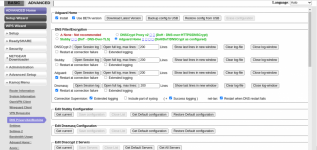
Same here on r7800 running Kamoj 5.4b35 on Voxels latest .The move device from vpn tunnel to bypass doesent move the device over and doesent appear in the show bypass rule.Hello dear Kamoj. Let's take a look at the VPN client settings in order.
1) In the latest version (Add-on V5.4b35), all connected devices immediately go through the VPN tunel. There is no way to create a priority menu for the required devices. Since VPN providers limit the number of active devices, I suggest that you make a function that will be active for selected devices, regardless of their connection method (or 2.4 GHz or 5 GHz or LAN). After creating and fixing the list of priority devices, you can start editing other devices, according to the type of their connection to the router.
2) After activating Bypass VPN, devices that do not go through the VPN are not displayed in the brown, right window.
3) The (Move selected devices) function does not work, that is, it does not move devices to the right window.
The rest of the functions work great!
Thanks a lot for your work !!!
Best regards to you.
Baursak.
Kamoj Kamoj Add-on Beta testing II
To me to NOT use killswitch is the same as not using VPN at all. Can you explain your reasoning, please?
Did you check the box for "Reboot router if Internet is down. May reboot every 150th sec. Use with caution"?
Maybe you have some logs to show (restart supervision, extended, wireguard)?
(I'm no oracle and can not guess what your issues come from. As a beta tester, please go deep, and at least show log-files.)
Also please report back in what version something was broken.
Thank you for your report!
I have provided the version of add-on: 5.4b35
I understand how complex debugging of things can be, so I don't even expect you to know the answer to this issue. I could share WG logs but they are irrelevant, because it seems like WG client has completely disregarded internet connection being down from ISP. Internet connection was down and PPPoE could not be established for a good 5mins, yet the WG client has shown green bar and status all the time like as if nothing happened... Same with the WG logs, where was absolutely nothing about any issues or session disconnection, this is what I find odd...
I do not use killswitch because I am not doing anything illegal like torrents etc. I use mainly VPN to overcome international traffic speed restrictions from ISP.
I don't even know where to look for a detailed logs in R9000, I have always been using Asus for many many years. The basic logs found under Admin page does not show detailed connection logs.
By the way I do have the option "Restart at connection failure" enabled, problem is the WG client does not seem to know there is any failure with the connection...
I had never thought of this! During the beta testing, I found Controld to be an excellent DNS service! After seeing your comment, I tried Controld using AdGuard Home on my R9000. Both DOH and TLS seem to be working (they are the only two DNS servers I am running). I haven't tried it yet using TLS in DNSCrypt... uncertain that it will work there but am going to try anyway.
As far as I know, only the legacy Controld DNS can be used for the main router settings(?).
Are you saying I should install Adguard Home and setting up DOH or DOT will be a breeze?
Yes, from the main router DNS settings, only legacy DNS can bet set. Netgear is really behind with all these new features. The absolutely best router I have is Synology rt2600ac in another location. Everything just works: dual wan, DOT, Synology SSL VPN server etc. But they don't support WG server or client and the router is dual core not 4 core like R9000.
In order to setup Adguard and DOH ControlD do I need to pay for Adguard subscription? I see that I need to log in, so I created account on adguard home website but the credentials are not working when trying to log in via router.
I seem to recall something similar happening on an earlier add-on version. However my internet drops so often that I wasn't sure this was the case or not. Have you tried the addon_fast_openvpn_supervision.sh via setting kamoj_fast_openvpn_supervison=1?
Excuse my lack of knowledge but where do I exactly set this up? I can see Connection supervision settings on DNS Privacy / ad blocking tab but I thought it is only for DNS.
I think it would be great having some simple ping / trace setup on VPN clients in which case they try to reconnect once the internet is down (e.g. failed 3 times every 5 seconds -> restart vpn connection).
Last edited:
kamoj
Very Senior Member
Impressing you know about this extra "hidden" tool!I seem to recall something similar happening on an earlier add-on version. However my internet drops so often that I wasn't sure this was the case or not. Have you tried the addon_fast_openvpn_supervision.sh via setting kamoj_fast_openvpn_supervison=1?
Kamoj, I have tried that and it appears to work for both OpenVPN and WireGuard - is that correct?
