Martineau
Part of the Furniture
I think @ZebMcKayhan may have identified a bug with the WAN KILL-Switch feature.....however until I can release a possible fix....Hey!
Thanks again for the answers. I generated a new Wireguard key from my provider OVPN.com tried it on my iPhone with the iOS Wireguard app and no issues.
Uploaded the conf file to the router and did an import. Compared the original and the ported one, and the only difference was that in the ported conf, DNS and Address were disabled with #.
Started the imported key in WGM and Internet stops
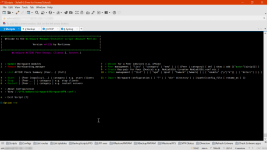
Could you please issue:
Code:
e = Exit Script [?]
E:Option ==> killswitch off
Code:
e = Exit Script [?]
E:Option ==> diagdiag output then you can PM the output to meEDIT: I see @ZebMcKayhan has already offered support!