You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
VPNMON VPNMON-R3 v1.3.8 -Nov 28, 2024- Monitor WAN/Dual-WAN/OpenVPN Health & Reset Multiple OpenVPN Connections (Now available in AMTM!)
- Thread starter Viktor Jaep
- Start date
Jack-Sparr0w
Regular Contributor
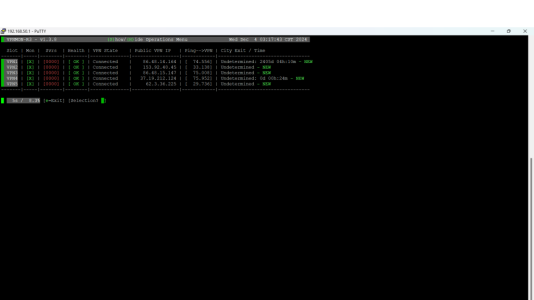
First time looking at this, Is this right? View attachment 62771
Is there any other config to be done with a basic NordVPN setup no unbound and using skynet Victor list
Attachments
Last edited:
Viktor Jaep
Part of the Furniture
1. It's kind of concerning that if this is very first time you've run this, that it somehow knows your VPN 1 slot has been going 2500 days. That's really weird. If you press the "1" key, it should reset that connection, and reset the time with it as well.First time looking at this, Is this right? does the VPN custom config file need to be changed?
2. Also, it doesn't seem to be getting any city exit information. Can you make sure you're not blocking "https://ipv4.icanhazip.com" ?
3. For each of your VPN slots, you can just add all the Nord VPN IP's to a server list for each particular slot if you want to randomize where it connects to next... or you can just keep it to 1 IP that it will just keep connecting to. I created some documentation here on how to automate this more: https://www.snbforums.com/threads/v...list-generation-tutorials-and-examples.88022/
For instance, my VPN1 slot randomizes against 2382 US-based Nord Servers... my VPN 5 slot randomizes against 86 AirVPN US-based servers. Each night it refreshes these lists to ensure they're up-to-date, and whitelisted in Skynet.
Let me know what specific issues you may be facing?
Last edited:
machinist
Occasional Visitor
Hello @Viktor Jaep . Thanks for all the work you're continually doing on your scripts here, what an asset you are.
Question: I tested R2 on this awhile back and now want to move over to R3 for my aging AC86U. I have an old RPi 3B laying around. Perhaps a dumb question but would I be served well with running the R3 version from the Raspberry Pi or would running it directly on the router suffice?
Question: I tested R2 on this awhile back and now want to move over to R3 for my aging AC86U. I have an old RPi 3B laying around. Perhaps a dumb question but would I be served well with running the R3 version from the Raspberry Pi or would running it directly on the router suffice?
Viktor Jaep
Part of the Furniture
You're very welcome! I don't think it would do much use on your RPi because it has to make direct calls to your router's NVRAM for it to do much of its magic. Keep it on the router where your VPN connection(s) are configured.Hello @Viktor Jaep . Thanks for all the work you're continually doing on your scripts here, what an asset you are.
Question: I tested R2 on this awhile back and now want to move over to R3 for my aging AC86U. I have an old RPi 3B laying around. Perhaps a dumb question but would I be served well with running the R3 version from the Raspberry Pi or would running it directly on the router suffice?
machinist
Occasional Visitor
@Viktor Jaep
Series of question to test my understanding - apologies in advance.
What I've done:
- Setup R3 on SCREEN utility and configured.
- Initial VPN setup from inside of VPN Director is basically to configure (4) slots with a single server IP VPN conf file each. Figure it would be an appropriate fallback.
- Have configured the local device I want VPN tunnel on (192.168.1.100) as (4) rules -- each with the corresponding VPN slot, i.e. OPVN1 => Device IP, OVPN2 => Device IP, OVPN3 => Device IP, OVPN4 => Device IP.
Questions:
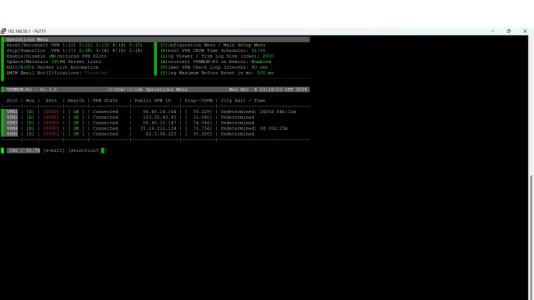
Is this right? All four connections are now live (Connected). I figure that's part of the point, but now I'm not sure. How is the actual endpoint determined out of the four live connections?
