Hello !
I am trying to configure this simple network:
modem (WAN: 192.168.1.1) -- router – (192.168.2.1/24) LAN
I am going to purchase as a router the
ASUS RT-AC52U with the stock updated firmware ASUSWRT.
My first problem is that I would like to run simultaneously the VPN server (OpenVPN) and VPN client in the
same router (ASUS RT-AC52U).
The LAN consists of several PCS, a smart TV, some Android devices and a IP camera.
Edit: My IP camera (Amcrest ProHD 3MP Wi-Fi Camera (
IP3M-941W) is
not cloud reliant, but has the option of local storage (microSD card, NAS et) for security reasons, according to the recommendations of this
excellent site!
The main reason I need a VPN tunnel is the IP camera.
I think that for my security reasons the IP camera will have access to the LAN and the WAN only through a VPN tunnel, as a VPN client running in ASUS RT-AC52U router. I would like to have access to my IP camera from PCs and Android devices on the same LAN as well as from PCs and Android devices remotely, through a VPN tunnel in all cases. All these PCs and Android devices must have access to LAN while using the VPN tunnel. In general, I would like make
selective routing, in order to select which devices will use the VPN and which devices will go directly to the internet. That is my
second problem.
In order to find a solution to my
first problem, I think that I have to follow
this tip :
I would assume the VPN client service is using 1194 the default port and your server by default is set to the same. You need to change the VPN server port # and regenerate a new OVPN file for the remote user to connect the server. Then you will be able to run the VPN client service and the VPN server at the same time.
I also have to ensure the VPN server and client are on separate subnets (but I don’t know how to do that)!!! Any ideas ? Perhaps the solution is the
static routing as proposed
here (point 1.5), according to the
proposal 2 of this post ! In this case
FritzBox LAN port IP : 192.168.50.1
Asus WAN port IP : 192.168.50.2
Asus LAN IP : 192.168.51.1
In order to find a solution to my
second problem, I think that I have to make the following settings (main source is
this post):
ASUSWRT: Push LAN to clients: enabled
ASUSWRT: Redirect Internet Traffic: disabled
ASUSWRT: Respond to DNS: enabled
ASUSWRT: Advertise DNS to clients: enabled
Windows 10 PC clients: disable the Use Default Gateway on Remote Network setting in the VPN dial-up connection item on the client computer:
In Windows 10 go to Settings > Network and Internet. Select 'Ethernet' on the left and then click 'Change Adapter Options'. VPN's properties? (TCP/IPv4 > Properties > Advanced).
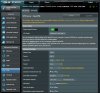
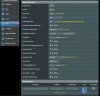
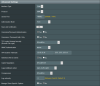
I don’t know how to make the selective routing with the stock firmware ASUSWRT, perhaps as pointed at this
video tutorial. I haven’t bought the ASUS RT-AC52U yet, but the firmware (two screenshots included) of my currently using elsewhere ASUS RT-AC51U seems slightly different and I don’t know how to configure ! Any help?
Another possible solution would be to follow the
proposal 1 of this post ! In this case, I could
flip devices between normal local country ISP or the VPN client network so I can surf privately or access other country content via VPN service. So I would manually switch my devices between the 2 wireless networks
Thank you in advance,
Dimi