Preskitt.man
Senior Member
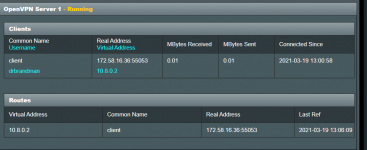
Am running Merlin 386.1_2 So, I decided to implement OpenVPN server on my AC86U. Technically, it went well, and my test client Samsung S20 connected to the VPN. Having said that, my phone behaves as if it were still just connected to my ISP - T-Mobile. WiFi is turned off on the phone, just cellular via T-Mobile. If I do a WhatsMyIP, it shows the address from T-Mobile, not the address from the Router, so internet queries are not going through the VPN. And pinging the address of any device on the LAN (192.168.1.x), fails. WiFMan shows my IP address to be 10.8.0.2, which fits in with the VPN settings, and it's graphic shows Internet ->Gateway -> to phone (@10.8.0.2)
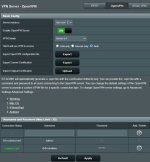
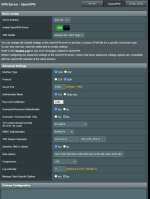
The entire setup at this time is pure vanilla. Enabled the VPN Server, checked that I would like to access both the internet and the lan, set a userid and password, and applied the settings. Downloaded the config file and imported into VPN Connect 3 client for Android. Connected using the userid and password previously supplied, and the connection was made. But as noted, internet connections seem to be directly through T-Mobile's cellular connection with no routing to my network. And certainly can't see my local devices. Frankly, I'm not sure how that would ever work with an assigned IP address of 10.8.0.2 from OpenVPN, but in reading the conflicting posts (lot of opinions on what to do), recommendation was not to set a connection on the 192.168.1.x network.
What I would like the end result to be is two fold:
1) When my phone connects, internet traffic gets routed through my router and then to the internet
2) When using my MAC and/or Windows laptop, I can access devices on my LAN
Any Ideas?
The entire setup at this time is pure vanilla. Enabled the VPN Server, checked that I would like to access both the internet and the lan, set a userid and password, and applied the settings. Downloaded the config file and imported into VPN Connect 3 client for Android. Connected using the userid and password previously supplied, and the connection was made. But as noted, internet connections seem to be directly through T-Mobile's cellular connection with no routing to my network. And certainly can't see my local devices. Frankly, I'm not sure how that would ever work with an assigned IP address of 10.8.0.2 from OpenVPN, but in reading the conflicting posts (lot of opinions on what to do), recommendation was not to set a connection on the 192.168.1.x network.
What I would like the end result to be is two fold:
1) When my phone connects, internet traffic gets routed through my router and then to the internet
2) When using my MAC and/or Windows laptop, I can access devices on my LAN
Any Ideas?