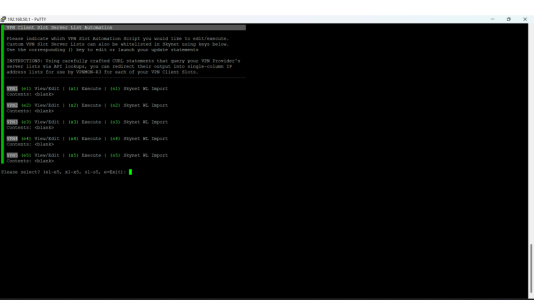
- Under "Edit/R(U)n Server List Automation" I've inserted the AirVPN curl commands for each of the slots, e.g.:
But for each of the slots in the Ops Menu I see [0000] under Svrs. What am I doing wrong -- do I need to also populate "Update/Maintain (V)PN Server Lists"? Was under the impression it would auto populate here using the curl scripts?
- When it reports "UNKWN" and "ping error", what does that mean exactly other than the obvious that there's an error?
- Lastly, when exiting the Ops Menu and to keep the script running, I am to hit CTRL + A + D and NOT [e=Exit], right?
That was a lot, thanks Viktor
Series of question to test my understanding - apologies in advance.
What I've done:
- Setup R3 on SCREEN utility and configured.
- Initial VPN setup from inside of VPN Director is basically to configure (4) slots with a single server IP VPN conf file each. Figure it would be an appropriate fallback.
- Have configured the local device I want VPN tunnel on (192.168.1.100) as (4) rules -- each with the corresponding VPN slot, i.e. OPVN1 => Device IP, OVPN2 => Device IP, OVPN3 => Device IP, OVPN4 => Device IP.
Questions:
Is this right? All four connections are now live (Connected). I figure that's part of the point, but now I'm not sure. How is the actual endpoint determined out of the four live connections?
- Under "Edit/R(U)n Server List Automation" I've inserted the AirVPN curl commands for each of the slots, e.g.:
Code:
curl --silent --retry 3 --connect-timeout 3 --max-time 6 --retry-delay 1 --retry-all-errors https://airvpn.org/api/status/ | jq --raw-output '.servers[] | select(.country_name=="Netherlands") | .ip_v4_in3, .ip_v4_in4'But for each of the slots in the Ops Menu I see [0000] under Svrs. What am I doing wrong -- do I need to also populate "Update/Maintain (V)PN Server Lists"? Was under the impression it would auto populate here using the curl scripts?
- When it reports "UNKWN" and "ping error", what does that mean exactly other than the obvious that there's an error?
- Lastly, when exiting the Ops Menu and to keep the script running, I am to hit CTRL + A + D and NOT [e=Exit], right?
That was a lot, thanks Viktor
Viktor Jaep
Part of the Furniture
Let's hope I can answer these!Series of question to test my understanding - apologies in advance.
This sounds right! If you want, you can provide some screenshots of how you configured your VPN director, and what VPNMON-R3 is looking like right now? But from the sound of it, you have 4 different devices all pointing to different VPN end points, correct? VPN Director is in charge of routing that traffic across the appropriate VPN slot, which is how it determines the actual endpoint for each device.What I've done:
- Setup R3 on SCREEN utility and configured.
- Initial VPN setup from inside of VPN Director is basically to configure (4) slots with a single server IP VPN conf file each. Figure it would be an appropriate fallback.
- Have configured the local device I want VPN tunnel on (192.168.1.100) as (4) rules -- each with the corresponding VPN slot, i.e. OPVN1 => Device IP, OVPN2 => Device IP, OVPN3 => Device IP, OVPN4 => Device IP.
Questions:
Is this right? All four connections are now live (Connected). I figure that's part of the point, but now I'm not sure. How is the actual endpoint determined out of the four live connections?
Congrats on getting that CURL statement correct. I tested it, and it brings back results. In order for the "SVRS" item to show more that "[0000]", just hit the execute command on that same screen. So for instance, on slot 5, you would hit "x5". It will show you the results of the query and tell you how many servers are now assigned to that slot.- Under "Edit/R(U)n Server List Automation" I've inserted the AirVPN curl commands for each of the slots, e.g.:
Code:curl --silent --retry 3 --connect-timeout 3 --max-time 6 --retry-delay 1 --retry-all-errors https://airvpn.org/api/status/ | jq --raw-output '.servers[] | select(.country_name=="Netherlands") | .ip_v4_in3, .ip_v4_in4'
But for each of the slots in the Ops Menu I see [0000] under Svrs. What am I doing wrong -- do I need to also populate "Update/Maintain (V)PN Server Lists"? Was under the impression it would auto populate here using the curl scripts?
It will optionally refresh the server lists each night when you have item 5 enabled under the configuration menu, if you are resetting your VPN nightly (using the R key) from the main operations menu:
When you see these, it just means that your router is having trouble getting a ping back from the VPN end point. Usually they are few and far between... if it keeps happening, then it will figure that this endpoint is no good, and will disconnect and reconnect to another server in your server list.- When it reports "UNKWN" and "ping error", what does that mean exactly other than the obvious that there's an error?
