New release with a few additions, enhancements and bugfixes! Many thanks to
@Martinski for his excellent work on the shared Email library, and huge props to
@ExtremeFiretop for wearing down his patience with me formally adopting the crazy complex ways of the ins&outs of Github!

This is the first official release made where development environment code was formally pulled into the main environment... voila, magic. LOL I just hope I can replicate this setup to my other projects.
What's new?
v1.5.9 - (February 21, 2024)
- PATCH: Thanks to
@Martinski, some
significant improvements were made to the email notification feature and functionality. HTML emails are now being sent by default, and have been tested using all major email providers. A new title header is now visible in the email, as well as the ability to bold characters. Looking at adding a secondary email address in the near future as that capability has now been built-in as well, which could optionally be used for text messaging.
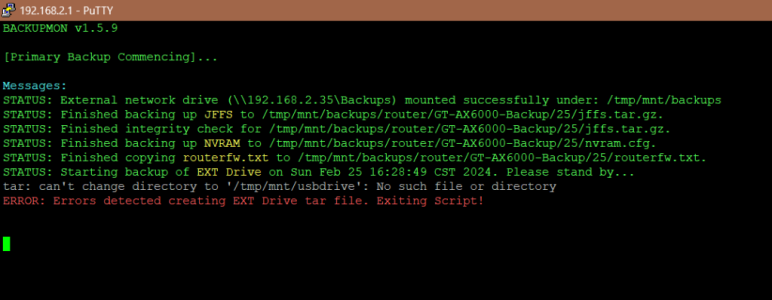
- PATCH: Noticed that when the "scheduled backup" item was set to "No", that one of its sub-items continued to stay active. Now, when this item is set to "No", both the
time and backup modes are grayed out.
- PATCH: The update logic now
pulls the backupmon.sh directly from github starting from versions after 1.5.9, instead of the backupmon-X.Y.Z.sh file based on the version number from the version.txt file.
Download link (or update directly within AMTM/BACKUPMON):
Code:
curl --retry 3 "https://raw.githubusercontent.com/ViktorJp/BACKUPMON/master/backupmon.sh" -o "/jffs/scripts/backupmon.sh" && chmod 755 "/jffs/scripts/backupmon.sh"
Significant Screenshots:
Behold, a new fresh HTML email for your BACKUPMON notifications:
View attachment 56657