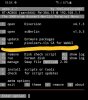
I saw this in syslog:
Aug 18 15:04:09 dnsmasq[1147]: bad name at /opt/share/diversion/list/blacklist line 369
So I navigated to the file and saw multiple identical entries like:
192.168.1.2 redir.metaservices.microsoft.com
192.168.1.2 redir.metaservices.microsoft.com # Entry added with W10Privacy (
www.winprivacy.de)!
192.168.1.2 reports.wes.df.telemetry.microsoft.com
192.168.1.2 reports.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (
www.winprivacy.de)!
192.168.1.2 reports.wes.df.telemetry.microsoft.com # Entry added with W10Privacy (
www.winprivacy.de)!
Can diversion sort these multiple identical entries somehow out?