You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
AdGuardHome [RELEASE] Asuswrt-Merlin-AdGuardHome-Installer (AMAGHI)
- Thread starter SomeWhereOverTheRainBow
- Start date
thelonelycoder
Part of the Furniture
As @SomeWhereOverTheRainBow said in his reply, I am the author of both amtm and Diversion. I coded Diversion long before amtm was born overnight. For simplicity, I added news and instructions to the diversion.ch website, rather than get it its own domain. Both scripts are hosted on that website.Sorry for asking a noob question. I am just starting on router based adblocker (from pihole). I was thinking of diversion, and on their website they show "What's new in amtm 3.2.3 - NEW: Adds support for Asuswrt-Merlin-AdGuardHome-Installer by SomeWhereOverTheRainBow". Its bit confusing give the first thread. As I understand this is new feature to amtm, and nothing to do with actual diversion codebase, right?
amtm is built into the router firmware since the release of Asuswrt-Merlin 384.15.
Kingp1n
Very Senior Member
I'm trying out adguardhome currently. It's pretty cool script. I've disabled Diverison currently to test it out.
If I use the built-in DoT settings within the router, do I need to also enable this as well under encryption settings inside AdguardHome website (192.168.1.1:12345/#encryption)?
Do I check the box that reads:
Enable encryption (HTTPS, DNS-over-HTTPS, and DNS-over-TLS)
If I use the built-in DoT settings within the router, do I need to also enable this as well under encryption settings inside AdguardHome website (192.168.1.1:12345/#encryption)?
Do I check the box that reads:
Enable encryption (HTTPS, DNS-over-HTTPS, and DNS-over-TLS)
SomeWhereOverTheRainBow
Part of the Furniture
Don't mess with the encryption page unless you are trying to host your own doh, DoT, or doQ server. To do such, you would need to run a ddns service and point adguardhome at the path of your letsencrypt cert and key. Also, you would need to runI'm trying out adguardhome currently. It's pretty cool script. I've disabled Diverison currently to test it out.
If I use the built-in DoT settings within the router, do I need to also enable this as well under encryption settings inside AdguardHome website (192.168.1.1:12345/#encryption)?
Do I check the box that reads:
Enable encryption (HTTPS, DNS-over-HTTPS, and DNS-over-TLS)
netstat -nlp | grep 443
To confirm you have all the ports available and not used. Obviously you would do the same for 853 and the DoQ port.
Not to forget to mention, you would also need to open those same ports on your firewall.
Last edited:
Kingp1n
Very Senior Member
I appreciate the response. I won't mess with none of that.
I did try these 2 commands to check adguard was running properly:
The 1st command return a number = gtg.
However, the 2nd check return this:
Everything seems to be running smoothly though.
I did try these 2 commands to check adguard was running properly:
Code:
pidof AdGuardHome
/opt/etc/init.d/AdGuardHome checkThe 1st command return a number = gtg.
However, the 2nd check return this:
Code:
admin@GT-AX11000-xxx0:/tmp/home/root# /opt/etc/init.d/AdGuardHome check
-sh: /opt/etc/init.d/AdGuardHome: not foundEverything seems to be running smoothly though.
SomeWhereOverTheRainBow
Part of the Furniture
If you want to change what dns servers you are using, in the first post I provided details of where to do thatI appreciate the response. I won't mess with none of that.
I did try these 2 commands to check adguard was running properly:
Code:pidof AdGuardHome /opt/etc/init.d/AdGuardHome check
The 1st command return a number = gtg.
However, the 2nd check return this:
Code:admin@GT-AX11000-xxx0:/tmp/home/root# /opt/etc/init.d/AdGuardHome check -sh: /opt/etc/init.d/AdGuardHome: not found
Everything seems to be running smoothly though.
