Stephen Harrington
Very Senior Member
First boot post upgrade, I needed to change the VPN Client > Redirect Internet traffic through tunnel setting to VPN Director (policy rules) as it was initially set to No. Once this adjustment was made, everything worked fine and the VPN Director settings appear to be functioning as expected.
Had a similar experience but not quite the same when I upgraded to the Beta today.
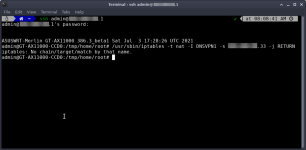
I only have one device/one IP routed via Policy Rules through my NordVPN OpenVPN Client 1, my Synology NAS.
Initially after the upgrade "Redirect Internet Traffic Through Tunnel" was set to "VPN Director (policy rules)" which was as expected given my pre-upgrade setup with the "old style" Policy Rules.
However the VPN wasn't routing any data, despite it looking to be "up" and giving it a nudge by restarting it.
I had to set "Redirect Internet Traffic Through Tunnel" to "No", then hit "Apply", then set it back to "VPN Director (policy rules)" and hit "Apply".
After another restart of OpenVPN Client 1 it all came good, and has been fine through a couple of reboots I did to check.
Just a minor glitch in the upgrade process, but worth noting for others who may follow?