Okay
@john9527 , I took the time this evening to test the WAN over WAN DNS in OpenVPN client, and successfully, it broke again same as before

So with the settings as we discussed:
WAN DNS set to 192.168.1.2 (Pi-Hole)
DNSFilter rules deleted/disabled
OpenVPN client set to "Exclusive" with "WAN devices use WAN DNS"
3 x clients set to policy based routing over openvpn client with block internet if tunnel is down
This is the output after a reboot of the router:
ASUSWRT-Merlin RT-AC68U_3.0.0.4 Mon Jan 30 16:23:34 UTC 2017
myusername@RT-AC68P-3DFX:/tmp/home/root# iptables-save -t nat
# Generated by iptables-save v1.4.14 on Wed Feb 22 19:33:48 2017
*nat
: PREROUTING ACCEPT [630:47794]
: INPUT ACCEPT [224:19636]
: OUTPUT ACCEPT [89:13028]
: POSTROUTING ACCEPT [18:3443]
: DNSFILTER - [0:0]
: DNSVPN1 - [0:0]
: LOCALSRV - [0:0]
: VSERVER - [0:0]
: VUPNP - [0:0]
-A PREROUTING -d XXX.5XX.5XX.2XX/32 -j VSERVER
-A PREROUTING -i br0 -p udp -m udp --dport 53 -j DNSVPN1
-A PREROUTING -i br0 -p tcp -m tcp --dport 53 -j DNSVPN1
-A POSTROUTING -s 192.168.1.0/24 -o tun11 -j MASQUERADE
-A POSTROUTING ! -s XXX.5XX.5XX.2XX/32 -o eth0 -j MASQUERADE
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -o br0 -j MASQUERADE
-A DNSVPN1 -s 192.168.1.20/32 -j DNAT --to-destination 192.168.1.1
-A DNSVPN1 -s 192.168.1.21/32 -j DNAT --to-destination 192.168.1.1
-A DNSVPN1 -s 192.168.1.22/32 -j DNAT --to-destination 192.168.1.1
-A DNSVPN1 -j DNAT --to-destination 192.168.1.2
-A VSERVER -j VUPNP
-A VUPNP -p udp -m udp --dport 49574 -j DNAT --to-destination 192.168.1.181:49574
COMMIT
# Completed on Wed Feb 22 19:33:48 2017
myusername@RT-AC68P-3DFX:/tmp/home/root#
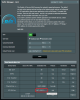
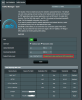
As well, a couple screenshots of the after affects to non - vpn devices (so WAN devices), after a reboot of the router and computer:
and of course