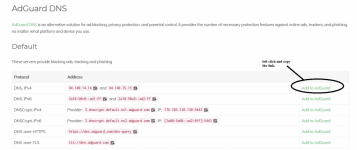
Here is a list of servers
Known DNS Providers | AdGuard DNS Knowledge Base
Here we suggest a list of trusted DNS providers. To use them, first install AdGuard Ad Blocker or AdGuard VPN on your device. Then, on the same device, click the link to a provider in this article
If you right click and copy the link provided by the webpage that says Add to AdGuard.
it will provide you with a sdns:// format that is easily portable to AdGuardHome upstream server section.
Example:
sdns://AgcAAAAAAAAAAAAPZG5zLmFkZ3VhcmQuY29tCi9kbnMtcXVlcnk
which is for AdGuards default DoH service.
Attachments
Last edited:
SomeWhereOverTheRainBow
Part of the Furniture
Refresh your page and take a look above, I updated it to be more detailed!I appreciate the response. I won't mess with none of that.
I did try these 2 commands to check adguard was running properly:
Code:pidof AdGuardHome /opt/etc/init.d/AdGuardHome check
The 1st command return a number = gtg.
However, the 2nd check return this:
Code:admin@GT-AX11000-xxx0:/tmp/home/root# /opt/etc/init.d/AdGuardHome check -sh: /opt/etc/init.d/AdGuardHome: not found
Everything seems to be running smoothly though.
SomeWhereOverTheRainBow
Part of the Furniture
The second check was missing an S61I appreciate the response. I won't mess with none of that.
I did try these 2 commands to check adguard was running properly:
Code:pidof AdGuardHome /opt/etc/init.d/AdGuardHome check
The 1st command return a number = gtg.
However, the 2nd check return this:
Code:admin@GT-AX11000-xxx0:/tmp/home/root# /opt/etc/init.d/AdGuardHome check -sh: /opt/etc/init.d/AdGuardHome: not found
Everything seems to be running smoothly though.
try running
Code:
/opt/etc/init.d/S61AdGuardHome checkKingp1n
Very Senior Member
Appreciate the assistance.The second check was missing an S61
try running
Code:/opt/etc/init.d/S61AdGuardHome check
I went back to use unbound and saw some tips on setting up unbound and adguard in some earlier post.
Does this look correct to setup in the Upstream DSN servers with unbound & adguard running together?
Code:
[/use-application-dns.net/]192.168.1.1:553
[/dns.resolver.arpa/]192.168.1.1:553
127.0.0.1:53535
tcp://127.0.0.1:53535This is what I'm getting when I run netstat -nlp | grep '53'
Code:
admin@GT-AX11000-xxx0:/tmp/home/root# netstat -nlp | grep '53'
tcp 0 0 127.0.0.1:553 0.0.0.0:* LISTEN 12523/dnsmasq
tcp 0 0 192.168.1.1:553 0.0.0.0:* LISTEN 12523/dnsmasq
tcp 0 0 127.0.0.1:47753 0.0.0.0:* LISTEN 3855/mcpd
tcp 0 0 0.0.0.0:3702 0.0.0.0:* LISTEN 12539/wsdd2
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 12024/unbound
tcp 0 0 127.0.0.1:53535 0.0.0.0:* LISTEN 12024/unbound
tcp 0 0 :::53 :::* LISTEN 4486/AdGuardHome
udp 0 0 127.0.0.1:553 0.0.0.0:* 12523/dnsmasq
udp 0 0 192.168.1.1:553 0.0.0.0:* 12523/dnsmasq
udp 0 0 0.0.0.0:3702 0.0.0.0:* 12539/wsdd2
udp 0 0 192.168.1.1:53923 0.0.0.0:* 12286/miniupnpd
udp 0 0 192.168.1.1:5351 0.0.0.0:* 12286/miniupnpd
udp 0 0 0.0.0.0:5353 0.0.0.0:* 10948/avahi-daemon:
udp 0 0 127.0.0.1:53535 0.0.0.0:* 12024/unbound
udp 0 0 :::53 :::* 4486/AdGuardHome
unix 2 [ ACC ] STREAM LISTENING 3553 1270/nt_actMail /var/run/nt_actMail_socketEverything seems to running smoothly, just let me know if the DNS upstream is gtg or if I need to make any changes. Sorry for the noob questions!
