Xentrk
Part of the Furniture
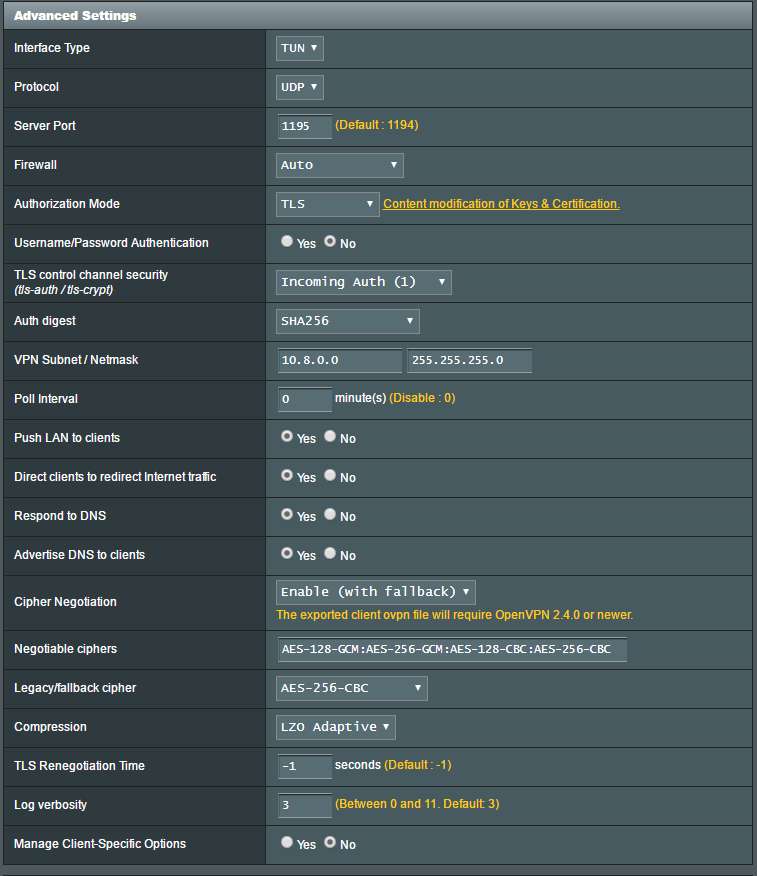
Can you draw up a simple network diagram and post it here?Thanks! I did make those changes to upgrade security from password only however I still cannot connect to a local machine. I am using an ip so can't be a DNS issue. Within my local network I can hit the 192.168.1.5 machine from 192.168.3, and both are behind PIA. But when I connect with my cell phone to this OpenVPN server, it connects properly, but I cannot hit 192.168.1.3 from the assigned 10.8.0.2. Is there a manual route that needs added to connect the two?