One thing I noticed is that the addon_fast_openvpn_supervision.sh acts a little too aggressive (I think) for my situation. Is the ping timeout derived from kamoj_ping_timeout, or otherwise adjustable withing the script?
Best wishes,
BL
Yes, it's aggressive. Next version is smarter but still aggressive...
The timeout is hardcoded to 3.0 sec.
To change it you can patch it to e.g. 10.0 sec with:
Code:
sed -i 's/3.0/10.0/g' /usr/bin/addon_fast_openvpn_supervision.shkamoj
Very Senior Member
Thank you very much for added information!I have provided the version of add-on: 5.4b35
I understand how complex debugging of things can be, so I don't even expect you to know the answer to this issue. I could share WG logs but they are irrelevant, because it seems like WG client has completely disregarded internet connection being down from ISP. Internet connection was down and PPPoE could not be established for a good 5mins, yet the WG client has shown green bar and status all the time like as if nothing happened... Same with the WG logs, where was absolutely nothing about any issues or session disconnection, this is what I find odd...
I do not use killswitch because I am not doing anything illegal like torrents etc. I use mainly VPN to overcome international traffic speed restrictions from ISP.
I don't even know where to look for a detailed logs in R9000, I have always been using Asus for many many years. The basic logs found under Admin page does not show detailed connection logs.
By the way I do have the option "Restart at connection failure" enabled, problem is the WG client does not seem to know there is any failure with the connection...
Are you saying I should install Adguard Home and setting up DOH or DOT will be a breeze?
Yes, from the main router DNS settings, only legacy DNS can bet set. Netgear is really behind with all these new features. The absolutely best router I have is Synology rt2600ac in another location. Everything just works: dual wan, DOT, Synology SSL VPN server etc. But they don't support WG server or client and the router is dual core not 4 core like R9000.
In order to setup Adguard and DOH ControlD do I need to pay for Adguard subscription? I see that I need to log in, so I created account on adguard home website but the credentials are not working when trying to log in via router.
Excuse my lack of knowledge but where do I exactly set this up? I can see Connection supervision settings on DNS Privacy / ad blocking tab but I thought it is only for DNS.
I think it would be great having some simple ping / trace setup on VPN clients in which case they try to reconnect once the internet is down (e.g. failed 3 times every 5 seconds -> restart vpn connection).
I'm sorry that the documentation could be better, but no one is willing to help me, and my time is very limited.
The most usefull log if you talk about the connection supervision is: System Information: Supervision
The next log is the wg log.
You can also switch on additional logging in Settings: DNS Privacy/Ad-Blocking: DNS Filter/Encryption: Connection Supervision: Extended logging + Include part of syslog,
and more supervision: net-lan: Restart when DNS restart fails
PS
It's not the wg at all that checks connection.
The connection check is done every minute by pinging a number of IPs and URLs.
(/usr/bin/addon_fast_openvpn_supervision.sh is run every 1-3rd second)
How is the WAN LED on the router when you have problem? Is it showing correctly or not?
Last edited:
Thank you very much for added information!
I'm sorry that the documentation could be better, but no one is willing to help me, and my time is very limited.
The most usefull log if you talk about the connection supervision is: System Information: Supervision
The next log is the wg log.
You can also switch on additional logging in Settings: DNS Privacy/Ad-Blocking: DNS Filter/Encryption: Connection Supervision: Extended logging + Include part of syslog,
and more supervision: net-lan: Restart when DNS restart fails
PS
It's not the wg at all that checks connection.
The connection check is done every minute by pinging a number of IPs and URLs.
(/usr/bin/addon_fast_openvpn_supervision.sh is run every 1-3rd second)
How is the WAN LED on the router when you have problem? Is it showing correctly or not?
Thank you. My R9000 is hidden in the networking closet a bit far from where I am sitting, so to be honest I did not check it. I saw on connection status page that the PPPoE was disconnected. Also the internet status on on Basic / home page was RED - disconnected. So I assume the WAN LED was not light up as well.
I wonder then why the connection checks have failed to notice lack of internet. There are 2 problems with this:
1. WG session not being terminated despite no internet access and WG client (all) logs were completely ignorant of this fact.
2. When the PPPoE connection came back and the IP was assigned, the internet was still not working on all devices and the WG client was still showing all the way green as if nothing happened at all. Only the manual disconnection of WG client has restored WAN activity in connected devices... This is also one of the reasons why I specifically do not use killswitch. If VPN fails and I am not at home, it is completely fine to revert back to using ISP directly. But it has to work and it failed to work unfortunately.
