eibgrad
Part of the Furniture
Been following this thread. I recall many questions about leaving DNS Server 1/DNS Server 2 blank was answered moons ago. @RMerlin 's guidance was: "do not leave'm blank or NTP and other time dependent services (VPNs, ...) cannot start properly." What did I miss? We are concerned that the router is leading DNS for it's own functional purposes or the DNS of the clients or both?
View attachment 39415
As usual, it gets complicated.
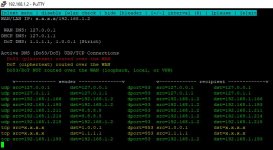
The point you missed is that we were talking about leaving them blank in a specific context, namely, when DoT is enabled on the WAN. When that happens, the WAN's DNS servers are updated to include Stubby (127.0.1.1). IOW, if you had 1.1.1.1 and 1.0.0.1 before DoT was enabled, either because of being set automatically or custom servers, it would now be 1.1.1.1, 1.0.0.1, 127.0.1.1 on the WAN. And that means that *any* of those DNS servers are equally available to the WAN for name resolution. But only 127.0.1.1 provides DNS leak protection.
The idea behind leaving the custom servers blank is to force the router to *always* use 127.0.1.1 (Stubby), since it now becomes the only option available. It's NOT to eliminate any and all DNS servers on the WAN, which would be the case if you did NOT use DoT.
Then @SomeWhereOverTheRainBow pointed out that this wasn't necessary if you set Tools > Other Settings > "Wan: Use local caching DNS server as system resolver (default: No)" to Yes, which started a whole other discussion.
Apparently at one time the WAN *was* configured by default to use DNSMasq (127.0.0.1). And if that was the case today, we wouldn't even be having this discussion. The router would be using Stubby exclusively, just like the WLAN/LAN clients. But that was changed quite some time ago to make sure the router always had valid DNS servers available on the WAN, since users were messing w/ it trying to implement their own DoT, long before it was a built-in feature. And then that Tools option was made available so users could go back to the old way of configuring the WAN if they explicitly chose to do so.
So @SomeWhereOverTheRainBow's recommendation ended up being the preferred means to ensure that the router only uses Stubby, since DNSMasq provides other benefits as well (local name resolution, caching, etc.).
So no matter which method you choose, blank custom servers or that Tools option, the WAN now only has a local reference, either directly to Stubby itself (127.0.1.1), OR, indirectly through DNSMasq (127.0.0.1), respectively. Take your pick.
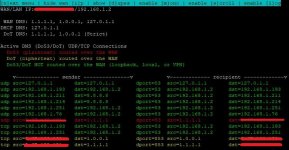
P.S. Here's the WAN configuration if you do nothing but enable DoT.
There are NO active WLAN/LAN clients at the time. Notice the DNS monitor is indicating that the DoT servers (127.0.1.1) are NOT being used. To the extent you believe this qualifies as a DNS leak (and that's certainly debatable), this is a problem.
Last edited: