Jeffrey Young
Very Senior Member
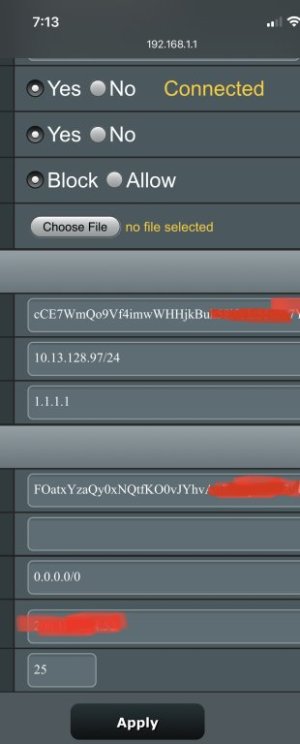
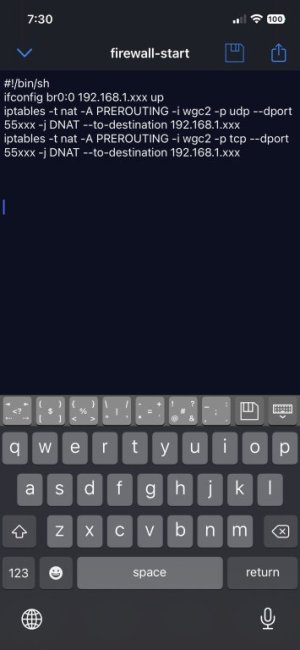
The NAT rules should go in the nat-start script. The ifconfig can stay in firewall-start script.I was able to open the port on the fireguard vpn using the following lines only in firewall-start
ifconfig br0:0 192.168.1.xxx up
iptables -t nat -A PREROUTING -i wgc2 -p udp --dport 55xxx -j DNAT --to-destination 192.168.1.xxx
iptables -t nat -A PREROUTING -i wgc2 -p tcp --dport 55xxx -j DNAT --to-destination 192.168.1.xxx
@Jeffrey Young do I still need to put the delete rules with the above lines?
Yes, you should include the delete (-D) rules above your insert rules so as not to create a bunch of duplicates rules should the script get called multiple times.
By wireguard very nature, a kill switch is not possible.
EDIT: perhaps we can rewind and you explain exactly what you are trying to achieve. The reason for setting up an alias IP on the br0 bridge is confusing me.
Last edited: