Does that need to run in a loop? Or just spit out one random number per invocation?
If the output is in the range of 1-6, do you need 3 bytes? or is 1 byte sufficient? 1 byte gives output in the decimal range of 0-255. Skew isn't a problem, see below.
As for the seed, "openssl rand" will automatically create a ".rnd" file in the home directory. Might not be there on the script's first run after (re)boot, but if the file is there, it will automatically be used as a seed. If one was concerned about that, they could just create that seed file from the init-start script, with something like "head -c 512 /dev/urandom > /root/.rnd", or even better, "openssl rand 1 > /dev/random".
Here's what I've got...
In practice, the "skew" isn't a problem. I collected output from 64,200 invocations of that script (directly above, run on an AC68U) and here's the distribution of the output:
But... If you really want to convert raw data into numeric strings, here's an ugly and inefficient way to do it:
The two biggest problems with that, are (1) there's no guarantee that the output will contain any numbers, and (2) you're consuming a lot more entropy than needed. You could also wind up with a number that's 100 digits long. An improvement would be something like this:
That hashes one byte of random (raw) data (0-127 range, in decimal), then converts the first hexadecimal character (any character of the hash would work; each hexadecimal character is 6 bits, or 0-31, in decimal) of the hexadecimal hash into a random decimal number in the 0-15 range. If you want larger random numbers, just make sure that what's read from urandom and the hashed bytes that are converted into a decimal output are both scaled up proportionately.
Just some ideas, but yeah, I think "openssl rand" is your best bet.
If the output is in the range of 1-6, do you need 3 bytes? or is 1 byte sufficient? 1 byte gives output in the decimal range of 0-255. Skew isn't a problem, see below.
As for the seed, "openssl rand" will automatically create a ".rnd" file in the home directory. Might not be there on the script's first run after (re)boot, but if the file is there, it will automatically be used as a seed. If one was concerned about that, they could just create that seed file from the init-start script, with something like "head -c 512 /dev/urandom > /root/.rnd", or even better, "openssl rand 1 > /dev/random".
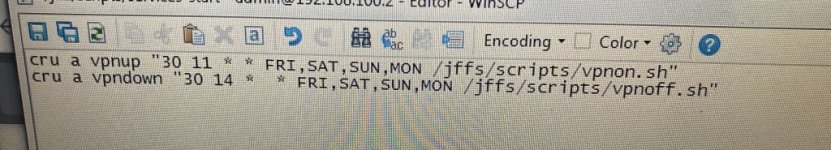
Here's what I've got...
Code:
#!/bin/sh
# Generate random numbers from BASE to BASE+N-1
N=6
BASE=1
#while [ '0' == ${?} ]
#do
RND=$(printf "%d" 0x$(openssl rand -hex 1))
RND2=$(( RND % N + BASE ))
echo $RND2
#doneIn practice, the "skew" isn't a problem. I collected output from 64,200 invocations of that script (directly above, run on an AC68U) and here's the distribution of the output:
Code:
10772 1
10762 2
10805 3
10726 4
10487 5
10648 6
Code:
head -c 100 /dev/urandom | tr -c -d '0-9'
Code:
printf "%d" 0x$( head -c 1 /dev/urandom | openssl md5 | cut -c 10-11 )Just some ideas, but yeah, I think "openssl rand" is your best bet.
Last edited: