Asuswrt Merlin: My working OpenVPN configuration for Bi-Directional VPN (router to router, between routers, site to site)
Acknowledgement: eibgard for helping me solve dns issues (Asuswrt Merlin, resolve client lan names on server-side? | SmallNetBuilder Forums (snbforums.com))
Update 2022-03-08: added pic of Server DDNS Host Name setting
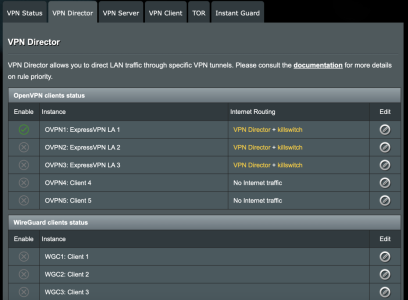
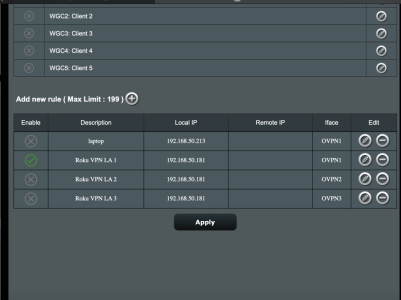
Update 2022-02-20: Added configuration for Client router with VPN Director (post #4)
Below is my working OpenVPN configuration for Bi-Directional VPN (router to router, between routers):
Attach are pics of configurations.
Routers: Asus RT-AC68U (Server), and RT-AC68U (Client)
Firmware: Asuswrt Merlin 386.4
Server LAN: 192.168.11.x
Server Domain Name: server.lan
Client LAN: 192.168.22.x
Client Domain Name: client.lan
0. Set Server "WAN - DDNS" Host Name, see pic
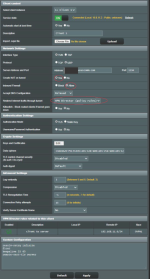
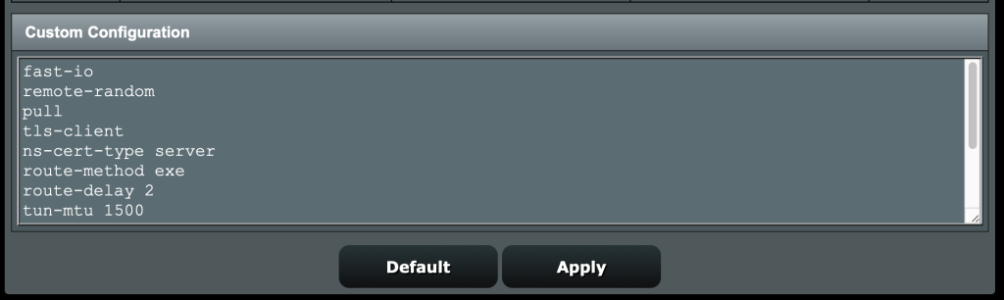
1. Config DNS on Server (dnsmasq.conf.add): pass dns request to vpn, and register Client dns for Client Domain Name, see pic.
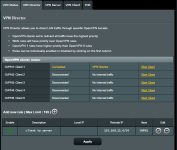
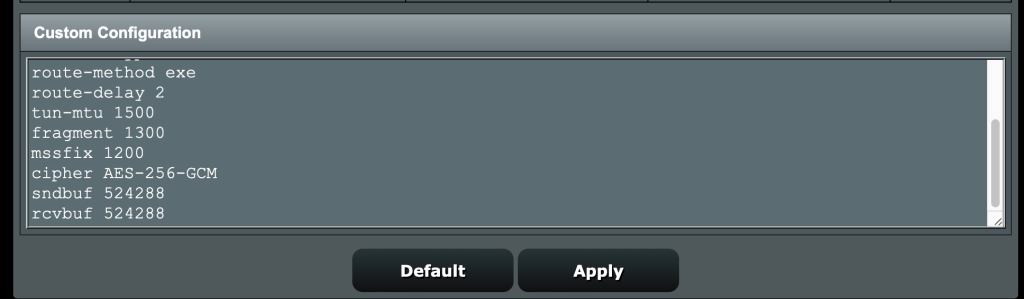
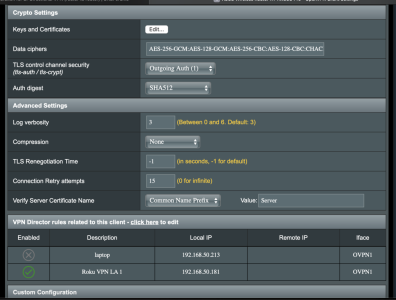
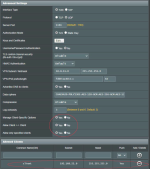
2. Config Server OpenVPN: The important configs (see pic) are
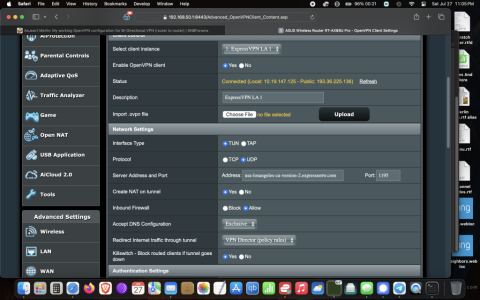
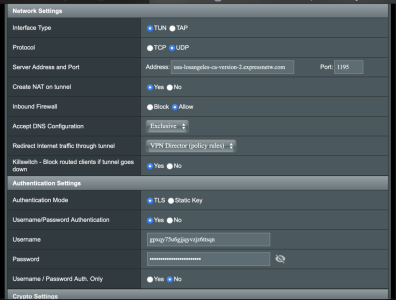
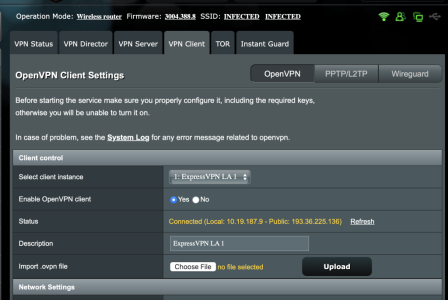
4. If the Client is using VPN Director, goto Post 4 below. If Client is not using VPN Director, then goto the “VPN Client” page, and make sure “Inbound Firewall” = allow, see pic in this post.
Hope this helps.
Acknowledgement: eibgard for helping me solve dns issues (Asuswrt Merlin, resolve client lan names on server-side? | SmallNetBuilder Forums (snbforums.com))
Update 2022-03-08: added pic of Server DDNS Host Name setting
Update 2022-02-20: Added configuration for Client router with VPN Director (post #4)
Below is my working OpenVPN configuration for Bi-Directional VPN (router to router, between routers):
Attach are pics of configurations.
Routers: Asus RT-AC68U (Server), and RT-AC68U (Client)
Firmware: Asuswrt Merlin 386.4
Server LAN: 192.168.11.x
Server Domain Name: server.lan
Client LAN: 192.168.22.x
Client Domain Name: client.lan
0. Set Server "WAN - DDNS" Host Name, see pic
1. Config DNS on Server (dnsmasq.conf.add): pass dns request to vpn, and register Client dns for Client Domain Name, see pic.
2. Config Server OpenVPN: The important configs (see pic) are
a. Manage Client-Specific Options
b. Allow Client<->Client
c. Allow only specified clients
d. Allowed Clients
i. “Common Name(CN)” = client
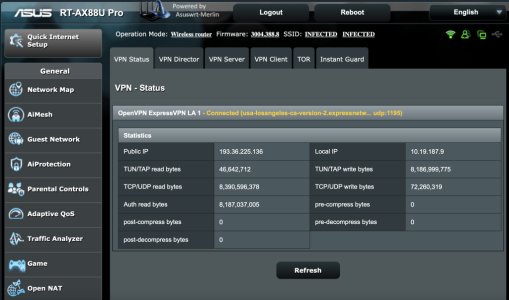
ii. “client” is from “VPN – Status” page when Client connects. You can confirm this when the Client connects to the Server
3. “Export OpenVPN configuration file” (.ovpn) on Server and “Import .ovpn file” on to Client4. If the Client is using VPN Director, goto Post 4 below. If Client is not using VPN Director, then goto the “VPN Client” page, and make sure “Inbound Firewall” = allow, see pic in this post.
Hope this helps.
Attachments
-
 20-20220129 OpenVPN Server-Advance-Good.png265.9 KB · Views: 768
20-20220129 OpenVPN Server-Advance-Good.png265.9 KB · Views: 768 -
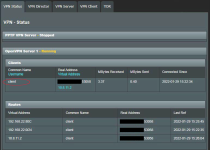 30-20220129 OpenVPN Server-Status_Redacted.png189.2 KB · Views: 739
30-20220129 OpenVPN Server-Status_Redacted.png189.2 KB · Views: 739 -
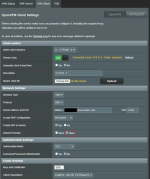 40-20220129 OpenVPN Client_Redacted-smaller.png294.4 KB · Views: 649
40-20220129 OpenVPN Client_Redacted-smaller.png294.4 KB · Views: 649 -
 10-20220129 OpenVPN - dnsmasq.conf.add_Redacted.png19.1 KB · Views: 578
10-20220129 OpenVPN - dnsmasq.conf.add_Redacted.png19.1 KB · Views: 578 -
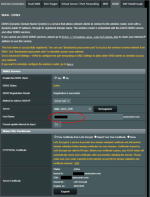 20220307 DDNS_HostName_Redacted.png403.9 KB · Views: 637
20220307 DDNS_HostName_Redacted.png403.9 KB · Views: 637
Last edited: