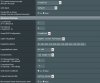
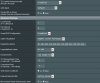
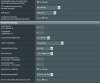
With same settings i connect on 380,64_2 with BF-CBC, above 380,65 and also on 380,66 alpha 3 with openssl 2.4.1 only aes 256 possible.... (same on cipher negotiation disbabled) ....
Server side is unchanged ...
380,65 ... log
pr 5 18:38:08 openvpn[1626]: VERIFY OK: depth=1, C=NV, ST=NV, L=nVPN, O=nVpn, CN=nVpn CA, emailAddress=support@nvpn.net
Apr 5 18:38:08 openvpn[1626]: VERIFY OK: depth=0, C=NV, ST=NV, L=nVPN, O=nVpn, CN=server, emailAddress=support@nvpn.net
Apr 5 18:38:08 openvpn[1626]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 1024 bit RSA
Apr 5 18:38:08 openvpn[1626]: [server] Peer Connection Initiated with [AF_INET]xxx:1194
Apr 5 18:38:09 openvpn[1626]: SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Apr 5 18:38:14 openvpn[1626]: SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Apr 5 18:38:14 openvpn[1626]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route xxx,topology net30,ping 10,ping-restart 120,ifconfig xxx,peer-id 1,cipher AES-256-GCM'
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: timers and/or timeouts modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: --ifconfig/up options modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: route options modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: peer-id set
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: adjusting link_mtu to 1629
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: data channel crypto options modified
Apr 5 18:38:14 openvpn[1626]: Data Channel Encrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Apr 5 18:38:14 openvpn[1626]: Data Channel Decrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
380,64_2
Apr 5 18:47:36 openvpn[793]: Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
Apr 5 18:47:36 openvpn[793]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 5 18:47:36 openvpn[793]: Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Apr 5 18:47:36 openvpn[793]: Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
Apr 5 18:47:36 openvpn[793]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 5 18:47:36 openvpn[793]: Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Apr 5 18:47:36 openvpn[793]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 1024 bit RSA
Apr 5 18:47:36 openvpn[793]: [server] Peer Connection Initiated with [AF_INET]xxx:1194
Apr 5 18:47:37 dnsmasq-dhcp[436]: DHCPREQUEST(br0) 192.168.1.152 9c:b7:0d:69:a3:dc
Apr 5 18:47:37 dnsmasq-dhcp[436]: DHCPACK(br0) 192.168.1.152 9c:b7:0d:69:a3:dc HP
Apr 5 18:47:38 openvpn[793]: SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Apr 5 18:47:38 openvpn[793]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route xx,topology net30,ping 10,ping-restart 120,ifconfig xx,peer-id 2'
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: timers and/or timeouts modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: --ifconfig/up options modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: route options modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: peer-id set
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: adjusting link_mtu to 1549
Server side is unchanged ...
380,65 ... log
pr 5 18:38:08 openvpn[1626]: VERIFY OK: depth=1, C=NV, ST=NV, L=nVPN, O=nVpn, CN=nVpn CA, emailAddress=support@nvpn.net
Apr 5 18:38:08 openvpn[1626]: VERIFY OK: depth=0, C=NV, ST=NV, L=nVPN, O=nVpn, CN=server, emailAddress=support@nvpn.net
Apr 5 18:38:08 openvpn[1626]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 1024 bit RSA
Apr 5 18:38:08 openvpn[1626]: [server] Peer Connection Initiated with [AF_INET]xxx:1194
Apr 5 18:38:09 openvpn[1626]: SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Apr 5 18:38:14 openvpn[1626]: SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Apr 5 18:38:14 openvpn[1626]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route xxx,topology net30,ping 10,ping-restart 120,ifconfig xxx,peer-id 1,cipher AES-256-GCM'
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: timers and/or timeouts modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: --ifconfig/up options modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: route options modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: peer-id set
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: adjusting link_mtu to 1629
Apr 5 18:38:14 openvpn[1626]: OPTIONS IMPORT: data channel crypto options modified
Apr 5 18:38:14 openvpn[1626]: Data Channel Encrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Apr 5 18:38:14 openvpn[1626]: Data Channel Decrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
380,64_2
Apr 5 18:47:36 openvpn[793]: Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
Apr 5 18:47:36 openvpn[793]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 5 18:47:36 openvpn[793]: Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Apr 5 18:47:36 openvpn[793]: Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
Apr 5 18:47:36 openvpn[793]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 5 18:47:36 openvpn[793]: Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Apr 5 18:47:36 openvpn[793]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 1024 bit RSA
Apr 5 18:47:36 openvpn[793]: [server] Peer Connection Initiated with [AF_INET]xxx:1194
Apr 5 18:47:37 dnsmasq-dhcp[436]: DHCPREQUEST(br0) 192.168.1.152 9c:b7:0d:69:a3:dc
Apr 5 18:47:37 dnsmasq-dhcp[436]: DHCPACK(br0) 192.168.1.152 9c:b7:0d:69:a3:dc HP
Apr 5 18:47:38 openvpn[793]: SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Apr 5 18:47:38 openvpn[793]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route xx,topology net30,ping 10,ping-restart 120,ifconfig xx,peer-id 2'
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: timers and/or timeouts modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: --ifconfig/up options modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: route options modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: peer-id set
Apr 5 18:47:38 openvpn[793]: OPTIONS IMPORT: adjusting link_mtu to 1549