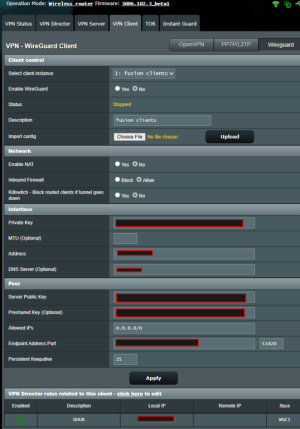
I'm trying to setup vpn for all network attached devices but without the need to configure it on the devices itselves.
The wireguard server is up&running and working because I have a VPN client for my mobile phones and they just work fine using local config on the mobile phone.
For the other devices I setup a new client in the same server using a different ip as the mobile client.
I created a wireguard client (see screenshot) . I linked 1 device to test all, but the device is unable to connect to the wifi or internet.
What is wrong in my config.
The wireguard server is up&running and working because I have a VPN client for my mobile phones and they just work fine using local config on the mobile phone.
For the other devices I setup a new client in the same server using a different ip as the mobile client.
I created a wireguard client (see screenshot) . I linked 1 device to test all, but the device is unable to connect to the wifi or internet.
What is wrong in my config.