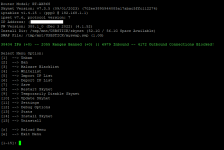
@SomeWhereOverTheRainBow
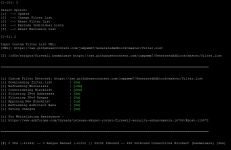
Screenshot 1 is your list - 0 ranges banned
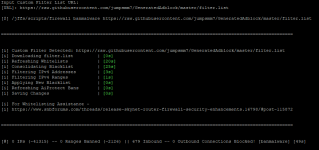
Screenshot 2 is Skynet default - 2055 ranges banned
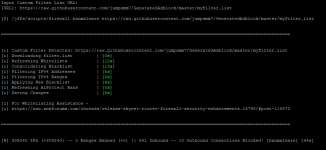
Okay so using the first link, i am not sure why there are no ranges since it would be pulling the lists straight from the sources like skynet default does:
as you can see, there is not that much difference between the default, versus mine:
in fact I include all the lists that are in skynet default. So it should be banning those "ranges" still.
@SomeWhereOverTheRainBow
Thanks!
This link is working again, but is not blocking any ranges. It's blocking ~200.000 IPs, but no ranges.
The second link is also blocking about 400.000 IPs but no ranges.
Some time ago, your filter list also included ranges.
The question begs to ask why is skynet doing this incorrectly in some instances?
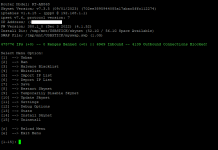
Let us look at what skynet code defines to be a "range"-
This is User added ranges (added by skynet menu option for ranges):
This is ranges blocked by blocking countries:
This is ranges blocked by blocking VIA "ASN" codes
@Adamm- "Why are when users load a custom filter.list, their user defined ranges are not included in the iptable rules; however, when they use the default filter lists their user defined ranges are included in the iptable rules?"
Basically
@Ubimo has pointed out when they load a custom filter.list, not much different from the default, there are no longer any ranges showing up as being banned in the statistic ( which implies the skynet-banned ranges rules are not getting loaded when switching to custom filter.list option). However, when they switch back to default filter.list, their banned ranges are once again included in the statistics (which implies skynet-banned ranges are once again loaded properly into the iptable ruleset).
@Ubimo
In the code link below, I see reference to using the custom list with the banmalware option. Possibly different steps are taking if "fast-switch" is enabled in diversion or skynet. Maybe this is causing the skipping of adding ranges when using custom filter lists? But I don't know
@Adamm script well enough yet to tell you.
more specifically, this line:
@Ubimo
A temporary solution is to manually restart skynet after switching to custom filter lists and your "blocked ranges" should hopefully be added back. (banned ranges = ranges you have added, any countries you block, and any ASN codes you block, and anything that gets added with a subnet attached like /24 at the end of the ipaddress).
Code:
( firewall ban range 8.8.8.8/24 "Apples" ) This Bans the CIDR Block Specified With The Comment Apples
( firewall ban country "pk cn sa" ) This Bans The Known IPs For The Specified Countries (Accepts Single/Multiple Inputs If Quoted) https://www.ipdeny.com/ipblocks/
( firewall ban asn AS123456 ) This Bans the ASN Specified
@Ubimo
If the custom filter list were loading correctly, here would be the amount of banned IPS ranges contributed.
Code:
curl -fsL --retry 3 --connect-timeout 3 "https://raw.githubusercontent.com/jumpsmm7/GeneratedAdblock/master/filter.list" | awk -F/ '{print $0}' | xargs "curl" -fsSL | grep -E '^(([0-9]{1,3}\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$' | grep -vE '^(0\.|10\.|100\.(6[4-9]|[7-9][0-9]|1[0-1][0-9]|12[0-7])\.|127\.|169\.254\.|172\.1[6-9]\.|172\.2[0-9]\.|172\.3[0-1]\.|192\.0\.0\.|192\.0\.2\.|192\.168\.|198\.(1[8-9])\.|198\.51\.100\.|203\.0\.113\.|2(2[4-9]|[3-4][0-9]|5[0-5])\.|8\.8\.8\.8|8\.8\.4\.4|1\.1\.1\.1|1\.0\.0\.1)' | awk '!x[$0]++' | grep -F "/" | wc -l
9230
IP from non-Ranges:
Code:
curl -fsL --retry 3 --connect-timeout 3 "https://raw.githubusercontent.com/jumpsmm7/GeneratedAdblock/master/filter.list" | awk -F/ '{print $0}' | xargs "curl" -fsSL | grep -E '^(([0-9]{1,3}\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$' | grep -vE '^(0\.|10\.|100\.(6[4-9]|[7-9][0-9]|1[0-1][0-9]|12[0-7])\.|127\.|169\.254\.|172\.1[6-9]\.|172\.2[0-9]\.|172\.3[0-1]\.|192\.0\.0\.|192\.0\.2\.|192\.168\.|198\.(1[8-9])\.|198\.51\.100\.|203\.0\.113\.|2(2[4-9]|[3-4][0-9]|5[0-5])\.|8\.8\.8\.8|8\.8\.4\.4|1\.1\.1\.1|1\.0\.0\.1)' | awk '!x[$0]++' | grep -vF "/" | wc -l
334724
If my custom list was loaded correctly here would be the amount of banned IPS ranges it contributed.
Code:
curl -fsL --retry 3 --connect-timeout 3 "https://raw.githubusercontent.com/jumpsmm7/GeneratedAdblock/master/myfilter.list" | awk -F/ '{print $0}' | xargs "curl" -fsSL | grep -E '^(([0-9]{1,3}\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$' | grep -vE '^(0\.|10\.|100\.(6[4-9]|[7-9][0-9]|1[0-1][0-9]|12[0-7])\.|127\.|169\.254\.|172\.1[6-9]\.|172\.2[0-9]\.|172\.3[0-1]\.|192\.0\.0\.|192\.0\.2\.|192\.168\.|198\.(1[8-9])\.|198\.51\.100\.|203\.0\.113\.|2(2[4-9]|[3-4][0-9]|5[0-5])\.|8\.8\.8\.8|8\.8\.4\.4|1\.1\.1\.1|1\.0\.0\.1)' | awk '!x[$0]++' | grep -F "/" | wc -l
63802
IP from non-Ranges:
Code:
curl -fsL --retry 3 --connect-timeout 3 "https://raw.githubusercontent.com/jumpsmm7/GeneratedAdblock/master/myfilter.list" | awk -F/ '{print $0}' | xargs "curl" -fsSL | grep -E '^(([0-9]{1,3}\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$' | grep -vE '^(0\.|10\.|100\.(6[4-9]|[7-9][0-9]|1[0-1][0-9]|12[0-7])\.|127\.|169\.254\.|172\.1[6-9]\.|172\.2[0-9]\.|172\.3[0-1]\.|192\.0\.0\.|192\.0\.2\.|192\.168\.|198\.(1[8-9])\.|198\.51\.100\.|203\.0\.113\.|2(2[4-9]|[3-4][0-9]|5[0-5])\.|8\.8\.8\.8|8\.8\.4\.4|1\.1\.1\.1|1\.0\.0\.1)' | awk '!x[$0]++' | grep -vF "/" | wc -l
475801