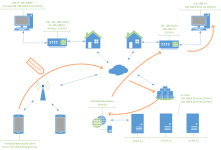
No additional iptables rules needed, unless your iptables' FORWARD chain is ended up with a drop rule.
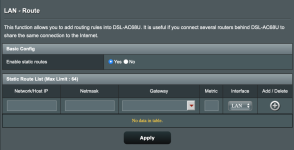
An ip route "192.168.1.0/24 to 172.30.55.44" is needed.
Thanks for such a quick reply!
"FORWARD CHAIN", does the #20 matter?
Chain FORWARD (policy DROP 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 457K 721M DOCKER-USER all -- * * 0.0.0.0/0 0.0.0.0/0
2 457K 721M DOCKER-ISOLATION-STAGE-1 all -- * * 0.0.0.0/0 0.0.0.0/0
3 185K 354M ACCEPT all -- * br-a6b4acbbfb2b 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
4 1050 61408 DOCKER all -- * br-a6b4acbbfb2b 0.0.0.0/0 0.0.0.0/0
5 271K 367M ACCEPT all -- br-a6b4acbbfb2b !br-a6b4acbbfb2b 0.0.0.0/0 0.0.0.0/0
6 0 0 ACCEPT all -- br-a6b4acbbfb2b br-a6b4acbbfb2b 0.0.0.0/0 0.0.0.0/0
7 0 0 ACCEPT all -- * docker0 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
8 0 0 DOCKER all -- * docker0 0.0.0.0/0 0.0.0.0/0
9 0 0 ACCEPT all -- docker0 !docker0 0.0.0.0/0 0.0.0.0/0
10 0 0 ACCEPT all -- docker0 docker0 0.0.0.0/0 0.0.0.0/0
11 0 0 ACCEPT all -- * docker_gwbridge 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
12 0 0 DOCKER all -- * docker_gwbridge 0.0.0.0/0 0.0.0.0/0
13 0 0 ACCEPT all -- docker_gwbridge !docker_gwbridge 0.0.0.0/0 0.0.0.0/0
14 67 3836 ufw-before-logging-forward all -- * * 0.0.0.0/0 0.0.0.0/0
15 67 3836 ufw-before-forward all -- * * 0.0.0.0/0 0.0.0.0/0
16 67 3836 ufw-after-forward all -- * * 0.0.0.0/0 0.0.0.0/0
17 67 3836 ufw-after-logging-forward all -- * * 0.0.0.0/0 0.0.0.0/0
18 67 3836 ufw-reject-forward all -- * * 0.0.0.0/0 0.0.0.0/0
19 67 3836 ufw-track-forward all -- * * 0.0.0.0/0 0.0.0.0/0
20 0 0 DROP all -- docker_gwbridge docker_gwbridge 0.0.0.0/0 0.0.0.0/0
sudo ip route add 192.168.1.0/24 via 172.30.55.44
ip route
...
192.168.1.0/24 via 172.30.55.44 dev ztMYSPECIFIC
...
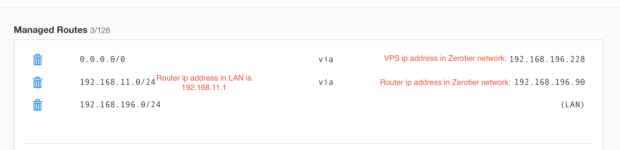
If you were talking about the zerotier WebUI console settings, leave it untouched.
YES, the zerotier WebUI->advanced->managed routes. leave it untouched, confirmed
You need to add a redirect rule(ipcidr) in your client App, let all 192.168.1.0/24 go through the proxy.
This is what I am confused about, what's
192.168.1.1 refer to in the IOS and
192.168.1.0/24 ip route in the VPS? My app is Shadowrocket, when I connect cellphone data with shadowrocket running, my 5G IP is 10.36.48.XXX, VPN IP 240.0.0.1/255.255.255.0 external IP 34.XX.XX.XX ---my VPS public IP/External IP.
Try to add a rule in Shadowrocket's config->rules->type: IP-CIDR, policy Proxy, No Resolve, IP-CIDR: 192.168.1.0/24, I can ping VPS zerotier IP and other devices' zerotier IP as well but cannot login my NAS and home router ac88u through WebUI...
At first, make sure you can access your VPS's zerotier address from your docker insurance(equals to SS-Server can reach zertier)
My VPS's zerotier IP is 172.30.165.217, how to check ss-server can reach it from docker?
docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
6754117xxxxx acrisliu/shadowsocks-libev:latest "/bin/sh -c 'exec ss…" 4 hours ago Up 4 hours 8388/tcp, 8388/udp, 0.0.0.0:9443->9443/tcp, 0.0.0.0:9443->9443/udp shadowsocks-libev