Hello all
I'm a networking novice looking to setup a VPN that allows me to securely access my local NAS over the WAN. I already have this running using PPTP. The router acts as the VPN server. As it is now, this provides the VPN client (Windows & Linux laptops) unrestricted access to my entire LAN. I want to limit this so VPN clients have access to nothing but the NAS. What is the most robust/secure way to do this?
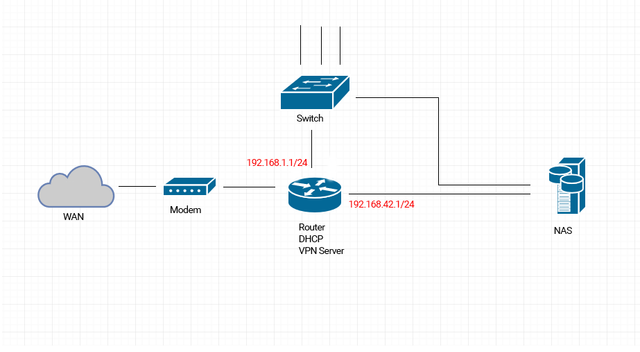
I'm thinking of creating two VLANs. Most of my LAN would run on VLAN1, but one RJ45 port on the router connected to the NAS would run on VLAN2. Looking at the OpenVPN configuration on my router, it looks like I could then switch from TUN to TAP and then bridge the OpenVPN server to VLAN2. I think that would achieve my goal
However:
Any pointers greatly appreciated!
I'm a networking novice looking to setup a VPN that allows me to securely access my local NAS over the WAN. I already have this running using PPTP. The router acts as the VPN server. As it is now, this provides the VPN client (Windows & Linux laptops) unrestricted access to my entire LAN. I want to limit this so VPN clients have access to nothing but the NAS. What is the most robust/secure way to do this?
I'm thinking of creating two VLANs. Most of my LAN would run on VLAN1, but one RJ45 port on the router connected to the NAS would run on VLAN2. Looking at the OpenVPN configuration on my router, it looks like I could then switch from TUN to TAP and then bridge the OpenVPN server to VLAN2. I think that would achieve my goal

However:
- Is this considered best practice, or are there more secure/robust approaches?
- Is there a way to achieve something similar without having to connect an additional ethernet cable (likely meaning without requiring VLAN2)?
- It seems bridging in this way is only possible using OpenVPN. At least in my router's VPN configuration UI, that briding option doesn't exist for PPTP or L2TP/IPSec. How would VPN systems not based on OpenVPN solve this?
Any pointers greatly appreciated!

