CKret
Occasional Visitor
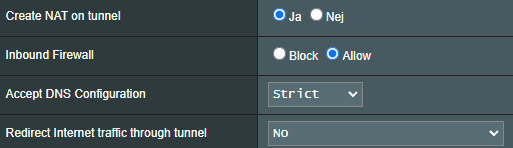
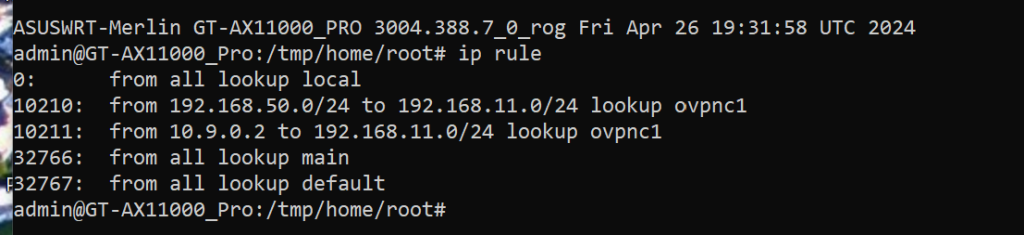
Based on the original rules, you have Redirection set to "All". In that case, VPNDirector will require you to create the two rules I mentionned in my post, otherwise nothing will be routed through the VPN.
EDIT: Tho generally in a site2site tunnel, you don't want to redirect everything - only the remote subnet. Unless you truly want the Internet connection to also go through the tunnel.
No I have No redirection set with the original rules. Redirection is only on the specific subnets of all sites.
Internet is never redirected through the tunnels. (If that is what you are suggesting).