I will try to reproduce this issue by pulling out cable from ONT modem provided by ISP.
kamoj
Very Senior Member
The add-on use the Netgear function to set the color of the status-symbol.:Thank you. My R9000 is hidden in the networking closet a bit far from where I am sitting, so to be honest I did not check it. I saw on connection status page that the PPPoE was disconnected. Also the internet status on on Basic / home page was RED - disconnected. So I assume the WAN LED was not light up as well.
I wonder then why the connection checks have failed to notice lack of internet. There are 2 problems with this:
1. WG session not being terminated despite no internet access and WG client (all) logs were completely ignorant of this fact.
2. When the PPPoE connection came back and the IP was assigned, the internet was still not working on all devices and the WG client was still showing all the way green as if nothing happened at all. Only the manual disconnection of WG client has restored WAN activity in connected devices... This is also one of the reasons why I specifically do not use killswitch. If VPN fails and I am not at home, it is completely fine to revert back to using ISP directly. But it has to work and it failed to work unfortunately.
I will try to reproduce this issue by pulling out cable from ONT modem provided by ISP.
Code:
detcable showPlease run this command from router command line when you get the issue and report back here.
Anyhow, the restart supervision does not depend on this, but just doing ping.
So do ping from router and show results here at the same time.
Also attach a screen dump of "Router Information"!!!
HelloI setup account with Adguard Home but when trying to sign in through the router page it says: Error: control/login | invalid username or password | 400
Any clue what is going on?
Downloaded Adguard latest Beta - same issue.
Yes, I was talking about setting up AdGuard Home from the Kamoj Add-on. I had that problem with invalid username too. In my case I think the username in the AdGuard Home configuration file got corrupted and I had to uninstall and delete the configuration file at /opt/kamoj/addons/defaults/AdGuardHome.yaml.
I then reinstalled AdGuard Home following the instructions in the Kamoj FAQ and going through the various setup menus. After I made the configuration changes from the gui, I made a backup using the Add-on's AdGuard Home backup button so I wouldn't have to worry about the configuration file again.
To get the Controld DOH and TLS servers added to AdGuard Home, I entered the following into Settings/DNS Settings --> Upstream DNS Servers menu. The AdGuard server in the list is commented out as I wanted to try running just controld only.
With controld I am not using any filter lists (except my own whitelist and blacklist text files stored on the opt partition of the usb drive). However, I did set AdGuard to block some services that I do not use (at Filters/Blocked services).
Although I really like DNSCrypt-proxy, I didn't have any luck adding the controld DOH server to it. I imagine you could add the TLS server to Stubby, but using AdGuard Home was easy and it has other benefits too.
Hope that helps..
BL
Attachments
Thanks Kamoj! I thought those 3.0 values were the correct ones to change but I am usually better at breaking tings than fixing them so thought I had better ask. I changed the values and reactivated the script... thought I would give it a try.Impressing you know about this extra "hidden" tool!
Yes, it's aggressive. Next version is smarter but still aggressive...
The timeout is hardcoded to 3.0 sec.
To change it you can patch it to e.g. 10.0 sec with:
Code:sed -i 's/3.0/10.0/g' /usr/bin/addon_fast_openvpn_supervision.sh
By the way, thank you for the DNSMasq configuation read/modifiy capability on the DNS Privacy / Adblocking page. It is very handy for reinstalling changes after updating firmware.
BL
Hi @blueliner , super, thanks for help. I have erased, uninstalled and reinstalled Adguard home and I can finally see some 5 steps config menu which I did not see before. Page 2/5 of this config shows the following 2 errors:
Admin Web Interface: "listen tcp 0.0.0.0:80: bind: address already in use"
DNS server: "listen udp 0.0.0.0:53: bind: address already in use"
How did you overcome this issue? Also do you have "all interfaces" checked for both?
As for controld, I mainly use it to unblock some geo blocked services, but I do have to say that filters come handy such as safe search etc. I do note there is no need to use ad filter on controld.com once we setup adguard + controld. My question is if this adguard ad block database is hosted locally on the router or some external connection is being made to check on each DNS request - but that would not make sense, as we skip Adguard DNS with ControlD in such case.
Admin Web Interface: "listen tcp 0.0.0.0:80: bind: address already in use"
DNS server: "listen udp 0.0.0.0:53: bind: address already in use"
How did you overcome this issue? Also do you have "all interfaces" checked for both?
As for controld, I mainly use it to unblock some geo blocked services, but I do have to say that filters come handy such as safe search etc. I do note there is no need to use ad filter on controld.com once we setup adguard + controld. My question is if this adguard ad block database is hosted locally on the router or some external connection is being made to check on each DNS request - but that would not make sense, as we skip Adguard DNS with ControlD in such case.
Last edited:
jberry
Regular Contributor
Hello primitivo, I just received my R9000 router, and installed the latest version of Voxel and latest beta, b35 for Kamoj. I did notice that when I would reboot my router, the wireguard connection wont connect automatically. I am using PPPoE as well to connect to my ISP. What I figured out is, that OpenVPN had a green check mark on it, but I dont use OpenVPN I use wireguard. SO what I did was click it to become red, and make sure to click the small box in the wireguard window to be the green check mark. Then when I did the test to reboot the R9000, wireguard would automatically connect to my VPN, maybe for you the OpenVPN has a green box, if you dont use it, just click it to red, not sure if this makes a difference, it did for me.I have provided the version of add-on: 5.4b35
I understand how complex debugging of things can be, so I don't even expect you to know the answer to this issue. I could share WG logs but they are irrelevant, because it seems like WG client has completely disregarded internet connection being down from ISP. Internet connection was down and PPPoE could not be established for a good 5mins, yet the WG client has shown green bar and status all the time like as if nothing happened... Same with the WG logs, where was absolutely nothing about any issues or session disconnection, this is what I find odd...
I do not use killswitch because I am not doing anything illegal like torrents etc. I use mainly VPN to overcome international traffic speed restrictions from ISP.
I don't even know where to look for a detailed logs in R9000, I have always been using Asus for many many years. The basic logs found under Admin page does not show detailed connection logs.
By the way I do have the option "Restart at connection failure" enabled, problem is the WG client does not seem to know there is any failure with the connection...
Are you saying I should install Adguard Home and setting up DOH or DOT will be a breeze?
Yes, from the main router DNS settings, only legacy DNS can bet set. Netgear is really behind with all these new features. The absolutely best router I have is Synology rt2600ac in another location. Everything just works: dual wan, DOT, Synology SSL VPN server etc. But they don't support WG server or client and the router is dual core not 4 core like R9000.
In order to setup Adguard and DOH ControlD do I need to pay for Adguard subscription? I see that I need to log in, so I created account on adguard home website but the credentials are not working when trying to log in via router.
Excuse my lack of knowledge but where do I exactly set this up? I can see Connection supervision settings on DNS Privacy / ad blocking tab but I thought it is only for DNS.
I think it would be great having some simple ping / trace setup on VPN clients in which case they try to reconnect once the internet is down (e.g. failed 3 times every 5 seconds -> restart vpn connection).


Thanks, it did the trick for rebooting the router on R9000 & WG connecting on router start. @kamoj I believe it is a bug in 5.4b35 version that OpenVPN check mark is enabled by default and I don't use OVPN at all so I did not notice this.Hello primitivo, I just received my R9000 router, and installed the latest version of Voxel and latest beta, b35 for Kamoj. I did notice that when I would reboot my router, the wireguard connection wont connect automatically. I am using PPPoE as well to connect to my ISP. What I figured out is, that OpenVPN had a green check mark on it, but I dont use OpenVPN I use wireguard. SO what I did was click it to become red, and make sure to click the small box in the wireguard window to be the green check mark. Then when I did the test to reboot the R9000, wireguard would automatically connect to my VPN, maybe for you the OpenVPN has a green box, if you dont use it, just click it to red, not sure if this makes a difference, it did for me.
Good to hear that you have PPPoE + R9000 @jberry , let's see if we have similar behaviour to the connection drops. I will definitely test and debug the issue reported before more.
kamoj
Very Senior Member
Very good finding!Hello primitivo, I just received my R9000 router, and installed the latest version of Voxel and latest beta, b35 for Kamoj. I did notice that when I would reboot my router, the wireguard connection wont connect automatically. I am using PPPoE as well to connect to my ISP. What I figured out is, that OpenVPN had a green check mark on it, but I dont use OpenVPN I use wireguard. SO what I did was click it to become red, and make sure to click the small box in the wireguard window to be the green check mark. Then when I did the test to reboot the R9000, wireguard would automatically connect to my VPN, maybe for you the OpenVPN has a green box, if you dont use it, just click it to red, not sure if this makes a difference, it did for me.

Thank you for posting this and even with pictures embedded - very nice!
kamoj
Very Senior Member
For me this is really good, because I have some problems with all possible configurations...Thanks, it did the trick for rebooting the router on R9000 & WG connecting on router start. @kamoj I believe it is a bug in 5.4b35 version that OpenVPN check mark is enabled by default and I don't use OVPN at all so I did not notice this.
Good to hear that you have PPPoE + R9000 @jberry , let's see if we have similar behaviour to the connection drops. I will definitely test and debug the issue reported before more.
E.g. I don't have/use any these:
- R9000
- PPPoE
- Wireguard
This is only one example of why this beta is still a beta. It's difficult/impossible for me to test everything.
It would be easier to drop R9000 support, but it's hard to desert/let-down the increasing number of R9000 users.
Especially since the share percentage of R8900/R9000 users for the add-on is so high: >40 %!
So for the moment, let's debug this beta together and make it a stable product - together.
jberry
Regular Contributor
Yes will be monitoring as well! thanks!Thanks, it did the trick for rebooting the router on R9000 & WG connecting on router start. @kamoj I believe it is a bug in 5.4b35 version that OpenVPN check mark is enabled by default and I don't use OVPN at all so I did not notice this.
Good to hear that you have PPPoE + R9000 @jberry , let's see if we have similar behaviour to the connection drops. I will definitely test and debug the issue reported before more.
You are very welcome sir!Very good finding!
Thank you for posting this and even with pictures embedded - very nice!
Yes sounds good! Especially since the R9000 came down a bit in the used market, thats how I was able to upgrade from my R7800 to the R9000. I am thinking its also the way PPPoE behaves, as it has to 'dial' in to the ISP to get internet, and if it drops it has to dial back, and the WireGuard protocol has to wait first, if PPPoE can successfully connect, will be monitoring...For me this is really good, because I have some problems with all possible configurations...
E.g. I don't have/use any these:
- R9000
- PPPoE
- Wireguard
This is only one example of why this beta is still a beta. It's difficult/impossible for me to test everything.
It would be easier to drop R9000 support, but it's hard to desert/let-down the increasing number of R9000 users.
Especially since the share percentage of R8900/R9000 users for the add-on is so high: >40 %!
So for the moment, let's debug this beta together and make it a stable product - together.
R9000: I can still break WG connection and then addon gets crazy. There is a very specific way to reproduce this issue and it involves having Torguard dedicated IP. If @kamoj or anyone else is interested to see it themselves, I can PM my Skype or Telegram. I would then give you my TG config with dedicated IP, once up and running I would break your WG connection by generating a new TG config. Every time new TG WG config is generated, it breaks the existing connectivity.
Logs (supervision + WG log + hard wired PC ping since it broke): https://pastebin.com/bm9DKd5F
Don't know why WG log is not complete, I guess it is time limited. But anyway you should be able to see the issue. If not, I can reproduce this every single time.
Don't get me wrong, until I break it, everything works great. But the moment it breaks, I would expect going back to normal ISP connectivity, instead of behaving like killswitch would be enabled although it is not.
Also funny thing, manual disabling of WG client did not fix the issue, more over the green status shield remained green... Only reboot has fixed the issue:

Logs (supervision + WG log + hard wired PC ping since it broke): https://pastebin.com/bm9DKd5F
Don't know why WG log is not complete, I guess it is time limited. But anyway you should be able to see the issue. If not, I can reproduce this every single time.
Don't get me wrong, until I break it, everything works great. But the moment it breaks, I would expect going back to normal ISP connectivity, instead of behaving like killswitch would be enabled although it is not.
