Don Draper
Occasional Visitor
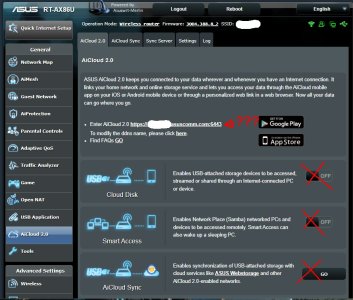
Similar issue - losing WAN access repeatedly, router crashing. Reset and rebuilt multiple times. New modem from ISP, new cables, new AX86U through warranty. Still occurring until disabling of AiCloud. Odd thing is while monitoring logs a line regarding tainted PPTP VPN caught my eye. I have never enabled the PPTP VPN ...I may have flipped the switch by accident while configuring WireGuard or something one of the hundred times I factory reset and rebuilt this past month. Disabling AiCloud has since solved my issue, but it's been less than 24hrs. Changed 26 character router login, DDNS, eliminated port forwarding.