AntonK
Very Senior Member
Nothing wrong there if you want Quad9.
Thanks! Yes, I've been a Quad9 man for some time now. Just turned on the D0T feature though, so wasn't sure if I still needed the WAN DNS boxes filled in.
Anton
Nothing wrong there if you want Quad9.
You can put any public DNS including your ISP DNS in the WAN DNS settings, just don't use the router IP.Thanks! Yes, I've been a Quad9 man for some time now. Just turned on the D0T feature though, so wasn't sure if I still needed the WAN DNS boxes filled in.
Anton
kdig -d @1.1.1.1 +tls-ca +dnssec +cd +tls-host=cloudflare-dns.com example.com
;; DEBUG: Querying for owner(example.com.), class(1), type(1), server(1.1.1.1), port(853), protocol(TCP)
;; DEBUG: TLS, imported 128 system certificates
;; DEBUG: TLS, received certificate hierarchy:
;; DEBUG: #1, C=US,ST=California,L=San Francisco,O=Cloudflare\, Inc.,CN=cloudflare-dns.com
;; DEBUG: SHA-256 PIN: V6zes8hHBVwUECsHf7uV5xGM7dj3uMXIS9//7qC8+jU=
;; DEBUG: #2, C=US,O=DigiCert Inc,CN=DigiCert ECC Secure Server CA
;; DEBUG: SHA-256 PIN: PZXN3lRAy+8tBKk2Ox6F7jIlnzr2Yzmwqc3JnyfXoCw=
;; DEBUG: TLS, skipping certificate PIN check
;; DEBUG: TLS, The certificate is trusted.
;; TLS session (TLS1.3)-(ECDHE-SECP256R1)-(ECDSA-SECP256R1-SHA256)-(AES-256-GCM)
;; ->>HEADER<<- opcode: QUERY; status: NOERROR; id: 25410
;; Flags: qr rd ra cd; QUERY: 1; ANSWER: 2; AUTHORITY: 0; ADDITIONAL: 1
;; EDNS PSEUDOSECTION:
;; Version: 0; flags: do; UDP size: 1452 B; ext-rcode: NOERROR
;; PADDING: 25 B
;; QUESTION SECTION:
;; example.com. IN A
;; ANSWER SECTION:
example.com. 980 IN A 93.184.216.34
example.com. 980 IN RRSIG A 8 2 86400 20190508112335 20190417064725 63195 example.com. V6Y2fQ7Kwgs0IX3wBSsORH6iSYAdfvj8urqEPaRDENgpH8WS21UNZHWjbUYLAKxhxknzKNTF7mpwKq3GX3sfAdpBpcNVHaovvv+pH2UDte3TCnEtXLo5EoN+fELCcI+Y4skZii9qsvSkFLIQmVo31KJtxZr2bvb59NyMnlINq/c=
;; Received 256 B
;; Time 2019-04-25 17:36:09 CST
;; From 1.1.1.1@853(TCP) in 84.0 mskdig -d @1.1.1.1 +tls-ca +dnssec +tls-host=cloudflare-dns.com example.com
;; DEBUG: Querying for owner(example.com.), class(1), type(1), server(1.1.1.1), port(853), protocol(TCP)
;; DEBUG: TLS, imported 128 system certificates
;; DEBUG: TLS, received certificate hierarchy:
;; DEBUG: #1, C=US,ST=California,L=San Francisco,O=Cloudflare\, Inc.,CN=cloudflare-dns.com
;; DEBUG: SHA-256 PIN: V6zes8hHBVwUECsHf7uV5xGM7dj3uMXIS9//7qC8+jU=
;; DEBUG: #2, C=US,O=DigiCert Inc,CN=DigiCert ECC Secure Server CA
;; DEBUG: SHA-256 PIN: PZXN3lRAy+8tBKk2Ox6F7jIlnzr2Yzmwqc3JnyfXoCw=
;; DEBUG: TLS, skipping certificate PIN check
;; DEBUG: TLS, The certificate is trusted.
