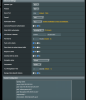
Then you are overdoing it and got lost on all modification.
1. Delete all scripts.
2. Use VPN Client 1
3. In router GUI for VPN Client 1 set policy rules to use VPN on certain LAN IP's, rest is WAN.
4. Create new "openvpn-event" script from post #6 and change last lines with your IP's and ports. This is for WAN access to VPN only devices.
5. Port forward those ports in router GUI.
6. Add rules from post #2 to same openvpn-event script, on script end, and change IP's / ports to match needed ports. You need 4 rules for every port if you want to use both UDP and TCP. If you want to use more then 1 port on one IP, you can't use those rules, you need to change them and use muli IP rule in 1 line. This is for access trough VPN exit server. DON'T PORT FORWARD THOSE PORTS ON ROUTER GUI. Also, your VPN provider MUST provide port forwarding for those same ports to your machine or it won't work at all.
7. Chmod "openvpn-event" script to be executable.
8. If you are working with windows machine, be sure file isn't saved with non-unix letters.
9. Restart router.
10. Wait for everything to start, cca 2 min, and if you set everything right, it should work.
1. Delete all scripts.
2. Use VPN Client 1
3. In router GUI for VPN Client 1 set policy rules to use VPN on certain LAN IP's, rest is WAN.
4. Create new "openvpn-event" script from post #6 and change last lines with your IP's and ports. This is for WAN access to VPN only devices.
5. Port forward those ports in router GUI.
6. Add rules from post #2 to same openvpn-event script, on script end, and change IP's / ports to match needed ports. You need 4 rules for every port if you want to use both UDP and TCP. If you want to use more then 1 port on one IP, you can't use those rules, you need to change them and use muli IP rule in 1 line. This is for access trough VPN exit server. DON'T PORT FORWARD THOSE PORTS ON ROUTER GUI. Also, your VPN provider MUST provide port forwarding for those same ports to your machine or it won't work at all.
7. Chmod "openvpn-event" script to be executable.
8. If you are working with windows machine, be sure file isn't saved with non-unix letters.
9. Restart router.
10. Wait for everything to start, cca 2 min, and if you set everything right, it should work.