First of all, here is my current spec.
AX86U running on 3004.388.8_4
YazFi v4.4.4
I know by default Yazfi is not working with Wireguard because of its firewall rules.
After doing extensive search, I found I can make custom firewall rules for Yazfi to work with Wireguard.
I tried but it still didn't work.
Since I'm not familiar with Linux commands, can anyone help me take a look if there is anything wrong on each command?
Here are the steps I tried to make wgc1 to work with Guest Network 1.
1. open a script
2. type the following into the script and save
3. make the script executable
4. execute the script
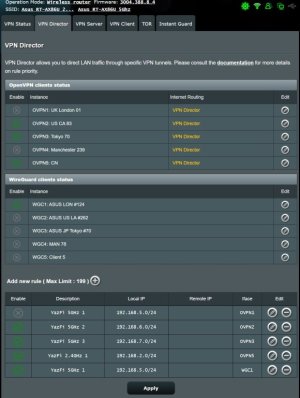
5. Add rule in VPN Director to direct traffic from 192.168.5.0/24 to wgc1 (see the attached pic)
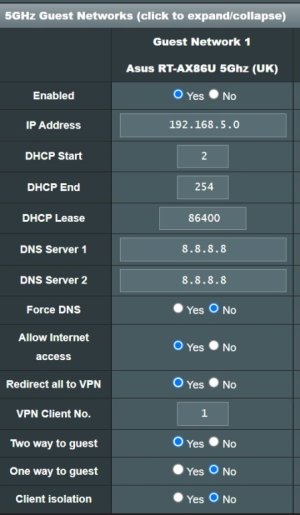
These are the steps I tried, but I'm still unable to connect to the internet by using the SSID of Guest Network 1.
AX86U running on 3004.388.8_4
YazFi v4.4.4
I know by default Yazfi is not working with Wireguard because of its firewall rules.
After doing extensive search, I found I can make custom firewall rules for Yazfi to work with Wireguard.
I tried but it still didn't work.
Since I'm not familiar with Linux commands, can anyone help me take a look if there is anything wrong on each command?
Here are the steps I tried to make wgc1 to work with Guest Network 1.
1. open a script
Code:
nano /jffs/addons/YazFi.d/userscripts.d/wg-yazfi.sh2. type the following into the script and save
Code:
#!/bin/sh
iptables -I YazFiFORWARD -i wl1.1 -o wgc1 -j ACCEPT
iptables -I YazFiFORWARD -i wgc1 -o wl1.1 -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -I YazFiINPUT -i wl1.1 -j ACCEPT3. make the script executable
Code:
chmod +x /jffs/addons/YazFi.d/userscripts.d/wg-yazfi.sh4. execute the script
Code:
/jffs/addons/YazFi.d/userscripts.d/wg-yazfi.sh5. Add rule in VPN Director to direct traffic from 192.168.5.0/24 to wgc1 (see the attached pic)


These are the steps I tried, but I'm still unable to connect to the internet by using the SSID of Guest Network 1.

