Hello,
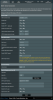
I've setup an OpenVPN Client on my router Asus RT-AC68U with Asuswrt-Merlin version 384.13_0 as follows:
Force Internet traffic through tunnel: Policy Rules (strict)
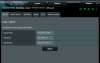
Rule: 192.168.24.0/24: VPN
Accept DNS Configuration: Exclusive
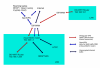
The VPN connection works fine but there is one problem:
not the DNS servers provied by the VPN tunnel but those from the WAN DNS Setting of the router are used.
I check the results on https://dnsleaktest.com
Could you please help to find the reason of this malfunction?
Best regards,
RKaniec
I've setup an OpenVPN Client on my router Asus RT-AC68U with Asuswrt-Merlin version 384.13_0 as follows:
Force Internet traffic through tunnel: Policy Rules (strict)
Rule: 192.168.24.0/24: VPN
Accept DNS Configuration: Exclusive
The VPN connection works fine but there is one problem:
not the DNS servers provied by the VPN tunnel but those from the WAN DNS Setting of the router are used.
I check the results on https://dnsleaktest.com
Could you please help to find the reason of this malfunction?
Best regards,
RKaniec