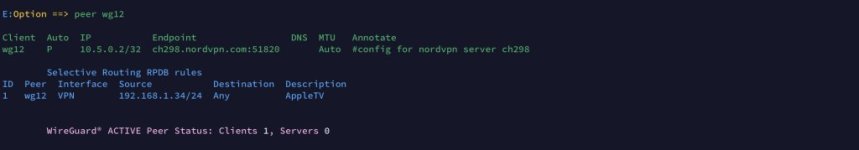
I got the exact same error as Ubimo. New RT-AX88u router, installed latest Merlin, set to default, installed amtm, used it to install flexqos then wg manager. Got his error. Used your suggestions, what it shows is this now:
Code:
Router RT-AX88U Firmware (v386.8_0)
[✔] Entware Architecture arch=aarch64
v4.18 WireGuard® Session Manager (Change Log: https://github.com/MartineauUK/wireguard/commits/main/wg_manager.sh)
MD5=1036fe1ca4df245cb50db0e069550da4 /jffs/addons/wireguard/wg_manager.sh
v4.17.9 (wg_client)
v4.17.1 (wg_server)
[ℹ ] WireGuard® Kernel module/User Space Tools included in Firmware (1.0.20210124) but 3rd-Party modules installed...
wireguard: WireGuard 1.0.20210124 loaded. See www.wireguard.com for information.
wireguard: Copyright (C) 2015-2019 Jason A. Donenfeld <Jason@zx2c4.com>. All Rights Reserved.
[✔] WireGuard® Module LOADED Fri Sep 9 23:55:06 CDT 2022
MD5=70a85a1bed5f6313add595e2a95423c4 wireguard-kernel_1.0.20220627-RT-AX88U_aarch64-3.10.ipk
MD5=3c3fef331578bcd20714a148b96257f8 wireguard-tools_1.0.20210914-1_aarch64-3.10.ipk
[✔] DNSmasq is listening on ALL WireGuard® interfaces 'wg*'
[✔] firewall-start is monitoring WireGuard® Firewall rules
[✖] WAN KILL-Switch is DISABLED (use 'vx' command for info)
[✖] UDP monitor is DISABLED
[✔] Flow Cache is ENABLED
[✖] IPv6 Service is DISABLED
[ℹ ] IPv4,52.144.111.235,v1.1,,,See http://ip6.me/docs/ for api documentation
[✔] Reverse Path Filtering ENABLED
[✔]Use 3rd-party Entware/Userspace Tools modules is ALLOWED
[✔] Use of 'Pg-Up' Key for command retrieval is ENABLED
[✔] Statistics gathering is ENABLED
[ℹ ] Speedtest link https://fast.com/en/gb/
[ℹ ] IPv6 Test link https://ipv6-test.com/
[ℹ ] WireGuard© Official Site https://www.wireguard.com/
[ℹ ] @ZebMcKayhan's Hint's and Tips Guide https://github.com/ZebMcKayhan/WireguardManager/blob/main/README.md#table-of-content
So, hopefully, all will be well though it seems very strange. On to setting it up!
Well.... This is so much different than just generic wireguard which has been simple to me. I have all sort of clients and a single server. Kind of lost on the terminology being used in this addon.
Essentially, I am behind CGNAT. I have a public server on the internet with wireguard. It has everything set up, a bunch of "clients" to it. I have currently an ubuntu machine at home, behind cgnat, that connects to the public server running wireguard. All my mobile devices, travel routers, and other machines connect to the public wireguard machine, and that machine sends all traffic destined for my home lan ips to the ubuntu machine on my home lan, which forwards all that traffic to my lan. I want to do the same, but replace my ubuntu machine with the ASUS router.
From what I can tell, wgm is setup to make configurations for all involved devices, I don't want that. It's all setup. All I want is to create the interface for ASUS device, with the already existing public server as it's peer, it already has it's own keys. So, that is the ASUS peer section endpoint, the public server. I don't want any traffic going there from the LAN except to the WG ip assigned to the public server. The other part is I need the Asus device to forward traffic sent to it to my LAN.
So, how do I accomplish this? Essentially, I want to duplicate what I have for my ubuntu configuration. In the end, the Asus wireguard config (assuming plain wireguard) would look like:
[Interface]
PrivateKey = notgonnashowit
Address = 192.168.10.6/32
DNS = 1.1.1.1,1.0.0.1
MTU = 1404
a bunch of PostUp and PostDown iptables rules
[Peer]
PublicKey = notgonnatellyou
AllowedIPs = 192.168.10.0/24
Endpoint = publicserverip:somepport
PersistentKeepalive = 25
I already have the keys, etc. for the public machine and all it's other clients and I don't want to redo it all. All clients not on my lan connect to the public server, and have access to my home lan even though it's behind CGNAT.