Voxel Custom firmware build for R7800 v. 1.0.2.86SF
- Thread starter Voxel
- Start date
kokishin
Regular Contributor
I realize that the following is not related to 86SF. I posted here because most of the really smart guys will be monitoring this thread.
Since 7-01-2021 1:55am PT, my 7800 has been bombarded with a probe on port 80 from the same source or slight variants on the ip address.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 01:55:19
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 02:02:42
.
.
.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.83, port 80, Monday, July 05, 2021 08:03:29
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.113, port 80, Monday, July 05, 2021 08:04:00
I ran Speedtest in the 7800 QOS page and their constant probing doesn't seem to be affecting my router speed. I'm just getting more log reports emailed to me by the 7800 since their constant probes keep filling the log buffer more quickly than usual.
I suppose I can uncheck Known "DoS attacks and Port Scans" to alleviate the logging but their constant probing has got my attention so I want to leave it checked.
Thoughts?

Since 7-01-2021 1:55am PT, my 7800 has been bombarded with a probe on port 80 from the same source or slight variants on the ip address.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 01:55:19
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 02:02:42
.
.
.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.83, port 80, Monday, July 05, 2021 08:03:29
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.113, port 80, Monday, July 05, 2021 08:04:00
I ran Speedtest in the 7800 QOS page and their constant probing doesn't seem to be affecting my router speed. I'm just getting more log reports emailed to me by the 7800 since their constant probes keep filling the log buffer more quickly than usual.
I suppose I can uncheck Known "DoS attacks and Port Scans" to alleviate the logging but their constant probing has got my attention so I want to leave it checked.
Thoughts?
Last edited:
SteevieWeevie
Occasional Visitor
Updated without issue yesterday. Smooth running. Thank you Voxel as always.
HELLO_wORLD
Very Senior Member
You can blocklist it with aegisI realize that the following is not related to 86SF. I posted heer because most of the really smart guys will be monitoring this thread.
Since 7-01-2021 1:55am PT, my 7800 has been bombarded with a probe on port 80 from the same source or slight variants on the ip address.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 01:55:19
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 02:02:42
.
.
.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.83, port 80, Monday, July 05, 2021 08:03:29
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.113, port 80, Monday, July 05, 2021 08:04:00
I ran Speedtest in the 7800 QOS page and their constant probing doesn't seem to be affecting my router speed. I'm just getting more log reports emailed to me by the 7800 since their constant probes keep filling the log buffer more quickly than usual.
I suppose I can uncheck Known "DoS attacks and Port Scans" to alleviate the logging but their constant probing has got my attention so I want to leave it checked.
Thoughts?
View attachment 34807
Alrighty I'm back again. Are any of you using the device in AP mode or just router mode? In AP this thing seems to crash for no rhyme or reason, need to set up logging on it. The only Factory firmware I remember working in AP mode was around 68. Anyone else having ap mode issues with this device
Might just be time for a network overhaul.
Might just be time for a network overhaul.
SwampKracker
Senior Member
Alrighty I'm back again. Are any of you using the device in AP mode or just router mode? In AP this thing seems to crash for no rhyme or reason, need to set up logging on it. The only Factory firmware I remember working in AP mode was around 68. Anyone else having ap mode issues with this device
Might just be time for a network overhaul.
AP mode works perfectly.
Alrighty I'm back again. Are any of you using the device in AP mode or just router mode? In AP this thing seems to crash for no rhyme or reason, need to set up logging on it. The only Factory firmware I remember working in AP mode was around 68. Anyone else having ap mode issues with this device
Might just be time for a network overhaul.
Both my R7800s are running .86SF as APs, no issues whatsoever.
I would recommend flashing to NG .82 stock, doing a factory reset, then flashing back to .86SF and doing a factory reset again and then configuring it from scratch.
kokishin
Regular Contributor
Thanks! I wasn't familiar with Aegis until you referred me to it. Need to come up to speed on it and implement it on my 7800.You can blocklist it with aegis
Just so I understand better... the 7800 implements it's own firewall. Aegis is another firewall virtually in front of the 7800?
I'm starting to look at the Aegis 1.7.x thread and I saw Aegis on GitHub.
Last edited:
Unfortunately tried this. It is working fine right now after a crash last night. I ordered a ubiquiti AP to just get this thing stable before the gf kills me while trying to do her MS program lolBoth my R7800s are running .86SF as APs, no issues whatsoever.
I would recommend flashing to NG .82 stock, doing a factory reset, then flashing back to .86SF and doing a factory reset again and then configuring it from scratch.