Last edited:
@SomeWhereOverTheRainBow One more issue I noticed. Before AdGuard, my local domain resolution was working with just hostnames. e.g. nslookup raspberrypi. But with AdGuarad it did not work.
I had to add my local domain in Upstream section (which you already add in Private reverse DNS servers section). So my current DNS setup is as below, which is providing valid local lookups.

Reading their documentations your implementation should have worked. Not sure if my network is any different since no one else have reported this issue.
Code:
$ nslookup
> raspberrypi
Server: 192.168.23.1
Address: 192.168.23.1#53
** server can't find raspberrypi: NXDOMAINI had to add my local domain in Upstream section (which you already add in Private reverse DNS servers section). So my current DNS setup is as below, which is providing valid local lookups.
Code:
$ nslookup
> raspberrypi
Server: 192.168.23.1
Address: 192.168.23.1#53
Name: raspberrypi.local
Address: 192.168.23.15Reading their documentations your implementation should have worked. Not sure if my network is any different since no one else have reported this issue.
SomeWhereOverTheRainBow
Part of the Furniture
That depends on your setup. I was able to use the current arpa just fine. Not everyone has .local at the end of their raspberripi.@SomeWhereOverTheRainBow One more issue I noticed. Before AdGuard, my local domain resolution was working with just hostnames. e.g. nslookup raspberrypi. But with AdGuarad it did not work.
Code:$ nslookup > raspberrypi Server: 192.168.23.1 Address: 192.168.23.1#53 ** server can't find raspberrypi: NXDOMAIN
I had to add my local domain in Upstream section (which you already add in Private reverse DNS servers section). So my current DNS setup is as below, which is providing valid local lookups.
View attachment 38450
Code:$ nslookup > raspberrypi Server: 192.168.23.1 Address: 192.168.23.1#53 Name: raspberrypi.local Address: 192.168.23.15
Reading their documentations your implementation should have worked. Not sure if my network is any different since no one else have reported this issue.
Mine is .mydomainname. If you want to resolve the issue, you need to set your routers domain to local, or modify your raspberrypi accordingly to your domain name.
At any rate you are using the wrong spot for defining a local request. It should be done in the Private reverse DNS servers. Using the upstream section has been known to break things at some point. AdGuardHome Devs only want you to use the upstream section if you are planning to send ALL your arpa. request to that. Otherwise you are leaking local client information to the upstream.
Last edited:
I already have it since very beginning, I didn't change that for adbloker. This along with installer adding the - '[/$DOMAIN/]$(nvram get lan_ipaddr):553'" \ part should cover my case, right?That depends on your setup. I was able to use the current arpa just fine. Not everyone has .local at the end of their raspberripi.
Mine is .mydomainname. If you want to resolve the issue, you need to set your routers domain to local, or modify your raspberrypi accordingly to your domain name.
At any rate you are using the wrong spot for defining a local request. It should be done in the Private reverse DNS servers. Using the upstream section has been known to break things at some point. AdGuardHome Devs only want you to use the upstream section if you are planning to send ALL your arpa. request to that. Otherwise you are leaking local client information to the upstream.
I beg to differ here.. Per their code, if a domain is specified (e.g. [/local/]192.168.23.1:553) then all requests for that domain should only go to that upstream, dnsmasq in this example. So I am not leaking local client info to any other upstream. Also the "Private reverse DNS servers" is section is kind of misnamed. Its used for PTR requests, which is more of dig than nslookup, right? I cam across https://github.com/AdguardTeam/AdGuardHome/issues/3028#issuecomment-830246459 which seems to agree with my reading. Any way I added two entries in upstream, and all my tasmota client who were configured to talk to my pi are happy. btw // has the special meaning of “unqualified names only”, i.e. names without any dots in them, like myhost or router.
