outlaw78
Regular Contributor
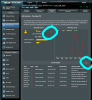
Checked my Asus router this morning and found this in its AiProtection section under Two Way IPS. Says they are out of Germany. The hits came in last night but this router has been "up" for days with no other hits.
What would cause this? Is it a bot sniffing out IP's or could an infected device be sending out my IP address? None of the other sections showed any alerts (like an infected device). I changed my external IP address since then.

What would cause this? Is it a bot sniffing out IP's or could an infected device be sending out my IP address? None of the other sections showed any alerts (like an infected device). I changed my external IP address since then.