E:Option ==> debug
WireGuard ACTIVE Peer Status: Clients 0, Servers 0
1 = Update Wireguard modules 7 = Display QR code for a Peer {device} e.g. iPhone
2 = Remove WireGuard/wg_manager 8 = Peer management [ "list" | "category" | "new" ] | [ {Peer | category} [ del | show | add [{"auto="[y|n|p]}] ]
9 = Create Key-pair for Peer {Device} e.g. Nokia6310i (creates Nokia6310i.conf etc.)
3 = List ACTIVE Peers Summary [Peer...] [full] 10 = IPSet management [ "list" ] | [ "upd" { ipset [ "fwmark" {fwmark} ] | [ "enable" {"y"|"n"}] | [ "dstsrc"] ] } ]
4 = Start [ [Peer [nopolicy]...] | category ] e.g. start clients
5 = Stop [ [Peer... ] | category ] e.g. stop clients
6 = Restart [ [Peer... ] | category ] e.g. restart servers
? = About Configuration
v = View ('/jffs/addons/wireguard/WireguardVPN.conf')
e = Exit Script [?]
E

ebug mode enabledOption ==> peer wg11 auto=y
+ printf %s peer wg11 auto=y+ sed s/^[ \t]*//;s/[ \t]*$//
+ menu1=peer wg11 auto=y
+ Validate_User_Choice peer wg11 auto=y
+ local menu1=peer wg11 auto=y
+ [ Y == Y ]
+ echo peer wg11 auto=y
+ awk {$1="peer"}1
+ menu1=peer wg11 auto=y
+ echo peer wg11 auto=y
+ menu1=peer wg11 auto=y
+ Process_User_Choice peer wg11 auto=y
+ local menu1=peer wg11 auto=y
+ Manage_Peer peer wg11 auto=y
+ local ACTION=peer
+ shift
+ WG_INTERFACE=wg11
+ shift
+ local CMD=auto=y
+ [ wg11 == new ]
+ [ wg11 == newC ]
+ [ wg11 == help ]
+ [ -z auto=y ]
+ echo auto=y+ grep -iw ipset
+ [ -n ]
+ [ auto=y == help ]
+ local FN=/jffs/addons/wireguard/WireguardVPN.confXXX
+ [ wg11 == new ]
+ [ wg11 == newC ]
+ [ wg11 == add ]
+ [ wg11 != category ]
+ [ auto=y == import ]
+ [ auto=y == delX ]
+ [ auto=y == new ]
+ [ auto=y == add ]
+ [ -f /opt/etc/wireguard.d/wg11.conf ]
+ echo auto=y
+ awk -F = {print $2}
+ local AUTO=y
+ echo y
+ grep ^[yYnNpP]$
+ [ y ]
+ echo y
+ tr a-z A-Z
+ FLAG=Y
+ [ wg1 == wg2 ]
+ TABLE=clients
+ sqlite3 /opt/etc/wireguard.d/WireGuard.db UPDATE clients SET auto='Y' WHERE peer='wg11';
+ echo -e \e[92m\n\t[✔] Updated AUTO=Y:\n\e[0m
[✔] Updated AUTO=Y:
+ [ Y == P ]
+ set +x
WireGuard ACTIVE Peer Status: Clients 0, Servers 0
1 = Update Wireguard modules 7 = Display QR code for a Peer {device} e.g. iPhone
2 = Remove WireGuard/wg_manager 8 = Peer management [ "list" | "category" | "new" ] | [ {Peer | category} [ del | show | add [{"auto="[y|n|p]}] ]
9 = Create Key-pair for Peer {Device} e.g. Nokia6310i (creates Nokia6310i.conf etc.)
3 = List ACTIVE Peers Summary [Peer...] [full] 10 = IPSet management [ "list" ] | [ "upd" { ipset [ "fwmark" {fwmark} ] | [ "enable" {"y"|"n"}] | [ "dstsrc"] ] } ]
4 = Start [ [Peer [nopolicy]...] | category ] e.g. start clients
5 = Stop [ [Peer... ] | category ] e.g. stop clients
6 = Restart [ [Peer... ] | category ] e.g. restart servers
? = About Configuration
v = View ('/jffs/addons/wireguard/WireguardVPN.conf')
e = Exit Script [?]
E

ebug mode enabledOption ==> 8
+ printf %s 8
+ sed s/^[ \t]*//;s/[ \t]*$//
+ menu1=8
+ Validate_User_Choice 8
+ local menu1=8
+ [ Y == Y ]
+ echo 8
+ awk {$1="peer"}1
+ menu1=peer
+ echo peer
+ menu1=peer
+ Process_User_Choice peer
+ local menu1=peer
+ Manage_Peer peer
+ local ACTION=peer
+ shift
+ WG_INTERFACE=
+ shift
+ local CMD=
+ [ == new ]
+ [ == newC ]
+ [ == help ]
+ [ -z ]
+ CMD=list
+ echo
+ grep -iw ipset
+ [ -n ]
+ [ != category ]
+ Show_Peer_Config_Entry
+ local WG_INTERFACE=
+ echo -e \e[97m\n\tPeers (Auto=P - Policy, Auto=X - External i.e. Cell/Mobile)\e[96m
Peers (Auto=P - Policy, Auto=X - External i.e. Cell/Mobile)
+ COLUMN_TXT=Server,Auto,Subnet,Port,Annotate
+ sqlite3 /opt/etc/wireguard.d/WireGuard.db SELECT peer,auto,subnet,port,tag from servers;
+ column -t -s | --table-columns Server,Auto,Subnet,Port,Annotate
Server Auto Subnet Port Annotate
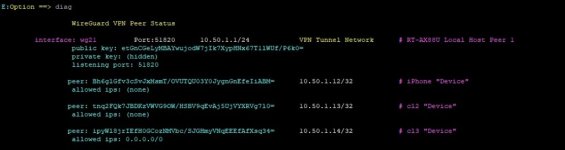
wg21 Y 10.50.1.1/24 51820 # RT-AC86U Server #1
+ echo -e
+ COLUMN_TXT=Client,Auto,IP,Endpoint,DNS,Annotate
+ sqlite3 /opt/etc/wireguard.d/WireGuard.db SELECT peer,auto,subnet,socket,dns,tag from clients;
+ column -t -s | --table-columns Client,Auto,IP,Endpoint,DNS,Annotate
+ echo -e
+ COLUMN_TXT=Device,Auto,IP,DNS,Allowed IP,Annotate
+ sqlite3 /opt/etc/wireguard.d/WireGuard.db SELECT name,auto,ip,dns,allowedip,tag from devices;
+ column -t -s | --table-columns Device,Auto,IP,DNS,Allowed IP,Annotate
Device Auto IP DNS Allowed IP Annotate
ubimo X 172.16.0.2/32 1.1.1.1 0.0.0.0/0 # Cloudflare Warp
+ echo -en \e[0m
+ set +x
WireGuard ACTIVE Peer Status: Clients 0, Servers 0