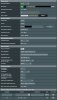
Starting_OpenVPN_%s_%d...: server
ovpn-server1[189]: OpenVPN 2.4.9 arm-buildroot-linux-gnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on 21 2020
ovpn-server1[189]: library versions: OpenSSL 1.1.1g 21 Apr 2020, LZO 2.08
ovpn-server1[1880]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
ovpn-server1[1880]: PLUGIN_INIT: POST /usr/lib/openvpn-plugin-auth-pam.so '[/usr/lib/openvpn-plugin-auth-pam.so] [openvpn]' intercepted=PLUGIN_AUTH_USER_PASS_VERIFY
ovpn-server1[1880]: Diffie-Hellman initialized with 2048 bit key
ovpn-server1[1880]: Outgoing Control Channel Encryption: Cipher 'AES--CTR' initialized with bit key
ovpn-server1[1880]: Outgoing Control Channel Encryption: Using bit message hash 'SHA' for HMAC authentication
ovpn-server1[1880]: Incoming Control Channel Encryption: Cipher 'AES--CTR' initialized with bit key
ovpn-server1[1880]: Incoming Control Channel Encryption: Using bit message hash 'SHA' for HMAC authentication
ovpn-server1[1880]: TUN/TAP device tun21 opened
ovpn-server1[1880]: TUN/TAP TX queue length set to 1000
ovpn-server1[1880]: /sbin/ifconfig tun21 10.8.0.1 netmask 5.5.5.0 mtu 1500 broadcast 10.8.0.5
lldpd[1355]: removal request for address of 10.8.0.1%23, but no knowledge of it
lldpd[1355]: removal request for address of 10.8.0.1%23, but no knowledge of it
ovpn-server1[1880]: updown.sh tun21 1500 124 10.8.0.1 5.5.5.0 init
ovpn-server1[1880]: Could not determine IPv4/IPv protocol. Using AF_INET
ovpn-server1[1880]: Socket Buffers: R=[8380->8380] S=[1384->1384]
ovpn-server1[1880]: Listening for incoming TCP connection on [AF_INET][undef]:43443
ovpn-server1[1880]: TCPv4_SERVER link local (bound): [AF_INET][undef]:43443
ovpn-server1[1880]: TCPv4_SERVER link remote: [AF_UNSPEC]
ovpn-server1[1880]: MULTI: multi_init called, r= v=
ovpn-server1[1880]: IFCONFIG POOL: base=10.8.0.2 size=2, ipv=0
ovpn-server1[1880]: MULTI: TCP INIT maxclients=1024 maxevents=1028
ovpn-server1[1880]: Initialization Sequence Completed
openvpn: OpenVPN server 1 launch completed.
openvpn: Setting up OpenVPN server 2...
Starting_OpenVPN_%s_%d...: server
ovpn-server2[1943]: OpenVPN 2.4.9 arm-buildroot-linux-gnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on 21 2020
ovpn-server2[1943]: library versions: OpenSSL 1.1.1g 21 Apr 2020, LZO 2.08
ovpn-server2[194]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
ovpn-server2[194]: PLUGIN_INIT: POST /usr/lib/openvpn-plugin-auth-pam.so '[/usr/lib/openvpn-plugin-auth-pam.so] [openvpn]' intercepted=PLUGIN_AUTH_USER_PASS_VERIFY
ovpn-server2[194]: Diffie-Hellman initialized with 2048 bit key
ovpn-server2[194]: Outgoing Control Channel Encryption: Cipher 'AES--CTR' initialized with bit key
ovpn-server2[194]: Outgoing Control Channel Encryption: Using bit message hash 'SHA' for HMAC authentication
ovpn-server2[194]: Incoming Control Channel Encryption: Cipher 'AES--CTR' initialized with bit key
ovpn-server2[194]: Incoming Control Channel Encryption: Using bit message hash 'SHA' for HMAC authentication
ovpn-server2[194]: TUN/TAP device tun22 opened
ovpn-server2[194]: TUN/TAP TX queue length set to 1000
ovpn-server2[194]: /sbin/ifconfig tun22 10.1.0.1 netmask 5.5.5.0 mtu 1500 broadcast 10.1.0.5
lldpd[1355]: removal request for address of 10.1.0.1%24, but no knowledge of it
lldpd[1355]: removal request for address of 10.1.0.1%24, but no knowledge of it
ovpn-server2[194]: updown.sh tun22 1500 124 10.1.0.1 5.5.5.0 init
ovpn-server2[194]: Could not determine IPv4/IPv protocol. Using AF_INET
ovpn-server2[194]: Socket Buffers: R=[8380->8380] S=[1384->1384]
ovpn-server2[194]: Listening for incoming TCP connection on [AF_INET][undef]:43444
ovpn-server2[194]: TCPv4_SERVER link local (bound): [AF_INET][undef]:43444
ovpn-server2[194]: TCPv4_SERVER link remote: [AF_UNSPEC]
ovpn-server2[194]: MULTI: multi_init called, r= v=
ovpn-server2[194]: IFCONFIG POOL: base=10.1.0.2 size=2, ipv=0
ovpn-server2[194]: MULTI: TCP INIT maxclients=1024 maxevents=1028
ovpn-server2[194]: Initialization Sequence Completed
openvpn: OpenVPN server 2 launch completed.
ovpn-server1[1880]: TCP connection established with [AF_INET]xx.xx.xx.xx:392
ovpn-server1[1880]: xx.xx.xx.xx:392 TLS: Initial packet from [AF_INET]xx.xx.xx.xx:392, sid=aab5d5d 38513b09
ovpn-server1[1880]: xx.xx.xx.xx:392 VERIFY OK: depth=1, C=TW, ST=TW, L=Taipei, O=ASUS, CN=RT-AC8U, emailAddress=
me@myhost.mydomain
ovpn-server1[1880]: xx.xx.xx.xx:392 VERIFY OK: depth=0, C=TW, ST=TW, L=Taipei, O=ASUS, CN=client, emailAddress=
me@myhost.mydomain
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_VER=3.git:released:3e5f9a:Release
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_PLAT=android
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_NCP=2
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_TCPNL=1
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_PROTO=2
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_LZO_STUB=1
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_COMP_STUB=1
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_COMP_STUBv2=1
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_GUI_VER=net.openvpn.connect.android_3.2.2-502
ovpn-server1[1880]: xx.xx.xx.xx:392 peer info: IV_SSO=openurl
ovpn-server1[1880]: xx.xx.xx.xx:392 PLUGIN_CALL: POST /usr/lib/openvpn-plugin-auth-pam.so/PLUGIN_AUTH_USER_PASS_VERIFY status=0
ovpn-server1[1880]: xx.xx.xx.xx:392 TLS: Username/Password authentication succeeded for username 'test23'
ovpn-server1[1880]: xx.xx.xx.xx:392 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES__GCM_SHA384, 2048 bit RSA
ovpn-server1[1880]: xx.xx.xx.xx:392 [client] Peer Connection Initiated with [AF_INET]xx.xx.xx.xx:392
ovpn-server1[1880]: client/xx.xx.xx.xx:392 MULTI_sva: pool returned IPv4=10.8.0.2, IPv=(Not enabled)
ovpn-server1[1880]: client/xx.xx.xx.xx:392 MULTI: Learn: 10.8.0.2 -> client/xx.xx.xx.xx:392
ovpn-server1[1880]: client/xx.xx.xx.xx:392 MULTI: primary virtual IP for client/xx.xx.xx.xx:392: 10.8.0.2
ovpn-server1[1880]: client/xx.xx.xx.xx:392 PUSH: Received control message: 'PUSH_REQUEST'
ovpn-server1[1880]: client/xx.xx.xx.xx:392 SENT CONTROL [client]: 'PUSH_REPLY,route 10..0.0 5.5.5.0 vpn_gateway 500,dhcp-option DOMAIN MyHome,dhcp-option DNS 10..0.1,redirect-gateway def1,route-gateway 10.8.0.1,topology subnet,ping 15,ping-restart 0,ifconfig 10.8.0.2 5.5.5.0,peer-id 0,cipher AES--GCM' (status=1)
ovpn-server1[1880]: client/xx.xx.xx.xx:392 Data Channel: using negotiated cipher 'AES--GCM'
ovpn-server1[1880]: client/xx.xx.xx.xx:392 Outgoing Data Channel: Cipher 'AES--GCM' initialized with bit key
ovpn-server1[1880]: client/xx.xx.xx.xx:392 Incoming Data Channel: Cipher 'AES--GCM' initialized with bit key
ovpn-server1[1880]: client/xx.xx.xx.xx:392 Connection reset, restarting [-1]
ovpn-server1[1880]: client/xx.xx.xx.xx:392 SIGUSR1[soft,connection-reset] received, client-instance restarting
ovpn-server2[194]: TCP connection established with [AF_INET]xx.xx.xx.xx:4013