KILLMON KILLMON v1.1.2 -Feb 29, 2024- IP4/IP6 VPN Kill Switch Monitor & Configurator (Now available in AMTM!)
- Thread starter Viktor Jaep
- Start date
Viktor Jaep
Part of the Furniture
Sorry... it just applies the iptables rules on startup... doesn't really have much to do with vpn connection/dialup unfortunately.Hi, is there a trick how the reboot protection works if the Asus doesn't do PPPoE dial-up?
Unfortunately I have problems so I let the Vigor do the dial-up and unfortunately the VPN no longer connects after the forced disconnection
OK, do you have an idea how I can tell my VPN connection to try to reconnect?Sorry... it just applies the iptables rules on startup... doesn't really have much to do with vpn connection/dialup unfortunately.
Viktor Jaep
Part of the Furniture
You could use a tool like VPNMON-R3 or some other custom script to try to start services on reboot?OK, do you have an idea how I can tell my VPN connection to try to reconnect?
I'm going to test VPNMON. I'm a newbie in this areaYou could use a tool like VPNMON-R3 or some other custom script to try to start services on reboot?
Jack-Sparr0w
Regular Contributor
Viktor Jaep
Part of the Furniture
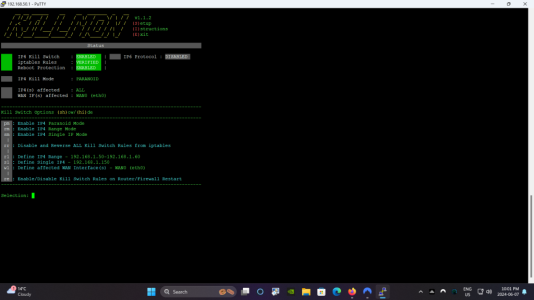
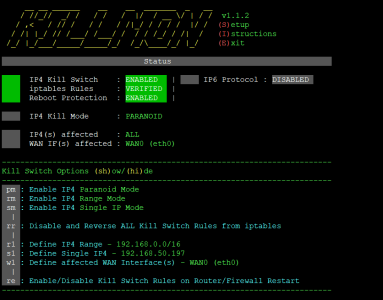
Congrats on enabling paranoid mode!New to this, does this look right
Jack-Sparr0w
Regular Contributor
Thank you again, is this the most secure way to use range mode. i have nordvpn and skynet
Viktor Jaep
Part of the Furniture
Paranoid mode blocks everything. If you only need 192.168.1.50 - 192.168.1.60 blocked, you would use range mode. And everything that falls between that range would get blocked. I use Nord and Skynet as well... so just be aware, if you make big changes to Skynet, upgrade it, what not... that will cause iptables to get reset, and you would need to re-enable killmon. Just keep an eye on it. I have plans in the future to make it a bit more automated, and have it do stuff like this on its own.Thank you again, is this the most secure way to use range mode. i have nordvpn and skynet
Last edited:
Caesar the Dictator
Regular Contributor
Hello! Asuswrt-Merlin firmware (388.8) will soon feature an upgraded VPN kill switch. How the upgraded VPN kill switch will work is briefly described here, what I read there made me think that it will now work like KILLMON. Will people who will be using the new Asuswrt-Merlin firmware in the future be able to continue using KILLMON, or will Merlin's built-in kill switch be enough for them?
- NEW: Rewrote VPN killswitch implementation. The new method
uses an always present routing rule to prohibit access to
the main routing table, so it will be active even if the
user manually stops a client. Removing the prohibit rule
requires disabling the killswitch on the webui.
The rules are also created before WAN goes up, to reduce
the risks of leaks between WAN going up and VPN connecting.
- NEW: Added killswitch support for WireGuard clients.
Last edited:
Viktor Jaep
Part of the Furniture
I'm with you. I'm hoping the built-in Killswitch will be enough in order to not need KILLMON any longer. Would love to see it in action. I believe he also said that there were plans to bring it over to the 3004 lineup as well. I'll probably keep the script updated until that time to continue supporting the 3004 lineup until it's no longer needed.Hello! Asuswrt-Merlin firmware (388.8) will soon feature an upgraded VPN kill switch. How the upgraded VPN kill switch will work is briefly described here, what I read there made me think that it will now work like KILLMON. Will people who will be using the new Asuswrt-Merlin firmware in the future be able to continue using KILLMON, or will Merlin's built-in kill switch be enough for them?
Jack-Sparr0w
Regular Contributor
Viktor Jaep
Part of the Furniture
That would definitely need to be tested. The only examples I have ever been able to find show that the iptables command can only handle an IP range in its own subnet... Like 192.168.1.50 - 192.168.1.100. You would likely have more luck with the CIDR notation (192.168.0.0/16), but that also eliminates any precision in the range.With guest networks, would the range 192.168.1.50-192.168.102.60 be a safer option globally.
While it looks nice to keep things separate in their own subnets... is it realistic that you might possibly have to dish out 250 addresses in each of those guest networks? Or do you think you can find 10 for each, and fold everything into your 192.168.1.x network? That would probably be more realistic.
Last edited:
Jack-Sparr0w
Regular Contributor
I have been testing it, seems that router is snappier and no issues with Skynet restarting. I figure it must be the same range due to it being a 192 address. Guest networks use the vpn too. also would it be possible to disable wifi access and use only guest access wifi, or a script to get rid of mesh abilities of router. If that is even possible. I've seen flipper zero goes through wpa2 like its nothing.
Viktor Jaep
Part of the Furniture
Could you please explain more what you're envisioning when you lose a VPN connection, preventing access to the WAN?I have been testing it, seems that router is snappier and no issues with Skynet restarting. I figure it must be the same range due to it being a 192 address. Guest networks use the vpn too. also would it be possible to disable wifi access and use only guest access wifi, or a script to get rid of mesh abilities of router. If that is even possible. I've seen flipper zero goes through wpa2 like its nothing.
Jack-Sparr0w
Regular Contributor
guest networks uses 192.168.50.2.254-192.168.50.102.254, I don't think the kill switch covers that unless it entered in vpn director manually. due to guest network being used with vpn I thought it would be a good move.
Jack-Sparr0w
Regular Contributor
I see now sorry I had to get someone to explain it to me, CIDR notation 192.168.0.0/16 is best. Thank you again
Jack-Sparr0w
Regular Contributor
Viktor Jaep
Part of the Furniture
A single IP would be the only IP blocked by the Killswitch if your VPN goes down. That means everything else will be able to get out over the WAN. I believe in your case, you were leaning more towards using it for a range with a /16 CIDR subnet, right?Last thing before I go, 192.168.50.1 is my network, and ipv4 only network. Is the single ip 192.168.50.197 best for this type of setup. Again thank you, Pretty new to this.
Jack-Sparr0w
Regular Contributor
yes
Similar threads
- Replies
- 48
- Views
- 3K
- Replies
- 7
- Views
- 2K
DomainVPNRouting
Domain VPN Routing v3.1.0 ***Release***
- Replies
- 89
- Views
- 8K
Similar threads
Similar threads
-
uiDivStats uiDivstats 4.0.9 - WebUI Stats for Diversion, Feb. 12, 2025
- Started by thelonelycoder
- Replies: 84
-
Entware Entware repository update: August 8, 2024
- Started by thelonelycoder
- Replies: 21
-
TAILMON TAILMON v1.0.20 -July 27, 2024- WireGuard-based Tailscale Installer, Configurator and Monitor (THREAD #1 CLOSED)
- Started by Viktor Jaep
- Replies: 556
Latest threads
-
-
-
Need help with ASUS GT AXE 2.4Ghz band WIFI
- Started by Chunjaa
- Replies: 7
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!