Also funny thing, manual disabling of WG client did not fix the issue, more over the green status shield remained green... Only reboot has fixed the issue:
jberry
Regular Contributor
Ah okay, I have about 5 active VPN accounts with different providers (so I can test or move to another VPN provider if one is giving me bad quality IP), the one I use the most is TorGuard, I have one dedicated in LA and SD (residential IPs). TorGuard made an announcement that recently when you generate a WireGuard config file, you will be able to log in at a later time, so will not time out (meaning your private key I guess will not expire). In the past, if you generated a config file, then used it for a bit, then disconnected from TorGuard, and came back like a day later, the connection will be invalid and you would have to re do the config again just to re connect. So making it once now, you are good to go, but I do see why you are breaking it on purpose just to test if you will go back to your ISP default.R9000: I can still break WG connection and then addon gets crazy. There is a very specific way to reproduce this issue and it involves having Torguard dedicated IP. If @kamoj or anyone else is interested to see it themselves, I can PM my Skype or Telegram. I would then give you my TG config with dedicated IP, once up and running I would break your WG connection by generating a new TG config. Every time new TG WG config is generated, it breaks the existing connectivity.
Logs (supervision + WG log + hard wired PC ping since it broke): https://pastebin.com/bm9DKd5F
Don't know why WG log is not complete, I guess it is time limited. But anyway you should be able to see the issue. If not, I can reproduce this every single time.
Don't get me wrong, until I break it, everything works great. But the moment it breaks, I would expect going back to normal ISP connectivity, instead of behaving like killswitch would be enabled although it is not.
Also funny thing, manual disabling of WG client did not fix the issue, more over the green status shield remained green... Only reboot has fixed the issue:
View attachment 35881
I just tried this now, made a new config file for my WG at TorGuard, and I got kicked off of course, and waited a bit, my local ISP internet did not kick in. I checked and I have been connected for over 22 hours and still connected, but no internet traffic via Wifi and LAN. Not sure why we are not going back to regular ISP internet, seems like a kill switch. I did try to reconnect with my new TorGuard WG config file and it connected just fine. I think this is just by design, like what Kamoj said whats the use of using a VPN if you want it to go back to your regular internet ( and possibly leak stuff ).
I do get what you are saying, lets say someone in my household is doing an important business meeting, VPN goes out, the person will be frustrated because they cant get back on the business meeting if there is no internet at all, and I'm not around to log back into the router and reconnect the VPN.
Ah okay, I have about 5 active VPN accounts with different providers (so I can test or move to another VPN provider if one is giving me bad quality IP), the one I use the most is TorGuard, I have one dedicated in LA and SD (residential IPs). TorGuard made an announcement that recently when you generate a WireGuard config file, you will be able to log in at a later time, so will not time out (meaning your private key I guess will not expire). In the past, if you generated a config file, then used it for a bit, then disconnected from TorGuard, and came back like a day later, the connection will be invalid and you would have to re do the config again just to re connect. So making it once now, you are good to go, but I do see why you are breaking it on purpose just to test if you will go back to your ISP default.
I am glad we have the same VPN provider with dedicated IP to test. Yes, you are right that Torguard has recently changed its policy. Before the validity of the configs was 24 hours, meaning if you did not use it for more than that, you had to generate a new config. Now, with the recent changes, if you generate the config it says the same until validity of your account unless you generate a new one.
I just tried this now, made a new config file for my WG at TorGuard, and I got kicked off of course, and waited a bit, my local ISP internet did not kick in. I checked and I have been connected for over 22 hours and still connected, but no internet traffic via Wifi and LAN. Not sure why we are not going back to regular ISP internet, seems like a kill switch. I did try to reconnect with my new TorGuard WG config file and it connected just fine. I think this is just by design, like what Kamoj said whats the use of using a VPN if you want it to go back to your regular internet ( and possibly leak stuff ).
Well, since the killswitch is optional, then I would not say it is by design like that. There is a bug somewhere with checking if the WG connection is up or down. If you see my logs you will see that at some point, WG gives up at trying or re-trying:
16:45:48 Wireguard Client completed start sequence
16:47:58 Wireguard Client completed start sequence
And for more than 1 minute nothing, in fact nothing more has happened for several good minutes as I was watching. Also the supervision logs I posted are showing activity until 16:49:13, but there was nothing more recent in WG logs at all. I also had no ISP internet connectivity.
You can also see by my pings from PC that some pings do get through directly via ISP, which means sometimes there is ISP connectivity present for a while but either WG client restarting or retrying is breaking it - hard to say. If that would be a killswitch, then it doesn't work
I do get what you are saying, lets say someone in my household is doing an important business meeting, VPN goes out, the person will be frustrated because they cant get back on the business meeting if there is no internet at all, and I'm not around to log back into the router and reconnect the VPN.