;; TLS session (TLS1.3)-(ECDHE-SECP256R1)-(ECDSA-SECP256R1-SHA256)-(AES-256-GCM)
;; ->>HEADER<<- opcode: QUERY; status: NOERROR; id: 14005
;; Flags: qr rd ra ad; QUERY: 1; ANSWER: 2; AUTHORITY: 0; ADDITIONAL: 1
;; EDNS PSEUDOSECTION:
;; Version: 0; flags: do; UDP size: 1452 B; ext-rcode: NOERROR
;; PADDING: 25 B
;; QUESTION SECTION:
;; example.com. IN A
;; ANSWER SECTION:
example.com. 909 IN A 93.184.216.34
example.com. 909 IN RRSIG A 8 2 86400 20190508112335 20190417064725 63195 example.com. V6Y2fQ7Kwgs0IX3wBSsORH6iSYAdfvj8urqEPaRDENgpH8WS21UNZHWjbUYLAKxhxknzKNTF7mpwKq3GX3sfAdpBpcNVHaovvv+pH2UDte3TCnEtXLo5EoN+fELCcI+Y4skZii9qsvSkFLIQmVo31KJtxZr2bvb59NyMnlINq/c=
;; Received 256 B
;; Time 2019-04-25 17:37:20 CST
;; From 1.1.1.1@853(TCP) in 83.9 msYou can put any public DNS including your ISP DNS in the WAN DNS settings, just don't use the router IP.
Sure, but bear in mind the circumstances when these addresses would be used is few and far between, as revealed in past posts.Could the VPN DNS servers go there as well? Long time ago (pre-Stubby) that is I used to have there and everything worked just fine.
Sent from my iPhone using Tapatalk
Sure, but bear in mind the circumstances when these addresses would be used is few and far between, as revealed in past posts.
Hi,
Does this setup look right, to those who know what "right" means?
Thanks,
Anton
I ran two KDIG tests one with the +cd switch and one without.
With:
And without:Code:kdig -d @1.1.1.1 +tls-ca +dnssec +cd +tls-host=cloudflare-dns.com example.com ;; DEBUG: Querying for owner(example.com.), class(1), type(1), server(1.1.1.1), port(853), protocol(TCP) ;; DEBUG: TLS, imported 128 system certificates ;; DEBUG: TLS, received certificate hierarchy: ;; DEBUG: #1, C=US,ST=California,L=San Francisco,O=Cloudflare\, Inc.,CN=cloudflare-dns.com ;; DEBUG: SHA-256 PIN: V6zes8hHBVwUECsHf7uV5xGM7dj3uMXIS9//7qC8+jU= ;; DEBUG: #2, C=US,O=DigiCert Inc,CN=DigiCert ECC Secure Server CA ;; DEBUG: SHA-256 PIN: PZXN3lRAy+8tBKk2Ox6F7jIlnzr2Yzmwqc3JnyfXoCw= ;; DEBUG: TLS, skipping certificate PIN check ;; DEBUG: TLS, The certificate is trusted. ;; TLS session (TLS1.3)-(ECDHE-SECP256R1)-(ECDSA-SECP256R1-SHA256)-(AES-256-GCM) ;; ->>HEADER<<- opcode: QUERY; status: NOERROR; id: 25410 ;; Flags: qr rd ra cd; QUERY: 1; ANSWER: 2; AUTHORITY: 0; ADDITIONAL: 1 ;; EDNS PSEUDOSECTION: ;; Version: 0; flags: do; UDP size: 1452 B; ext-rcode: NOERROR ;; PADDING: 25 B ;; QUESTION SECTION: ;; example.com. IN A ;; ANSWER SECTION: example.com. 980 IN A 93.184.216.34 example.com. 980 IN RRSIG A 8 2 86400 20190508112335 20190417064725 63195 example.com. V6Y2fQ7Kwgs0IX3wBSsORH6iSYAdfvj8urqEPaRDENgpH8WS21UNZHWjbUYLAKxhxknzKNTF7mpwKq3GX3sfAdpBpcNVHaovvv+pH2UDte3TCnEtXLo5EoN+fELCcI+Y4skZii9qsvSkFLIQmVo31KJtxZr2bvb59NyMnlINq/c= ;; Received 256 B ;; Time 2019-04-25 17:36:09 CST ;; From 1.1.1.1@853(TCP) in 84.0 ms
The +cd seems to mess the test up. The "ad" flag shows in the second test.Code:kdig -d @1.1.1.1 +tls-ca +dnssec +tls-host=cloudflare-dns.com example.com ;; DEBUG: Querying for owner(example.com.), class(1), type(1), server(1.1.1.1), port(853), protocol(TCP) ;; DEBUG: TLS, imported 128 system certificates ;; DEBUG: TLS, received certificate hierarchy: ;; DEBUG: #1, C=US,ST=California,L=San Francisco,O=Cloudflare\, Inc.,CN=cloudflare-dns.com ;; DEBUG: SHA-256 PIN: V6zes8hHBVwUECsHf7uV5xGM7dj3uMXIS9//7qC8+jU= ;; DEBUG: #2, C=US,O=DigiCert Inc,CN=DigiCert ECC Secure Server CA ;; DEBUG: SHA-256 PIN: PZXN3lRAy+8tBKk2Ox6F7jIlnzr2Yzmwqc3JnyfXoCw= ;; DEBUG: TLS, skipping certificate PIN check ;; DEBUG: TLS, The certificate is trusted. ;; TLS session (TLS1.3)-(ECDHE-SECP256R1)-(ECDSA-SECP256R1-SHA256)-(AES-256-GCM) ;; ->>HEADER<<- opcode: QUERY; status: NOERROR; id: 14005 ;; Flags: qr rd ra ad; QUERY: 1; ANSWER: 2; AUTHORITY: 0; ADDITIONAL: 1 ;; EDNS PSEUDOSECTION: ;; Version: 0; flags: do; UDP size: 1452 B; ext-rcode: NOERROR ;; PADDING: 25 B ;; QUESTION SECTION: ;; example.com. IN A ;; ANSWER SECTION: example.com. 909 IN A 93.184.216.34 example.com. 909 IN RRSIG A 8 2 86400 20190508112335 20190417064725 63195 example.com. V6Y2fQ7Kwgs0IX3wBSsORH6iSYAdfvj8urqEPaRDENgpH8WS21UNZHWjbUYLAKxhxknzKNTF7mpwKq3GX3sfAdpBpcNVHaovvv+pH2UDte3TCnEtXLo5EoN+fELCcI+Y4skZii9qsvSkFLIQmVo31KJtxZr2bvb59NyMnlINq/c= ;; Received 256 B ;; Time 2019-04-25 17:37:20 CST ;; From 1.1.1.1@853(TCP) in 83.9 ms
Add the second quad9 secure server at 149.112.112.112Hi,
Does this setup look right, to those who know what "right" means?
Thanks,
Anton
Exact same result here after implementation ( https://www.cloudflare.com/ssl/encrypted-sni/ ).I’ve been following this thread to learn about DNS over TLS. I have found it helpful also somewhat confusing so I decided to have a play but wasn’t sure it was working properly. After some googling I believe I have it set up correctly
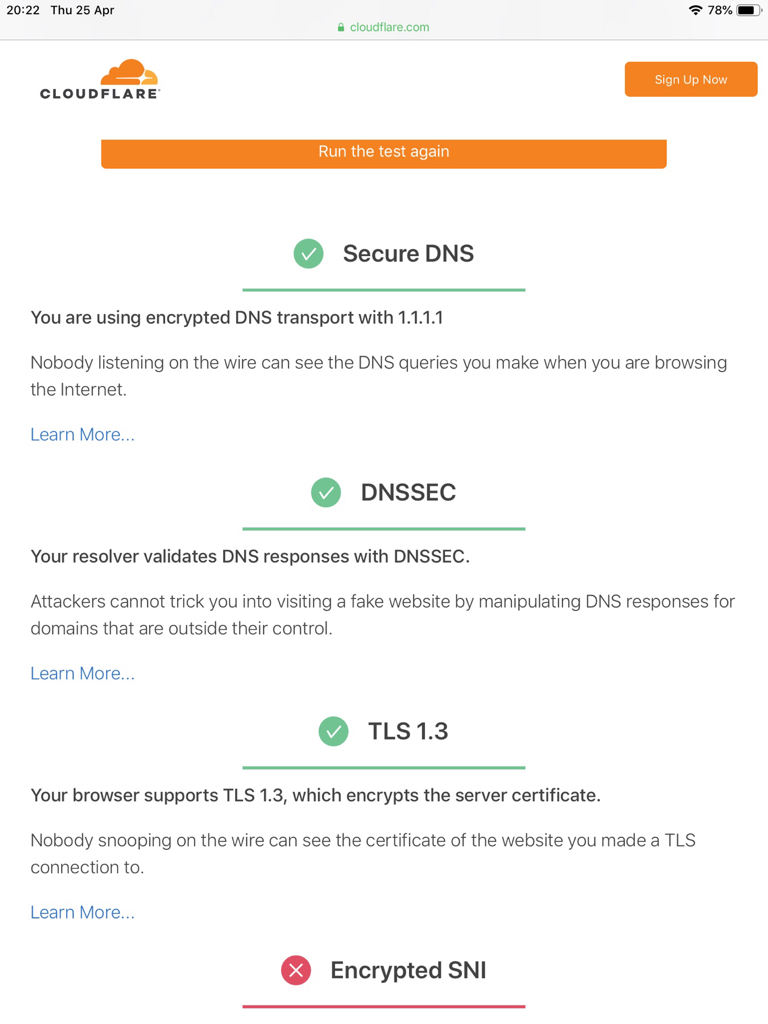
Sent from my iPad using Tapatalk
Exact same result here after implementation ( https://www.cloudflare.com/ssl/encrypted-sni/ ).
I don't know the why's on the Encrypted SNI fail. Read some, but no real clarity yet...