[/local/]192.168.23.1:553
[//]192.168.23.1:553
Last edited:
SomeWhereOverTheRainBow
Part of the Furniture
I already have it since very beginning, I didn't change that for adbloker. This along with installer adding the - '[/$DOMAIN/]$(nvram get lan_ipaddr):553'" \ part should cover my case, right?
View attachment 38453
View attachment 38454
I beg to differ here.. Per their code, if a domain is specified (e.g. [/local/]192.168.23.1:553) then all requests for that domain should only go to that upstream, dnsmasq in this example. So I am not leaking local client info to any other upstream. Also the "Private reverse DNS servers" is section is kind of misnamed. Its used for PTR requests, which is more of dig than nslookup, right? I cam across https://github.com/AdguardTeam/AdGuardHome/issues/3028#issuecomment-830246459 which seems to agree with my reading. Any way I added two entries in upstream, and all my tasmota client who were configured to talk to my pi are happy. btw // has the special meaning of “unqualified names only”, i.e. names without any dots in them, like myhost or router.
[/local/]192.168.23.1:553
[//]192.168.23.1:553
After thoroughly reviewing, the issue lies more in their documentation then anything. I will push a patch.
Now all private domain request will be handled in the upstream section.
Last edited:
SomeWhereOverTheRainBow
Part of the Furniture
You can if you Iike to. The only differences are all the domain associations in the private dns section for moved from there to the upstream section while all the arpa. got left in the reverse dns section.Is it a good idea to fresh install adguard at every new update? Clear out any old setting? This seem to have work for me just incase come minor code change which need the old setting to clear out?
SomeWhereOverTheRainBow
Part of the Furniture
Scroll up your ssh terminal and screen shot, that is the best log as everything can be seen there.Clean install of 386.4, I ssh into the router and install EP and then AdBlock, but it just gets caught into a circle of installing. It clears the screen before I can grab the errors. Is there a place I can grab logs to show you guys?
It's clearing the screen or something, it looks like this. This is after installing it.Scroll up your ssh terminal and screen shot, that is the best log as everything can be seen there.
Attachments
SomeWhereOverTheRainBow
Part of the Furniture
Are you doing this from your phone or a computer?It's clearing the screen or something, it looks like this. This is after installing it.
Similar threads
- Replies
- 8
- Views
- 986
- Locked
AdGuardHome
AdGuardHome New Release's 2023
- Replies
- 288
- Views
- 34K
- Locked
- Replies
- 461
- Views
- 58K
- Replies
- 10
- Views
- 3K
- Replies
- 23
- Views
- 6K
Similar threads
Similar threads
-
-
DomainVPNRouting Domain VPN Routing v3.0.6 ***Release***
- Started by Ranger802004
- Replies: 73
-
amtm amtm 5.2 - the Asuswrt-Merlin Terminal Menu, February 09, 2025
- Started by thelonelycoder
- Replies: 142
-
Entware Possible to install jdownloader on asuswrt-merlin router with entware??
- Started by JeyJ
- Replies: 9
-
Skynet SOLVED: Scrollbar Disappears on Skynet Tab on Asuswrt-Merlin 386.14
- Started by WRobertE
- Replies: 10
-
-
ntpMerlin ntpMerlin compatibility with Merlin 3006.102.3
- Started by Ripshod
- Replies: 15
-
Asus ASUS RT-AX88U PRO AX6000, Merlin, Tailscale
- Started by Ratfink
- Replies: 0
-
Latest threads
-
-
Release ASUS RT-AX55 / RT-AX57 / RT-AX3000P Firmware version 3.0.0.4.386_53119 (2025/04/01)
- Started by fruitcornbread
- Replies: 0
-
-
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 1,406 (members: 12, guests: 1,394)