skeal
Part of the Furniture
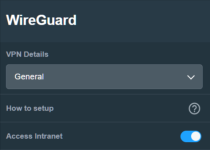
I have set up a Wireguard server on my AX88U. I selected the "Access Intranet" switch to on. I do not have intranet access, however. No router webui, nothing at all. Is there a temporary fix that can be used until Asus straightens this issue out? Like IP Tables or something, this is way above my paygrade. I have access to ssh and can follw instructions pretty well. Can anyone help, please?