Thanks for the help guys! Appreciate it!
So what I have done:
- cd /jffs/scripts/
- Edited the firewall-start and added
Code:
#!/bin/sh
/jffs/addon/wireguard/wg-tool.sh firewall show
- added with 'nano' the file nat-start with
Code:
#!/bin/sh
/jffs.../wg-tool.sh nat show
- added with 'nano' the file services-start with
Code:
#!/bin/sh
/jffs/.../wg-tool.sh start br-sao show
- Executed the "chmod a+rx /jffs/scripts/*" to change permissions
- rebooted.
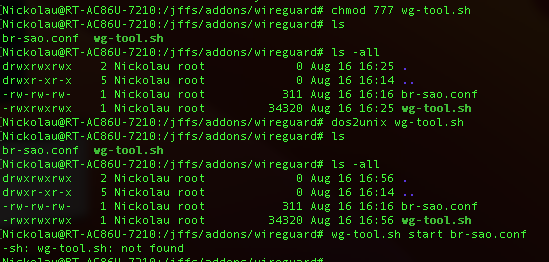
Not working. No access to internet. I have this error:
Nickolau@RT-AC86U-7210:/tmp# /jffs/addons/wireguard/wg-tool.sh start br-sao show
Wireguard interface br-sao appears to be already up! To restart use the RESTART command
Error reported parsing config file, not adding firewall entries
Nickolau@RT-AC86U-7210:/tmp# /jffs/addons/wireguard/wg-tool.sh restart br-sao show
[#] ip -4 rule delete table 51820
[#] ip rule delete table main suppress_prefixlength 0
[#] ip link del dev br-sao
Wireguard interface br-sao successfully deleted
Deleting firewall rules
Deleting NAT Rules
[#] ip link add dev br-sao type wireguard
[#] ip -4 address add dev br-sao 10.14.0.2/16
[#] ip link set up dev br-sao
[#] ip link set mtu 1420 up dev br-sao
[#] ip -4 route add 0.0.0.0/0 dev br-sao table 51820
[#] ip -4 rule add not fwmark 51820 table 51820
[#] ip -4 rule add table main suppress_prefixlength 0
Wireguard interface br-sao successfully added
Adding firewall rules
[#] iptables -I INPUT -i br-sao -j ACCEPT
[#] iptables -I FORWARD -i br-sao -j ACCEPT
[#] iptables -I FORWARD -o br-sao -j ACCEPT
[#] iptables -I OUTPUT -o br-sao -j ACCEPT
Adding NAT Rules
[#] iptables -t mangle -I FORWARD -o br-sao -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
[#] iptables -t mangle -I FORWARD -i br-sao -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
[#] iptables -t mangle -I FORWARD -o br-sao -j MARK --set-xmark 0x01/0x7
[#] iptables -t mangle -I PREROUTING -i br-sao -j MARK --set-xmark 0x01/0x7
[#] iptables -t nat -I POSTROUTING -s 10.0.0.0/24 -o br-sao -j MASQUERADE
[#] iptables -t nat -N DNSbr-sao
[#] iptables -t nat -I PREROUTING -p tcp -m tcp --dport 53 -j DNSbr-sao
[#] iptables -t nat -I PREROUTING -p udp -m udp --dport 53 -j DNSbr-sao
[#] iptables -t nat -I OUTPUT -o br-sao -p tcp -m tcp --dport 53 -j DNSbr-sao
[#] iptables -t nat -I OUTPUT -o br-sao -p udp -m udp --dport 53 -j DNSbr-sao
[#] iptables -t nat -I DNSbr-sao -p tcp -s 10.0.0.0/24 -j DNAT --to-destination 162.252.172.57:53
[#] iptables -t nat -I DNSbr-sao -p udp -s 10.0.0.0/24 -j DNAT --to-destination 162.252.172.57:53
[#] iptables -t nat -I DNSbr-sao -p tcp -s 10.0.0.0/24 -j DNAT --to-destination 149.154.159.92:53
[#] iptables -t nat -I DNSbr-sao -p udp -s 10.0.0.0/24 -j DNAT --to-destination 149.154.159.92:53
[#] iptables -t mangle -A PREROUTING -p udp -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff
[#] iptables -t mangle -A POSTROUTING -p udp -m mark --mark 0xca6c -j CONNMARK --save-mark --nfmask 0xffffffff --ctmask 0xffffffff
[#] iptables -t raw -A PREROUTING -d 10.14.0.2/16 ! -i br-sao -m addrtype ! --src-type LOCAL -j DROP
Nickolau@RT-AC86U-7210:/tmp#
What have I done wrong?
Edit: When I run it manually (commenting the scripts and running it by command line with the ./wg-tool.sh start... ), it works fine.