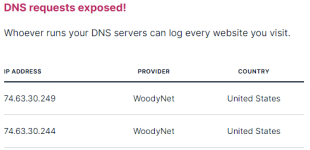
One potential reason for an ISP to want to intercept DNS queries is to redirect you to caching servers within their network for certain services like Netflix or Youtube. There are better ways to do that (through EDNS extensions and partnering with those providers), but that's one lazy way to do it.
Some providers also want to provide you with a generic error page when querying for a non-existent domain, so they want to point you to an internal server rather than the client getting an NXDOMAIN response. Yes, it's a completely stupid idea that breaks a lot of things such as spam control for mail servers, but quite a few ISPs experimented with that over the years.
Logging queries is unlikely to be a reason tho. They only need to monitor port 53 traffic to do that.
The main reason they do it here is for advertising revenue, the page you get with a list of search results when your lookup fails brings them revenue if you click one of those links (plus some revenue from the banner ads they show). Verizon lets you disable this behavior by pointing to DNS servers that are 1 IP up from the default ones you get assigned.. I've never seen an ISP actively intercept a DNS query to an outside server though. If Comcast is now actively intercepting queries to servers that aren't theirs, that's a new behavior. Not sure I'd be terribly concerned with it though, DNS queries are the least of our issues when it comes to privacy. As you say it could end up hurting you, if they are using their own DNS to make sure you use their local Netflix (and other) connections, those are the ones you want to be using, Netflix (and others) have direct 10G and 100G connections right into the major ISPs and they perform much better.
I did a ton of testing using a utility, I think it was DNSperf - and my ISPs servers were the fastest by far for cached domains (makes sense) and even for uncached they were either faster or equal, so I use theirs (the ones that don't redirect you on NXDOMAIN) with no encryption and no concerns.
If they are intercepting, would be curious (as a network guy) as to how they're doing it. Could be as simple as NAT'ing all traffic with UDP 53 destination to their own server IPs, or static destination NATs for all the common public DNS servers, etc. Seems anything more than that would require more significant investment, i.e. additional hardware etc, where NAT can be done right on their existing routers without issue, I'm sure they have plenty of memory and probably had the NAT timeout set fairly low. Since it is UDP traffic you can NAT the outbound query but not the inbound response (which is a totally separate connection) which would explain why OP is seeing the comcast servers responding rather than appearing to come from the outside server.
Not aware of anything in Cisco that would allow intercept and redirect like this other than NAT, however Juniper does have more features as far as basic firewall etc. Then again the Cisco ASRs have a lot more features than previous routers and I haven't played with them al. I believe Comcast uses both brands as do many network providers (including the one I work for) for redundancy (some sort of vulnerability or bug that takes down one brand will hopefully not impact the other). However our Cisco gear is far more reliable and less buggy than Juniper. Cost is a factor too, Juniper is about 1/2 the price.
Cisco has turned into a combination of HP (the switch or router price doesn't seem too bad until you start buying SFPs for it which are outrageous, similar to ink in HP printers) and Intel (many of their processors are actually the top of the line one with a bit of code that limits it to slower speeds, cheaper to just make one processor). Though Intel hasn't caught up to Cisco where you can just pay for a license to unlock the full speed/capability. Cisco calls it "performance license" or 'security license" if you want to utilize the onboard (but default disabled) hardware encryption module.
We buy SFPs from Cisco in batches of $1M and that gets us a 92% discount - what does that tell you about the actual cost of SFPs for them? List price for a 10G SFP is nearly the price of a nice 48 port Nexus switch, and a 100G SFP costs more than an ASR 9K router. Juniper just charges you a fraction of the amount regardless of how many you buy (with some small discounts for bulk orders).
/Tangent
/Tangent