Correct... if you're using Screen. I start VPNMON-R3 using the command "vpnmon-r3 -screen -now", which will run an instance under screen. You can use this command to see the UI, and to exit, CTRL-A + D. The "e" command will just kill the script.- Lastly, when exiting the Ops Menu and to keep the script running, I am to hit CTRL + A + D and NOT [e=Exit], right?
Glad to help!That was a lot, thanks Viktor
machinist
Occasional Visitor
This sounds right! If you want, you can provide some screenshots of how you configured your VPN director, and what VPNMON-R3 is looking like right now? But from the sound of it, you have 4 different devices all pointing to different VPN end points, correct? VPN Director is in charge of routing that traffic across the appropriate VPN slot, which is how it determines the actual endpoint for each device.
At the moment I have 1 device that has to be routed through the VPN. Number of devices will increase, but for now it's only the one. All other traffic on the network goes out through WAN.
So, I've setup a rule for each OVPN interface to target the device on ...200 -- ignore slot 5, it's not active as I plan on using it for Unbound and DNS like I've seen on another post of yours
Thoughts?
Follow-up: When the R3 checks for ping health and it finds one of the connections to be above the custom value of, say, 200ms - but it _is_ still connected to it. It then shuts it down, finds another, and reconnects. What happens to the connection in the interim? Does the built in killswitch take over, or does the connection resume over WAN? Let me know if I'm asking the wrong question, please.
Damnit, missed that. It works!In order for the "SVRS" item to show more that "[0000]", just hit the execute command on that same screen. So for instance, on slot 5, you would hit "x5". It will show you the results of the query and tell you how many servers are now assigned to that slot.
Got it.When you see these, it just means that your router is having trouble getting a ping back from the VPN end point. Usually they are few and far between... if it keeps happening, then it will figure that this endpoint is no good, and will disconnect and reconnect to another server in your server list.
About that - is there any reason to enable this when it already checks/pings the connections in your specified interval? Or is it more a case of either/or, so as to not set an interval and then have it reset every night?It will optionally refresh the server lists each night when you have item 5 enabled under the configuration menu, if you are resetting your VPN nightly (using the R key) from the main operations menu:
vpnmon-r3 -screen -nowCorrect... if you're using Screen. I start VPNMON-R3 using the command "vpnmon-r3 -screen -now", which will run an instance under screen. You can use this command to see the UI, and to exit, CTRL-A + D. The "e" command will just kill the script.
Excellent, just what I needed. My next question was how to easily navigate in and out of the Ops Menu.
Thanks for the patience.
Last edited:
Viktor Jaep
Part of the Furniture
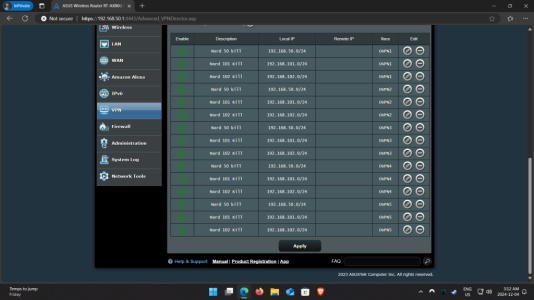
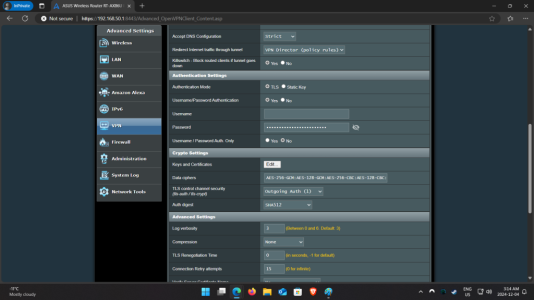
Personally, I think what you're doing is a bit overkill. You really just need 1 VPN slot set up for this particular scenario. For instance, on my end, I have all devices in our entire house going through VPN slot 1, and a select few are excluded which hit the WAN directly.View attachment 62972
At the moment I have 1 device that has to be routed through the VPN. Number of devices will increase, but for now it's only the one. All other traffic on the network goes out through WAN.
So, I've setup a rule for each OVPN interface to target the device on ...200 -- ignore slot 5, it's not active as I plan on using it for Unbound and DNS like I've seen on another post of yours
Thoughts?
If you aren't using the built-in killswitch (which I don't use either), then when the VPN connection is killed, all traffic would temporarily get routed over the WAN until the VPN tunnel comes back up. Depending on the process, it might take a good 30sec-1min for things to get killed and reconnect. If your killswitch is enabled, then as soon as the VPN goes down, all traffic no longer is allowed to exit via the WAN until the VPN tunnel comes back up.Follow-up: When the R3 checks for ping health and it finds one of the connections to be above the custom value of, say, 200ms - but it _is_ still connected to it. It then shuts it down, finds another, and reconnects. What happens to the connection in the interim? Does the built in killswitch take over, or does the connection resume over WAN? Let me know if I'm asking the wrong question, please.
The reason for this is to refresh your connection with a different server, so that your connection rotates on a regular basis. In my case, I connect to one of 2000+ servers across the US. The other thing this does is get a new refreshed list of servers from your VPN provider. They might delete some servers, add new ones, etc. Your old list wouldn't know about these, and may try to connect to a dead server. You can then optionally whilelist all these servers in Skynet as well (using option #7 in the config).About that - is there any reason to enable this when it already checks/pings the connections in your specified interval? Or is it more a case of either/or, so as to not set an interval and then have it reset every night?
Thanks for the patience.
machinist
Occasional Visitor
If I may:The reason for this is to refresh your connection with a different server, so that your connection rotates on a regular basis. In my case, I connect to one of 2000+ servers across the US. The other thing this does is get a new refreshed list of servers from your VPN provider. They might delete some servers, add new ones, etc. Your old list wouldn't know about these, and may try to connect to a dead server. You can then optionally whilelist all these servers in Skynet as well (using option #7 in the config).
If I set it to reset once a day (under 'R'), is it both a reset of the server list or is it also a connection reset (switch to a different VPN server IP from the new and updated list)?
EDIT: That has to be the case, if I'm understanding you right.
When the nightly reset happens, I suppose it will work the same way as when auto switching VPN from high ping, as in it will allow traffic out through WAN in the interim for the 30-60 seconds?
Is there a way to completely disallow this? I'd want the connection to completely sever and not allow anything out that is not through the VPN tunnel. I am using the built in kill-switch in Merlin. Will that suffice for this?
Last edited:
Viktor Jaep
Part of the Furniture
Just this once I guess...If I may:
The Server List will be refreshed only if you have this option (below) set to "enabled". If you don't, it will just reset your connection, and choose a random server from your list.If I set it to reset once a day (under 'R'), is it both a reset of the server list or is it also a connection reset (switch to a different VPN server IP from the new and updated list)?
machinist
Occasional Visitor
Where do I donate?Just this once I guess...
You're too quick. I updated the reply above, if you didn't catch it
Viktor Jaep
Part of the Furniture
Correct. It refreshes the list, then chooses a random server to connect to.If I may:
If I set it to reset once a day (under 'R'), is it both a reset of the server list or is it also a connection reset (switch to a different VPN server IP from the new and updated list)?
EDIT: That has to be the case, if I'm understanding you right.
Same principle, but it does not refresh the list in this case. It just chooses a different server from the existing list.When the nightly reset happens, I suppose it will work the same way as when auto switching VPN from high ping, as in it will allow traffic out through WAN in the interim for the 30-60 seconds?
Using the built-in Killswitch should work for you in this case. I havent tried the new Killswitch implementation. Best way to tell is to test it out. Try resetting the connection, and see if you can browse the Internet while the VPN connection is down?Is there a way to completely disallow this? I'd want the connection to completely sever and not allow anything out that is not through the VPN tunnel. I am using the built in kill-switch in Merlin. Will that suffice for this?
Similar threads
- Replies
- 20
- Views
- 2K
- Replies
- 17
- Views
- 2K
- Replies
- 22
- Views
- 822
Similar threads
Similar threads
-
(Not specifically) VPNMON-R3 1.11 failure domino effect
- Started by Ripshod
- Replies: 20
-
amtm amtm 5.1 - the Asuswrt-Merlin Terminal Menu, December 09, 2024
- Started by thelonelycoder
- Replies: 69
-
Entware Entware repository update: August 8, 2024
- Started by thelonelycoder
- Replies: 21
-
Diversion Diversion 5.4.1 - the Router Ad-Blocker, December 15, 2024
- Started by thelonelycoder
- Replies: 91
-
TAILMON TAILMON v1.0.20 -July 27, 2024- WireGuard-based Tailscale Installer, Configurator and Monitor (THREAD #1 CLOSED)
- Started by Viktor Jaep
- Replies: 556
-
uiDivStats uiDivstats 4.0.5 - WebUI Stats for Diversion, December 15, 2024
- Started by thelonelycoder
- Replies: 70
-
scMerlin scMerlin 2.5.8 - Service and script control menu for Asuswrt-Merlin, October 20, 2024
- Started by thelonelycoder
- Replies: 85
Latest threads
-
-
Issue with selective VPN Routing on ASUS GS-AX3000 (WireGuard & VPN Fusion)
- Started by BerkayDrsn
- Replies: 1
-
-
-
RT-AX86U Pro trouble 2.4 devices
- Started by Heronimos
- Replies: 4
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Staff online
-
thigginsMr. Easy