Yota
Very Senior Member
Asus and Asuswrt-Merlin have introduced encrypted passwords since 3.0.0.4.384_81790 and 384.17 firmware, which I appreciate, but I messed up a few days ago.
I tried backing up all encrypted password hashes in nvram in ssh and re-writing to nvram, but I found that even though nvram didn't change anything, the GUI told me the password was wrong. because there are many important settings that are not backed up, I don't want to do a factory reset, so I tried looking for a solution, the good news is I found it.
Prerequisites:
You must be able to log into your router via SSH.
(For me I'm using
How to do:
1) Enter the following commands in SSH:
2) Now logging into the GUI with
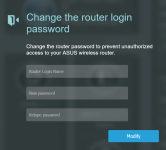
3) Congrats, you've unlocked your password without resetting the router
How it works:
I remember that when 378 or 380, asus introduced an initial setting check, when the default password is
So we just need to use SSH to write the plaintext
In short we are using one security feature to hack another security feature.
Note:
This method may not work for everyone because not everyone has SSH enabled and
Anyone is welcome to copy this thread to the wiki.
I tried backing up all encrypted password hashes in nvram in ssh and re-writing to nvram, but I found that even though nvram didn't change anything, the GUI told me the password was wrong. because there are many important settings that are not backed up, I don't want to do a factory reset, so I tried looking for a solution, the good news is I found it.
Prerequisites:
You must be able to log into your router via SSH.
(For me I'm using
Authorized Keys so I can still log in even if the GUI password is incorrect)How to do:
1) Enter the following commands in SSH:
Code:
nvram set http_passwd=admin
nvram commitadmin as the password should ask you to reset the password (Or just open: http://192.168.50.1/Main_Password.asp )
3) Congrats, you've unlocked your password without resetting the router
How it works:
I remember that when 378 or 380, asus introduced an initial setting check, when the default password is
admin, it will enter an interface and ask to change the password before continuing to enter the GUI, This is a security feature to make sure no one uses admin as the password.So we just need to use SSH to write the plaintext
admin password to nvram, we can trigger the interface to reset the password, and when we reset the password, we can enter the GUI.In short we are using one security feature to hack another security feature.
Note:
This method may not work for everyone because not everyone has SSH enabled and
Authorized Keys set. So when there is no way to log into the router via SSH, the only way is to do a factory reset.Anyone is welcome to copy this thread to the wiki.
Last edited:

