Ranger802004
Very Senior Member
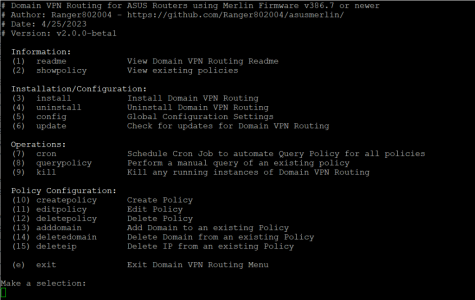
Domain VPN Routing is a tool used to route specific website domains to specific VPN tunnels or override all traffic being routed to a VPN tunnel to directly route through a WAN interface.
***v2.1.0 Release****
This is the release information regarding v2.1.0, please read the notes carefully prior to installing.
Considerations ***READ CAREFULLY***:
- Due to the configuration differences between v1.x and v2.x.x there are configuration changes made during the upgrade that will not allow the script to automatically be reverted back to v1.x, a back up of the original configuration is created under /jffs/configs/domain_vpn_routing/domain_vpn_routing.conf-<Datestamp>.bak and would have to be restored to be used if Domain VPN Routing is reverted back to v1.x.
- Domain VPN Routing will now use interface friendly names instead of actual interface names. Example: tun11 will be replaced by ovpnc1, eth0 will be replaced by wan0
- There is an option to select "wan" when using Dual WAN mode, this will essentially keep the domain routing tied to the primary WAN at any given time as opposed to wan0 / wan1 keeping the traffic bound to the specific interface.
- A new global configuration will be created during the upgrade, by default Dev Mode is Disabled during the creation. To enable you can use the new SSH UI Menu to enable in the Global Configuration Menu.
- Domain VPN Routing will now be called by wan-event script in addition to openvpn-event.
Readme - https://raw.githubusercontent.com/Ranger802004/asusmerlin/main/domain_vpn_routing/readme.txt
Script - https://raw.githubusercontent.com/R...main/domain_vpn_routing/domain_vpn_routing.sh
Install Command:
Upgrade from v1.x Command:
Release Notes:
v2.1.0 - 10/06/2023
Enhancements:
- DNSMasq log is now utilized if enabled to query for domain records to route. The log path will be captured from the DNSMasq Configuration.
- IPSets, IPTables Rules, and IP Rules using FWMarks have been implemented to reduce the amount of routes / rules that are created for policies.
- Added Check Interval configuration options to Configuration Menu to modify the cron job schedule between 1 - 59 minutes. Default: 15 minutes
- The current interface for a Policy will be displayed when in the Edit Policy configuration menu.
- Added default FWMark and Mask values for OpenVPN and WireGuard clients that can be changed in the configuration menu. Reboot required for changes.
- Log priority values added (Critical, Error, Warning, Notice, Informational, Debug)
- Additional logging messages have been added.
- Added Boot Delay Timer configuration setting to delay execution to wait and allow VPN tunnels to initalize during start up before querying for policies. Default: 0 Seconds
- Added Reset Default Configuration to Configuration Menu, additionally the command argument resetconfig can be used.
Fixes:
- Fixed an issue where adding a domain with the same partial name as an existing in a policy prevented it from being added.
- Fixed an issue that causes the update function to hang when complete as well as when terminating Domain VPN Routing.
- Fixed an issue preventing installation where Domain VPN Routing was trying to access the global configuration before it was created.
- Fixed an issue where the alias "domain_vpn_routing" was not being deleted during uninstallation.
- Fixed an issue where changing the Check Interval causes the Domain VPN Routing to hang on Query Policy screen instead of returning to Configuration Menu.
- Fixed an issue when editing a policy and changing the interface would cause a parameter not set error.
- Fixed an issue that wouldn't allow FWMark and Mask settings in the configuration to be null.
- Fixed an issue that caused uninstallation to prompt multiple times for confirmation during uninstall process.
- Fixed an issue that prevented the menu from loading when Domain VPN Routing was not installed.
***v2.1.0 Release****
This is the release information regarding v2.1.0, please read the notes carefully prior to installing.
Considerations ***READ CAREFULLY***:
- Due to the configuration differences between v1.x and v2.x.x there are configuration changes made during the upgrade that will not allow the script to automatically be reverted back to v1.x, a back up of the original configuration is created under /jffs/configs/domain_vpn_routing/domain_vpn_routing.conf-<Datestamp>.bak and would have to be restored to be used if Domain VPN Routing is reverted back to v1.x.
- Domain VPN Routing will now use interface friendly names instead of actual interface names. Example: tun11 will be replaced by ovpnc1, eth0 will be replaced by wan0
- There is an option to select "wan" when using Dual WAN mode, this will essentially keep the domain routing tied to the primary WAN at any given time as opposed to wan0 / wan1 keeping the traffic bound to the specific interface.
- A new global configuration will be created during the upgrade, by default Dev Mode is Disabled during the creation. To enable you can use the new SSH UI Menu to enable in the Global Configuration Menu.
- Domain VPN Routing will now be called by wan-event script in addition to openvpn-event.
Readme - https://raw.githubusercontent.com/Ranger802004/asusmerlin/main/domain_vpn_routing/readme.txt
Script - https://raw.githubusercontent.com/R...main/domain_vpn_routing/domain_vpn_routing.sh
Install Command:
Code:
/usr/sbin/curl -s "https://raw.githubusercontent.com/Ranger802004/asusmerlin/main/domain_vpn_routing/domain_vpn_routing.sh" -o "/jffs/scripts/domain_vpn_routing.sh" && chmod 755 /jffs/scripts/domain_vpn_routing.sh && sh /jffs/scripts/domain_vpn_routing.sh installUpgrade from v1.x Command:
Code:
/usr/sbin/curl -s "https://raw.githubusercontent.com/Ranger802004/asusmerlin/main/domain_vpn_routing/domain_vpn_routing.sh" -o "/jffs/scripts/domain_vpn_routing.sh" && chmod 755 /jffs/scripts/domain_vpn_routing.sh && sh /jffs/scripts/domain_vpn_routing.shRelease Notes:
v2.1.0 - 10/06/2023
Enhancements:
- DNSMasq log is now utilized if enabled to query for domain records to route. The log path will be captured from the DNSMasq Configuration.
- IPSets, IPTables Rules, and IP Rules using FWMarks have been implemented to reduce the amount of routes / rules that are created for policies.
- Added Check Interval configuration options to Configuration Menu to modify the cron job schedule between 1 - 59 minutes. Default: 15 minutes
- The current interface for a Policy will be displayed when in the Edit Policy configuration menu.
- Added default FWMark and Mask values for OpenVPN and WireGuard clients that can be changed in the configuration menu. Reboot required for changes.
- Log priority values added (Critical, Error, Warning, Notice, Informational, Debug)
- Additional logging messages have been added.
- Added Boot Delay Timer configuration setting to delay execution to wait and allow VPN tunnels to initalize during start up before querying for policies. Default: 0 Seconds
- Added Reset Default Configuration to Configuration Menu, additionally the command argument resetconfig can be used.
Fixes:
- Fixed an issue where adding a domain with the same partial name as an existing in a policy prevented it from being added.
- Fixed an issue that causes the update function to hang when complete as well as when terminating Domain VPN Routing.
- Fixed an issue preventing installation where Domain VPN Routing was trying to access the global configuration before it was created.
- Fixed an issue where the alias "domain_vpn_routing" was not being deleted during uninstallation.
- Fixed an issue where changing the Check Interval causes the Domain VPN Routing to hang on Query Policy screen instead of returning to Configuration Menu.
- Fixed an issue when editing a policy and changing the interface would cause a parameter not set error.
- Fixed an issue that wouldn't allow FWMark and Mask settings in the configuration to be null.
- Fixed an issue that caused uninstallation to prompt multiple times for confirmation during uninstall process.
- Fixed an issue that prevented the menu from loading when Domain VPN Routing was not installed.
Attachments
Last edited: