mekabe remain
Regular Contributor
Hi,
I am using the recent Merlin firmware on AC88U
I don't usually use the blocking feature for clients. Today I needed to use it.
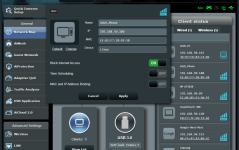
So from the mobile client I blocked internet for a client.
However, the client was still able to access internet.
Then I created a family member and added that device to that family member. Blocked the member.
But it was still accessing internet.
Basically block internet feature seems to be not working.
I have restarted the router and tried again but it did not help at all.
Since I am not using this feature frequently, I am not sure after which firmware update I lost this feature.
It might be in this condition with 386 release.
Any ideas ?
is this a known problem ?
I am using the recent Merlin firmware on AC88U
I don't usually use the blocking feature for clients. Today I needed to use it.
So from the mobile client I blocked internet for a client.
However, the client was still able to access internet.
Then I created a family member and added that device to that family member. Blocked the member.
But it was still accessing internet.
Basically block internet feature seems to be not working.
I have restarted the router and tried again but it did not help at all.
Since I am not using this feature frequently, I am not sure after which firmware update I lost this feature.
It might be in this condition with 386 release.
Any ideas ?
is this a known problem ?