scotty
Senior Member
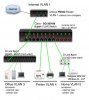
I have a quick question regarding the setup in this article. I ask because I might have to set up this very same setup for a friend's office (shared office). I've done lots of VLAN'ing on bigger Cisco switches and routers, but not much on the Linksys type equipment. My question is essentially about the 'general' port mode offered in the SRW-2008.
The Cisco mentality is that you have trunk ports or access ports. Trunks use .1Q (or ISL) tagging, whereas access ports don't, and can only be a member of 1 VLAN. Normally, you would only have each port (which a device plugs into) as a member of 1 VLAN, and then set up a trunk port to a .1Q aware router, or on a Cisco-type device set up with sub-interfaces and do a Router on a Stick setup.
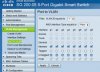
What I don't get with the article is the "general" mode that gets used, and how it seems to get away with both. It seems as though you can assign multiple VLANs to a port without needing .1Q encapsulation aware devices on the other end. I'm just wondering how this 'general' mode works. Is this all just a function of the switch being used (SRW-2008) and it being 'smart' enough to only transmit frames on ports which it knows are a member of the VLAN.
I've asked a couple higher-end Cisco guys I know and unfortunately they only know how to do it on Cisco devices (ROAS). With this port mode, do you also need a 1Q aware router?
The Cisco mentality is that you have trunk ports or access ports. Trunks use .1Q (or ISL) tagging, whereas access ports don't, and can only be a member of 1 VLAN. Normally, you would only have each port (which a device plugs into) as a member of 1 VLAN, and then set up a trunk port to a .1Q aware router, or on a Cisco-type device set up with sub-interfaces and do a Router on a Stick setup.
What I don't get with the article is the "general" mode that gets used, and how it seems to get away with both. It seems as though you can assign multiple VLANs to a port without needing .1Q encapsulation aware devices on the other end. I'm just wondering how this 'general' mode works. Is this all just a function of the switch being used (SRW-2008) and it being 'smart' enough to only transmit frames on ports which it knows are a member of the VLAN.
I've asked a couple higher-end Cisco guys I know and unfortunately they only know how to do it on Cisco devices (ROAS). With this port mode, do you also need a 1Q aware router?