Martineau
Part of the Furniture
OK, I decided that it was about time I truly wiped my sandpit RT-AC86U and ditched the v385.2 Alphas and reverted to v386.1I only have one client peer configured for the closest server peer. I rebooted the router in between tests. First I activated the wireguard client peer software from WireGuard and ran fast.com and speedtest.net. After reboot I've done the same thing but instead of the software client peer I ran 'wgstart client 1 policy' (pointing the the laptop). Again the same fast.com and speedtest.net.
I posted the results - they were very close between the 2 test sites.
EDIT: @Martineau, it looks like you're getting more than double the throughput on wg - good for you. Then I'll have to dig deeper at my end...
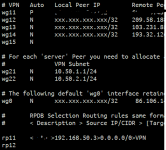
Only thing I installed was
S50wireguard from Github 'dev' branch.I reran the 500MB download again via the the same Mullvad New York Server.
Code:
./Speedtest.sh --big
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 500M 100 500M 0 0 1140k 0 0:07:28 0:07:28 --:--:-- 1619k
Code:
wgshow
(S50wireguard): 17648 v1.12b WireGuard VPN Peer Status check.....
interface: wg11 ('client' # Mullvad USA, New York)
public key: BAM+9SUqhEAYgzFUbaYnL5jKK9h1jzpwadGH7G4Z3U4=
private key: (hidden)
listening port: 58807
peer: ru9aQRxYBkK5pWvNkdFlCR8VMPSqcEENBPGkIGEN0XU=
endpoint: 86.106.143.93:51820
allowed ips: 0.0.0.0/0
latest handshake: 1 minute, 20 seconds ago
transfer: 572.50 MiB received, 30.99 MiB sent
persistent keepalive: every 25 secondsDuration
0:07:28 @Avg 1140k vs last night's 0:14:20 @Avg 595kUndoubtedly not a scientific approach and probably doesn't raise your spirits with your current quest for a resolution, but for me
WireGuard is now within 95% of my ISP WAN Speed!I'll start adding back all the other stuff to see if there is a point where the throughput dramatically drops back to its former paltry level.