Wallifur
New Around Here
I set up WireGuard VPN server on the router but encountered a few issues that I thought @RMerlin might care about:
Thanks for all your good work. It's breathed a bit more life into my aging hardware, and it was great not having to reconfigure everything when switching to your firmware.
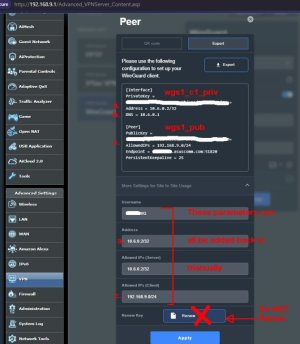
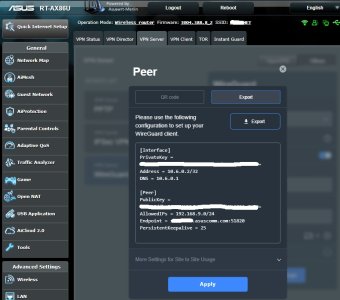
- I changed the VPN subnet to a /24 in the 172.16.0.0/12 range, as it's visually distinct from those I typically connect to in 10.0.0.0/8 and 192.168.0.0/16. However, when adding a client peer, the suggested settings for addresses use values from the default 10.6.0.0/24 range, which are both incorrect and hidden in that expando. It would be great if the values were derived from the main subnet setting.
- When adding a client peer, I saw no option to enter my own public key. I assume this means peers' private keys are always stored on the router, which somewhat defeats the purpose of public key cryptography. I understand the convenience, but ideally it would generate peer keys only if not provided, and remain editable after that anyway.
- Under the server's Advanced Settings, the text of the server's public key is unselectable. The private key is, too, but that's usually not needed. On desktop it can at least be copied using a browser's dev tools, on mobile it's basically impossible.
Thanks for all your good work. It's breathed a bit more life into my aging hardware, and it was great not having to reconfigure everything when switching to your firmware.