kamoj
Very Senior Member
Thank you as always for your good reporting!Hello,
I installed 5.4b32 on my R9000. I was unable to get VPN bypassing to work and I had to try several times to get AdGuard to install/start (which it eventually did). I assume it is something relating to my system. I didn't see anything in the logs that stuck out, however I was unable to download the Kamoj or Voxel information from the System Information page. Everything else seemed OK. Things I tried:
- A restart of the router, cleaning the browser cache on the machine I was using and restarting the machine.
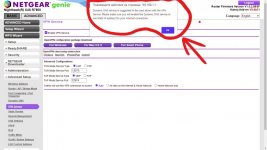
- Clearing the VPN bypassing by moving items back to non-bypassed and clicking the clear bypassing from NVRAM buttons.
- Uninstall 5.4b32. Factory reset router, reinstall the current Voxel firmware and 5.4b32
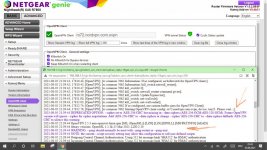
The ip rule display on the VPN bypass page showed nothing was being bypassed no matter what I did...and checking the ip of several devices using curl confirmed devices in the bypass selection list were still using the VPN.
As I needed to get the router going again, I reinstalled 5.4b31. Everything worked as it should on 5.4b31 except I was still unable to download the Voxel release notes, Kamoj release notes or Kamoj FAQ. Downloading the Aegis info, etc., still worked.
Didn't have time to check further, but thought I would pass this along as I won't be able to hop back on here for a while.
Best wishes,
BL
The downloading probably times out for you. What timeout do you use for downloads?
Don't know what about the bypassing is about.
Wish you had taken a screen dump of Router Information page. Its very informative...