R. Gerrits
Very Senior Member
the R7800 has a firewall that mostly only blocks inbound traffic, but blocks no outbound traffic. I.e. all devices on your network can connect to any destination on internet.Just so I understand better... the 7800 implements it's own firewall. Aegis is another firewall virtually in front of the 7800?
Aegis adds a rules to that firewall so that also a lot of outbound traffic is blocked, to addresses that are considered dangerous.
(so that your devices on your network for instance are less likely to download malware.)
HELLO_wORLD
Very Senior Member
Like @R. Gerrits said, it is using the existing built-in firewall and adds its own rules, using iptables and ipset. It uses lists (remote and local) to block all traffic from and to undesired IPs or IP ranges.Thanks! I wasn't familiar with Aegis until you referred me to it. Need to come up to speed on it and implement it on my 7800.
Just so I understand better... the 7800 implements it's own firewall. Aegis is another firewall virtually in front of the 7800?
I'm starting to look at the Aegis 1.7.x thread and I saw Aegis on GitHub.
The first post on the thread you found (Aegis 1.7.x) explains it, and points to the ReadMe on GitHub with instructions
kokishin
Regular Contributor
@HELLO_wORLDthe R7800 has a firewall that mostly only blocks inbound traffic, but blocks no outbound traffic. I.e. all devices on your network can connect to any destination on internet.
Aegis adds a rules to that firewall so that also a lot of outbound traffic is blocked, to addresses that are considered dangerous.
(so that your devices on your network for instance are less likely to download malware.)
Shields Up port test confirms that inbound probes are not being responded to. My 7800 ports are in stealth mode. The 7800 sees the port probe and logs it (but doesn't respond).
Will the 7800 still see and log the external port probes if I use Aegis to blacklist the external ip addresses that are firing off the port probes?
Last edited:
Soo even more interesting, the device only crashes when I spin up the gf's MacBook Pro. I'll have to see what the packet captures/logs say. I've already ordered a ubiquiti AP as I was tired of troubleshootingUnfortunately tried this. It is working fine right now after a crash last night. I ordered a ubiquiti AP to just get this thing stable before the gf kills me while trying to do her MS program lol
Last edited:
HELLO_wORLD
Very Senior Member
Yes, aegis is blocking after the routing process, so the router’s log still catches the external probe. Also, aegis has its own log and stats as well.@HELLO_wORLD
Shields Up port test confirms that inbound probes are not being responded to. My 7800 ports are in stealth mode. The 7800 sees the port probe and logs it (but doesn't respond).
Will the 7800 still see and log the external port probes if I use Aegis to blacklist the external ip addresses that are firing off the port probes?
Stealth mode is great and recommended, but it does not prevent :
1) any connection initiated from inside
2) if you have any open service to WAN, then undesired packets, even if not answered are still reaching the destination.
I realize that the following is not related to 86SF. I posted here because most of the really smart guys will be monitoring this thread.
Since 7-01-2021 1:55am PT, my 7800 has been bombarded with a probe on port 80 from the same source or slight variants on the ip address.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 01:55:19
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.75, port 80, Thursday, July 01, 2021 02:02:42
.
.
.
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.83, port 80, Monday, July 05, 2021 08:03:29
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.113, port 80, Monday, July 05, 2021 08:04:00
I ran Speedtest in the 7800 QOS page and their constant probing doesn't seem to be affecting my router speed. I'm just getting more log reports emailed to me by the 7800 since their constant probes keep filling the log buffer more quickly than usual.
I suppose I can uncheck Known "DoS attacks and Port Scans" to alleviate the logging but their constant probing has got my attention so I want to leave it checked.
Thoughts?
After reading your post, I checked my log and surprisingly I have them from that IP range.
Code:
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.217, port 80, Wednesday, July 07, 2021 20:36:52
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.81, port 80, Wednesday, July 07, 2021 20:32:24
[admin login] from source 192.168.87.8, Wednesday, July 07, 2021 20:32:01
[DoS Attack: SYN/ACK Scan] from source: 212.133.164.96, port 80, Wednesday, July 07, 2021 20:31:33I am still on .85, not sure if other people have the same problem.
kokishin
Regular Contributor
And the probe from 212.133.164.xxx is always to port 80. Consistent, persistent, and annoying.After reading your post, I checked my log and surprisingly I have them from that IP range.
Code:[DoS Attack: SYN/ACK Scan] from source: 212.133.164.217, port 80, Wednesday, July 07, 2021 20:36:52 [DoS Attack: SYN/ACK Scan] from source: 212.133.164.81, port 80, Wednesday, July 07, 2021 20:32:24 [admin login] from source 192.168.87.8, Wednesday, July 07, 2021 20:32:01 [DoS Attack: SYN/ACK Scan] from source: 212.133.164.96, port 80, Wednesday, July 07, 2021 20:31:33
I am still on .85, not sure if other people have the same problem.
HELLO_wORLD
Very Senior Member
In aegis, just add 212.133.164.0/24 in the custom global block list, and voilàAnd the probe from 212.133.164.xxx is always to port 80. Consistent, persistent, and annoying.
kokishin
Regular Contributor
Mrs K's work Thinkpad is connected to the Guest 5GHz wifi network to keep it private from our home network.
The DHCP renewal occurs every 15 minutes like clockwork.
I had another device connected to the Guest 2.4GHz wifi and DHCP renewal occurred every 15 minutes as well.
I suppose because it's the Guest network, DHCP renewal is more aggressive since I presume devices on the Guest network are considered to be temporary.
Besides 86SF, I noticed this behavior on prior releases.
Is there a way to increase the DHCP renewal time?
The DHCP renewal occurs every 15 minutes like clockwork.
I had another device connected to the Guest 2.4GHz wifi and DHCP renewal occurred every 15 minutes as well.
I suppose because it's the Guest network, DHCP renewal is more aggressive since I presume devices on the Guest network are considered to be temporary.
Besides 86SF, I noticed this behavior on prior releases.
Is there a way to increase the DHCP renewal time?
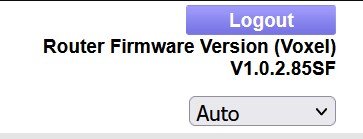
I just signed up for the forum and am a little confused. I've been running dd-wrt but wanted to try Voxel's firmware to see if the wireless was better. I thought I got the newest version V1.02.86SF installed but noticed there was nothing showing (Voxel) on the main screen like I'd seen in pictures so kept thinking I did something wrong.
I reverted to an older version 1.0.1... of the Netgear stock firmware then upgraded to 1.0.2.59S version of Voxel and it did show (Voxel) next to the version on the router screen. Finally I upgraded to the newest version of Voxel, 86SF, again and the name is gone. Did he remove his name next to the Version at some point?
I reverted to an older version 1.0.1... of the Netgear stock firmware then upgraded to 1.0.2.59S version of Voxel and it did show (Voxel) next to the version on the router screen. Finally I upgraded to the newest version of Voxel, 86SF, again and the name is gone. Did he remove his name next to the Version at some point?
I just signed up for the forum and am a little confused. I've been running dd-wrt but wanted to try Voxel's firmware to see if the wireless was better. I thought I got the newest version V1.02.86SF installed but noticed there was nothing showing (Voxel) on the main screen like I'd seen in pictures so kept thinking I did something wrong.
I reverted to an older version 1.0.1... of the Netgear stock firmware then upgraded to 1.0.2.59S version of Voxel and it did show (Voxel) next to the version on the router screen. Finally I upgraded to the newest version of Voxel, 86SF, again and the name is gone. Did he remove his name next to the Version at some point?
I can verify on V1.0.2.85SF the Voxel name is above the firmware version. Maybe you need to clear the cache on your web browser?
Attachments
Similar threads
- Replies
- 11
- Views
- 1K
- Replies
- 2
- Views
- 373
- Replies
- 1
- Views
- 305
- Replies
- 3
- Views
- 662
- Replies
- 12
- Views
- 1K
Similar threads
Similar threads
-
Voxel Custom firmware build for Orbi LBR20 v. 9.2.5.2.50SF-HW
- Started by Voxel
- Replies: 0
-
Voxel Custom firmware build for R9000/R8900 v. 1.0.4.81HF
- Started by Voxel
- Replies: 2
-
Voxel Custom firmware build for R7800 v. 1.0.2.115SF
- Started by Voxel
- Replies: 8
-
Voxel Custom firmware build for Orbi LBR20 v. 9.2.5.2.49SF-HW
- Started by Voxel
- Replies: 1
-
Voxel Custom firmware build for R9000/R8900 v. 1.0.4.80HF
- Started by Voxel
- Replies: 2
-
Voxel Custom firmware build for R7800 v. 1.0.2.114SF
- Started by Voxel
- Replies: 11
-
Voxel Custom firmware build for Orbi LBR20 v. 9.2.5.2.48SF-HW
- Started by Voxel
- Replies: 3
Latest threads
-
-
-
GT-BE98 - All 2.4ghz channels drop.
- Started by OfficerDoofy
- Replies: 14
-
FlexQoS FlexQoS 1.4.7 - Flexible QoS Enhancement Script for Adaptive QoS
- Started by ExtremeFiretop
- Replies: 0
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!