v4.3.4
Updated 2021-08-04
Feature expansion of guest WiFi networks on AsusWRT-Merlin, including, but not limited to:
* Dedicated VPN WiFi networks
* Separate subnets for organisation of devices
* Restrict guests to only contact router for ICMP, DHCP, DNS, NTP and NetBIOS
* Allow guest networks to make use of pixelserv-tls (if installed)
* Allow guests to use a local DNS server
* Extend DNS Filter to guest networks
This project is hosted on
GitHub
YazFi is free to use under the
GNU General Public License version 3 (GPL 3.0).
Love the script and want to support future development? Any and all donations gratefully received!
PayPal donation
Buy me a coffee
Supported firmware versions
Core YazFi features
You must be running firmware no older than:
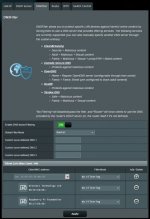
WebUI page for YazFi
You must be running firmware no older than:
Installation
Using your preferred SSH client/terminal, copy and paste the following command, then press Enter:
Code:
/usr/sbin/curl --retry 3 "https://raw.githubusercontent.com/jackyaz/YazFi/master/YazFi.sh" -o "/jffs/scripts/YazFi" && chmod 0755 /jffs/scripts/YazFi && /jffs/scripts/YazFi install
Please then follow instructions shown on-screen. An explanation of the settings is provided in the FAQs in
post #2
Usage
WebUI
YazFi can be configured via the WebUI, in the Guest Network section.
Command Line
To launch the YazFi menu after installation, use:
If you do not have Entware installed, you will need to use the full path: