I put the "pieces together" about 7-8 years ago. I don't recall exactly when, but it was well before the COVID-19 lockdowns started, and I was not even specifically looking to change the RSA key size.
You see, I was managing my parents' & my in-laws' network routers (a pair of RT-AC68Us back then), and I had set up the OpenVPN Servers so that I could remotely log in and check things out whenever they had some issues or wanted me to tweak some settings. I had the 2 OpenVPN servers for each router configured exactly the same (except for port number & IP subnet address, of course), but only the 1st server was left enabled/active. The 2nd server was a backup just in case the 1st one was, for some reason, not active or running, and my watchdog script would automatically enable & start the 2nd server.
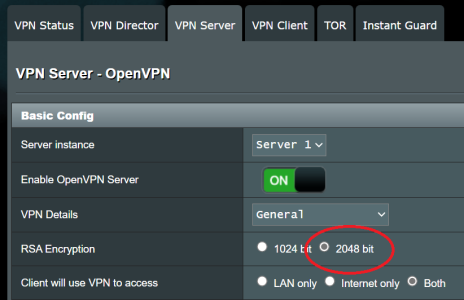
During the process of setting all this up, I noticed that the RSA key size option became available only when toggling the OpenVPN server
OFF and then back
ON. Later on, while playing with some options, I read the tooltip that pops up for the "
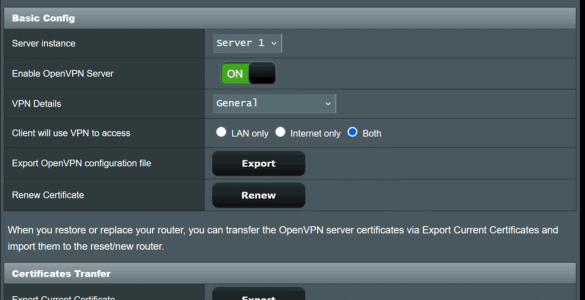
Renew Certificate" title (see sample screenshot below), which was the key piece indicating how to regenerate the keys & certificates when needed *without* reconfiguring the server.
View attachment 64668
So, to try to answer your question, I figured out the steps not in one single session, but it was more of a series of events that led me to the serendipitous discovery while setting up & testing the 2 OpenVPN servers so they would operate the way I wanted them to for my parents & in-laws.