RT AC-5300
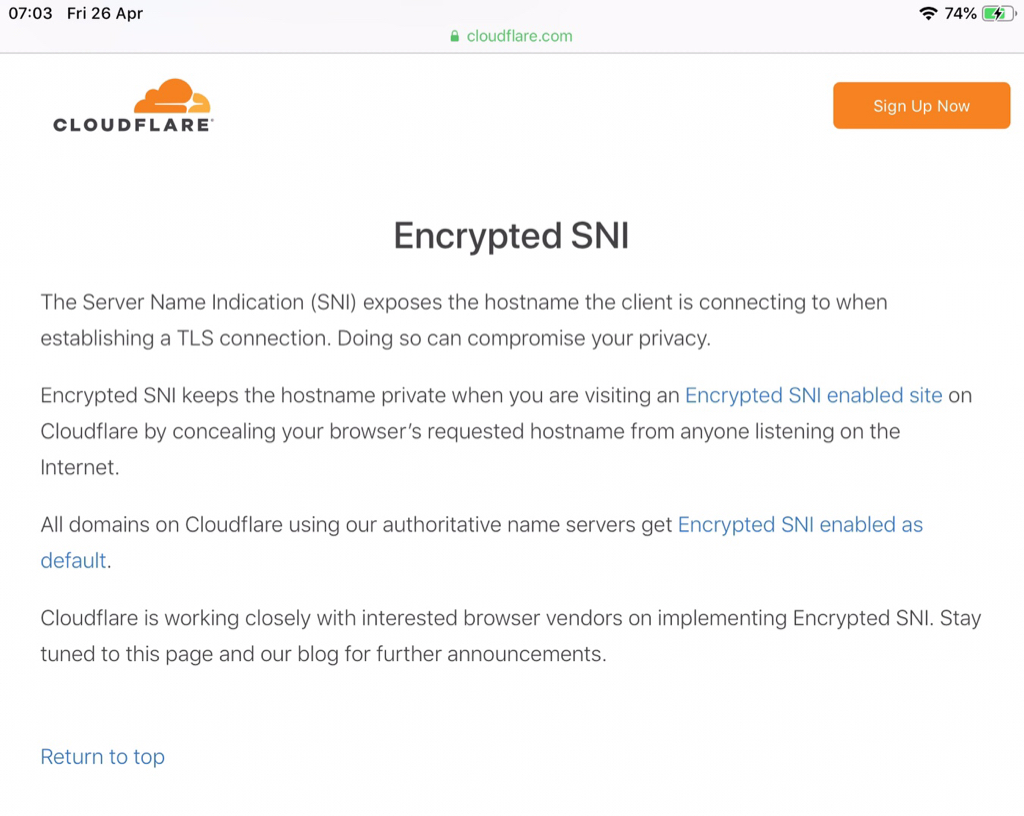
Why do some people get positive results on the Cloudflare DNS test page, while others (like me) don't?
(Do we know what causes the difference?)
Why do some people get positive results on the Cloudflare DNS test page, while others (like me) don't?
(Do we know what causes the difference?)
For me, if I enabled DNSSEC and DNS-over-TLS then it breaks that page. When I disable DNSSEC, then it works.
Same settings here, but I also have DNSFilter under LAN set to ‘Router’, leaving the DNS entries blank. Everything working fine as well.Connect to DNS Server automatically set to Yes
Forward local domain queries to upstream DNS set to No
Enable DNS rebind protection set to No
Enable DNSSEC support set to No
DNS Privacy Protocol set to DNS over TLS Enabled
DNS over TLS Profile set Strict
Preset servers chosen are 1.1.1.1 Cloudflare-dns.com
1.0.0.1 Cloudflare-dns.com
I’ve seen posts mentioning Enable DNS-based Filtering on the LAN page, mine is switched off.
We have been telling folks for some time now that DNSSEC breaks the cf help test. In time it will get fixed or not. Stubby DoT and DNSSEC do work. For now you just trust that it does...Why do some people get positive results on the Cloudflare DNS test page, while others (like me) don't?
(Do we know what causes the difference?)
That would indeed explain the failure I see.For me, if I enabled DNSSEC and DNS-over-TLS then it breaks that page. When I disable DNSSEC, then it works.
Add the second quad9 secure server at 149.112.112.112
Sent from my SM-T380 using Tapatalk

Welcome To SNBForums
SNBForums is a community for anyone who wants to learn about or discuss the latest in wireless routers, network storage and the ins and outs of building and maintaining a small network.
If you'd like to post a question, simply register and have at it!
While you're at it, please check out SmallNetBuilder for product reviews and our famous Router Charts, Ranker and plenty more!