Exactly. And this would be my least concern, as nobody except myself is going to generate a new TG config. I wanted to remind that this behaviour has happened when PPPoE connection from ISP was down for 10+ mins. Once it came back, neither WG session was restored, nor ISP internet connectivity was present. I had to untick the green box manually on WG client to make things working, which as I said, is not a desired solution especially with killswitch disabled.
Last edited:
Hello Primitivo,Hi @blueliner , super, thanks for help. I have erased, uninstalled and reinstalled Adguard home and I can finally see some 5 steps config menu which I did not see before. Page 2/5 of this config shows the following 2 errors:
Admin Web Interface: "listen tcp 0.0.0.0:80: bind: address already in use"
DNS server: "listen udp 0.0.0.0:53: bind: address already in use"
How did you overcome this issue? Also do you have "all interfaces" checked for both?
As for controld, I mainly use it to unblock some geo blocked services, but I do have to say that filters come handy such as safe search etc. I do note there is no need to use ad filter on controld.com once we setup adguard + controld. My question is if this adguard ad block database is hosted locally on the router or some external connection is being made to check on each DNS request - but that would not make sense, as we skip Adguard DNS with ControlD in such case.
It has been a long time since I set up AdGuard. As I recall, the setup menu gives the option to use an alternate address
" How can I setup Adguard Home by myself?
A: - First stop Adguard Home:
Kamoj Menu: DNS Privacy/Ad-Blocking: DNS Filter/Encryption: None
- Delete the current configuration:
Kamoj Menu: DNS Privacy/Ad-Blocking: Adguard Home: Erase configuration
- Start Adguard Home:
Kamoj Menu: DNS Privacy/Ad-Blocking: DNS Filter/Encryption: Adguard Home
- Start setup program:
*If you access your router through it's IP eg 192.168.1.1: Kamoj Menu: Adguard Home Setup
*If you not access the router through it's IP, open: http://192.168.1.1:3000
Run the guide, it's very easy. You can select one of many available languages as well.
If you are not expert, I advice you to use these values:
Admin Web Interface: Listen interface: 8080
DNS server: Listen interface: 5300
After The last "Open Dashboard", close the window".
AdGuard itself has the option to use their hosted database for security checks, parental control and safe search. You can also use your own or third party blocklists by entering the ip address for the file location.
I have attached some partial screen shots of these options.
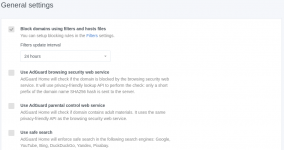
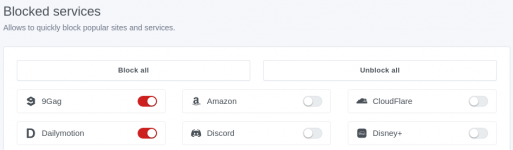
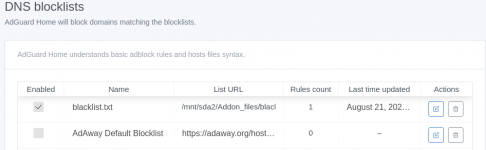
Best wishes,
BL
Similar threads
- Replies
- 41
- Views
- 3K
- Replies
- 2
- Views
- 3K
- Replies
- 499
- Views
- 72K
- Replies
- 522
- Views
- 72K
- Replies
- 282
- Views
- 28K
Similar threads
| Thread starter | Title | Forum | Replies | Date |
|---|---|---|---|---|
| M | Kamoj Kamoj Addon 5.5 Beta for Netgear R7800/R8900/R9000 with Voxel FW - Continuation | NETGEAR AC Routers and Adapters (Wi-Fi 5) | 41 |
Similar threads
-
Kamoj Kamoj Addon 5.5 Beta for Netgear R7800/R8900/R9000 with Voxel FW - Continuation
- Started by matttt22
- Replies: 41
Latest threads
-
Release ASUS GT-AXE11000 Firmware version 3.0.0.4.388_23883 (2025/04/28)
- Started by fruitcornbread
- Replies: 0
-
Release ASUS RT-AXE7800 Firmware version 3.0.0.4.388_25144 (2025/04/28)
- Started by fruitcornbread
- Replies: 0
-
Voxel R7800 Voxel - dhcp - different gateway for specific IPs
- Started by joshhighley
- Replies: 0
-
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!