You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Adguard Home and clients of subnet (wireguard tunnel)
- Thread starter atorcha
- Start date
ZebMcKayhan
Very Senior Member
You will need to turn off nat (MASQUARADE) on GL Inet router. As this setting changes source address to be wg address for the entire lan.View attachment 60891
View attachment 60892
Hello, I only see in adguard IP of GLINET X750 and I would like to see IP of devices, in order to made differentes profiles for each one.
How can I do that?
Furthermore, you will need to add on Asus router wireguard server on the peer to GL Inet router:
AllowedIPs (Server): 10.6.0.10/32, 192.168.10.0/24
I think you find this setting alittle hidden under site-2-site settings.
Last edited:
You will need to turn off nat (MASQUARADE) on GL Inet router. As this setting changes source address to be wg address for the entire lan.
Furthermore, you will need to add on Asus router wireguard server on the peer to GL Inet router:
AllowedIPs (Server): 10.6.0.10/30, 192.168.10.0/24
I think you find this setting alittle hidden under site-2-site settings.
But I don´t know how to : to turn off nat (MASQUARADE) on GL Inet router
What I want is see IP devices ( for example 192.168.10.101) in ADH to apply rules and specific filters
ZebMcKayhan
Very Senior Member
Can't help you with that, try Google.But I don´t know how to : to turn off nat (MASQUARADE) on GL Inet router
I get that, and right now you only see 10.6.0.10 for every lan device. This is how MASQUARADE works, same as your entire lan uses a single public ip. But this is not an asus router issue, it's a GL Inet router issue.What I want is see IP devices ( for example 192.168.10.101) in ADH to apply rules and specific filters
eibgrad
Part of the Furniture
Given the GL.iNet devices typically use third-party firmware (OpenWRT) and most make NAT'ing the tunnel on a VPN optional (if only to support site-to-site configurations), I'd be surprised if it wasn't there in the firmware. But I don't use OpenWRT, so I can't confirm one way or the other. If it isn't, that would seem to be a major oversight imo. Or perhaps it's been removed from the GUI under the assumption it's considered a travel router, where site-to-site would be very unusual, so in the name of simplicity, they removed it. Even so, if you have access to SSH, you should be able to remove the NAT rule yourself, although you would have to have a means via OpenWRT to make it persistent across a restart of the VPN and/or router.
Of course, all this assumes you also have static routing configured properly on the WG server side (the use of NAT w/ the WG client is intended to make that unnecessary).
The other option is to reverse the roles of the WG connection, making the client the server, and vice versa, putting the client on the device where you presumably have more control of the NAT'ing. Granted, it may be impractical for other reasons.
Of course, all this assumes you also have static routing configured properly on the WG server side (the use of NAT w/ the WG client is intended to make that unnecessary).
The other option is to reverse the roles of the WG connection, making the client the server, and vice versa, putting the client on the device where you presumably have more control of the NAT'ing. Granted, it may be impractical for other reasons.
ZebMcKayhan
Very Senior Member
This should already be taken care of when changing AllowedIPs (Server), a route in the main route table should been added for 192.168.10.0/24 to wgs1 (and wg will route to correct peer).Of course, all this assumes you also have static routing configured properly on the WG server side (the use of NAT w/ the WG client is intended to make that unnecessary).
I may be out on thin ice here, but this source:But I don´t know how to : to turn off nat (MASQUARADE) on GL Inet router
https://forum.gl-inet.com/t/wireguard-without-double-nat/16915/2
Suggests the only way is to change in the wireguard config file.
Another source:
https://forum.gl-inet.com/t/s2s-wir...bnet-without-nat-only-routes-possible/13773/2
Suggests the masquarade option is adjustable in the firewall zones area of the gui. However, you will need to re-arrange so lan-wan has masquarade enabled whilst lan-wireguard does not have it.
Both links are abit dated and may not be relevant anymore. But perhaps a starting point?
ZebMcKayhan
Very Senior Member
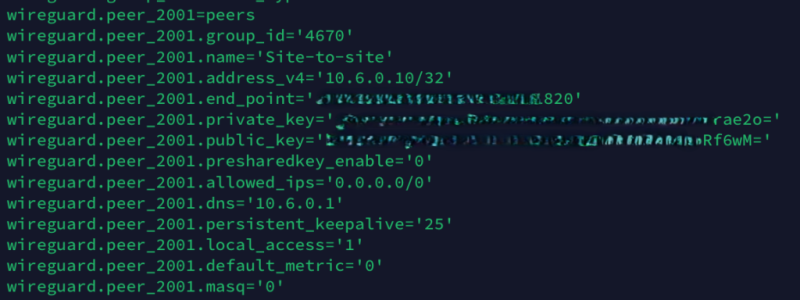
Looks like you don't have masquerading enabled for neither wan or Wireguard which may give issues if you have lan clients using wan.This is my configuration.
But did this resolve your issue or not?
Not. When I see connections on ADGUARD HOME I just see IP of WG not real IP of devices in other LAN (192.168.10.x)Looks like you don't have masquerading enabled for neither wan or Wireguard which may give issues if you have lan clients using wan.
But did this resolve your issue or not?
ZebMcKayhan
Very Senior Member
Then the Gl.Inet router is still masquerading... unless wireguard dns is setup to use router itself as forwarder for dns (dnsmasq).Not. When I see connections on ADGUARD HOME I just see IP of WG not real IP of devices in other LAN (192.168.10.x)
did you stop/start wireguard after making these changes? Or better yet, reboot the router?
As you already are familiar with ssh into the gl.inet router, could you try dumping firewall rules and if it's there we could try to remove it:
Code:
iptables -nvL POSTROUTING -t natI will check config wireguard but in SSH of gl.inet I have this:
Code:
root@GL-X750:~# iptables -nvL POSTROUTING -t nat
# Warning: iptables-legacy tables present, use iptables-legacy to see them
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
root@GL-X750:~#ZebMcKayhan
Very Senior Member
Aha, gl.inet router are using nftables... im not as familiar with those. You should be able to list them byI will check config wireguard but in SSH of gl.inet I have this:
Code:root@GL-X750:~# iptables -nvL POSTROUTING -t nat # Warning: iptables-legacy tables present, use iptables-legacy to see them Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination root@GL-X750:~#
Code:
nft list rulesetI cann´t copy all code, so I posted to pastebin:

 pastebin.com
pastebin.com

BusyBox v1.35.0 (2023-04-09 12:27:46 UTC) built-in shell (ash) _______ - Pastebin.com
Pastebin.com is the number one paste tool since 2002. Pastebin is a website where you can store text online for a set period of time.
Last edited:
Code:
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname { "eth0", "wwan0" } jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic"
}
chain srcnat_wan {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic"
}
Code:
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
}ZebMcKayhan
Very Senior Member
Great! Om not an expert in these but I don't see anything pointing to masquarade being used on wireguard anymore.Code:chain dstnat { type nat hook prerouting priority dstnat; policy accept; } chain srcnat { type nat hook postrouting priority srcnat; policy accept; oifname { "eth0", "wwan0" } jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic" } chain srcnat_wan { meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic" }
Code:chain mangle_postrouting { type filter hook postrouting priority mangle; policy accept; }
I think your gl.inet router processes dns requests locally by dnsmasq. So lan client sends dns to gl.inet router which either uses cached info or makes it's own request to upstream dns server (agh). Which is why you only see gl.inet router ip in agh log. You need to figure out how to bypass local dns resolution on the gl.inet router. You will probably get better help on a forum/section for these routers.
littlepopkaka
Occasional Visitor
I recently encountered this issue as well. In previous versions, I could access the DNS of the remote router through a VPN, but it doesn't seem possible anymore in version 388.8. Have you found a solution?
yes it works for me.

 forum.gl-inet.com
forum.gl-inet.com

VPN wireguard and Adguard Home
I modified it that should be: iptables -w -t nat -I PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.6.0.1 NOW IT WORKS!!!!!!! I can see in ADH devices connected to GL-X750
 forum.gl-inet.com
forum.gl-inet.com
ZebMcKayhan
Very Senior Member
Great you managed to sort this out, and thanks for the link!yes it works for me.

VPN wireguard and Adguard Home
I modified it that should be: iptables -w -t nat -I PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.6.0.1 NOW IT WORKS!!!!!!! I can see in ADH devices connected to GL-X750forum.gl-inet.com
Just a couple of notes:
- According to this post: https://forum.gl-inet.com/t/vpn-wireguard-and-adguard-home/45861/16 You added a static route in the asus router. This should not be needed as you added remote lan in AllowedIPs (server) and could be removed. I don't think it does any harm though but it does not look correctly formulated.
- The redirection rule you added:
Code:
iptables -w -t nat -I PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.6.0.1
Code:
iptables -w -t nat -I PREROUTING -i br-lan -p tcp --dport 53 -j DNAT --to 10.6.0.1Thanks. I add the line.Great you managed to sort this out, and thanks for the link!
Just a couple of notes:
- According to this post: https://forum.gl-inet.com/t/vpn-wireguard-and-adguard-home/45861/16 You added a static route in the asus router. This should not be needed as you added remote lan in AllowedIPs (server) and could be removed. I don't think it does any harm though but it does not look correctly formulated.
- The redirection rule you added:
Only covers udp dns packets, which most dns requests are, but not all. Some are tcp. For completeness you should also add:Code:iptables -w -t nat -I PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.6.0.1
Code:iptables -w -t nat -I PREROUTING -i br-lan -p tcp --dport 53 -j DNAT --to 10.6.0.1
Similar threads
- Replies
- 9
- Views
- 201
- Replies
- 14
- Views
- 822
- Replies
- 13
- Views
- 2K
Similar threads
Similar threads
-
pros and cons for the two common DNS setups for a local adblocker - adguard home
- Started by jata
- Replies: 25
-
AdGuard VPN (IPSec/IKEv2) not possible as VPN client on Asuswrt-Merlin?
- Started by XIII
- Replies: 1
-
-
-
Home Network Upgrade with RT-BE88U (Merlin) & AX-58U as AiMesh Node - Inputs ?
- Started by wrink
- Replies: 40
-
Going from Home to Small business (NAS+CCTV) - AiMesh and possible managed switch
- Started by keyboard99
- Replies: 8
-
-
Solved What VPN Director rule should i use to be able to connect outside my home to my VPN provider?
- Started by brodas
- Replies: 2
-
How would you go about syncing/symlinking root home folder to entware drive during system operation?
- Started by domic
- Replies: 12
Latest threads
-
-
Some wireless devices are unreachable from clients but are reachable from the router itself
- Started by itayt
- Replies: 2
-
RT-BE92U connections in AIMesh nodes intermittently dropped
- Started by TurboWG
- Replies: 2
-
-
BACKUPMON BACKUPMON installation instructions / tutorial
- Started by KrautHolg
- Replies: 8
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!