SomeWhereOverTheRainBow
Part of the Furniture
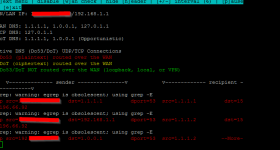
the router himself traffic?I have unbound and route it over vpn. It used to be all green. But few days ago I noticed a lot of red entry with my WAN as source. The recipient dst side still show my vpn ip though. Any idea what could possibly cause this?
View attachment 47830
are you routing the routers "own" local traffic thru the vpn? if not, then you will see its own dns traffic traveling via wan. Any clients not travelling VIA way of VPN will also use unbound through WAN typically, unless you define port 53 traffic from those clients to specifically traverse the VPN. This has one caveat, the rules would have to be defined before any other rules for those clients to ensure that specific traffic hits the vpn.