Not 100% sure but I think what you are after is
site to site, if so, see the post in that link and
also Colin's post which refers to Tailscale's site to site instructions.
Essentially what Viktor said:
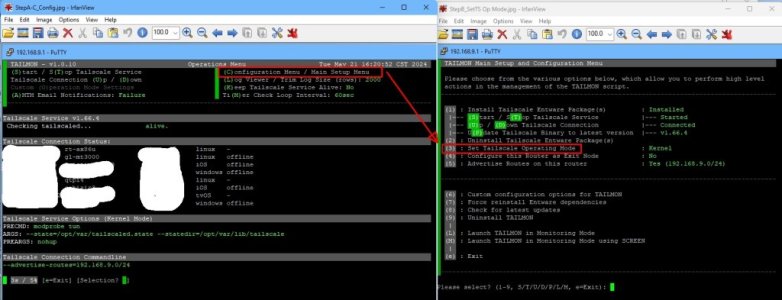
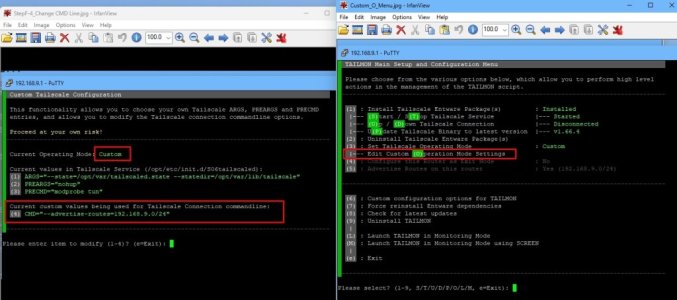
i.e. append “
--accept-routes” after “
--advertise-routes” on the command line.
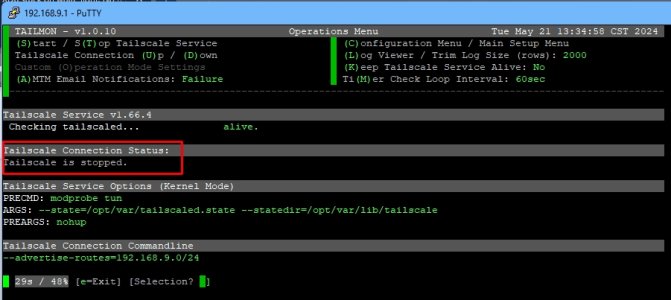
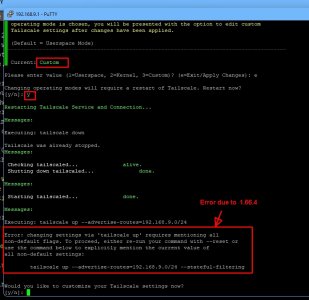
Note with the latest 1.66.4 I believe you no longer need to actively disable stateful filtering per Colin's post; it is now disabled by default.
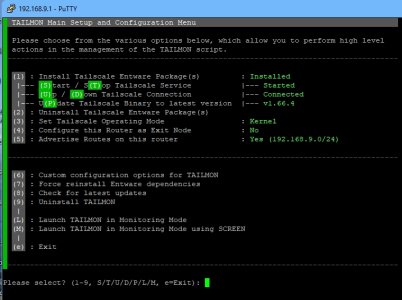
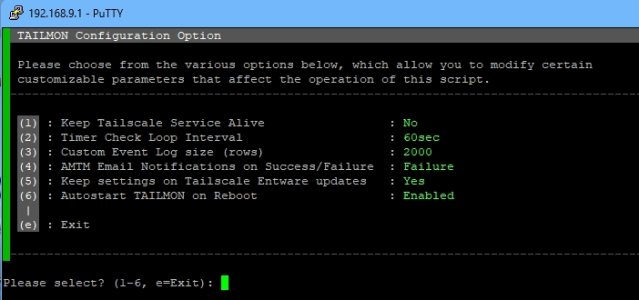
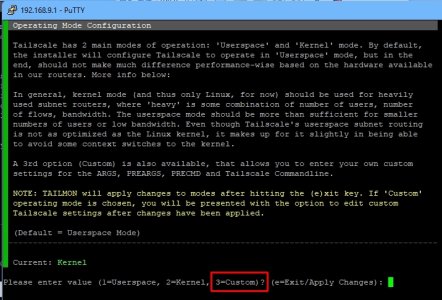
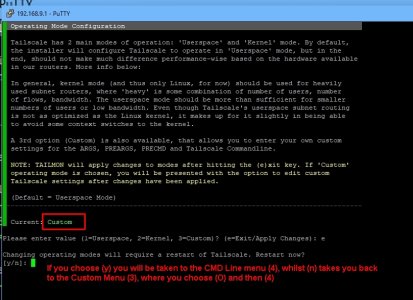
To get into the Custom Commandline Options, go to (C), 3, 3 for Custom (of Userspace, Kernel, Custom), exit (e), y, then you should get a prompt to customize the Tailscale settings, you then select (4) and amend teh abovce lines.
You wil also see an extra menu under the Custom Menu, (O), where you can amend to again if needed.
Let us know how you get on