ZebMcKayhan
Very Senior Member
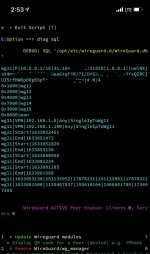
i am also getting that error below once starting wg11. not sure what it means. thank you.
wireguard-clientwg11: Initialising Wireguard VPN 'client' Peer (wg11) DNS=1.0.0.1
Error: table traffic has 6 columns but 4 values were supplied
wireguard-clientwg11: Initialisation complete.

Wireguard - Session Manager - Discussion thread (CLOSED/EXPIRED Oct 2021 use http://www.snbforums.com/threads/session-manager-discussion-2nd-thread.75129/)
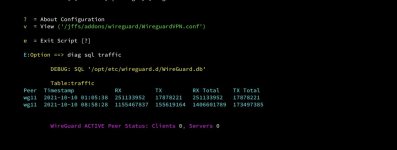
Hello, Wondering how to enterpret the stats (which by the way have not produced any negative numbers!) For example 2 consecutive statistics: Jun 21 18:59:00 RT-AC86U-D7D8 (wg_manager.sh): 676 Clients [97m2[95m, Servers [97m0 Jun 21 18:59:01 RT-AC86U-D7D8 (wg_manager.sh): 676 wg11:[97m transfer...
 www.snbforums.com
www.snbforums.com
//Zeb