Asuswrt-Merlin 3006.102.1 Beta is now available for the RT-BE96U and the GT-BE98_PRO. This is the first release based on the new 3006 code, and also the first release to include WIfi 7 devices.
Do not ask about support for other models. 3006.102.1 will only support these two models (plus the GT-BE98 by Gnuton), and we will re-evaluate things after that realease is finalized on any other potential device to support. These must be picked in collaboration with Asus as GPL code and device samples (in the case of new devices) are necessary for each individual model.
Changelog:
Things to test in particular:
For Addons developers:
There may be other changes that affect script authors, as I don't know what internal structures or variables they may be interfacing with.
Please keep discussions on testing of these two devices. Off-topic posts will be ignored, moved or deleted, based on my mood at the time.
Downloads are here.
Changelog is here.
Do not ask about support for other models. 3006.102.1 will only support these two models (plus the GT-BE98 by Gnuton), and we will re-evaluate things after that realease is finalized on any other potential device to support. These must be picked in collaboration with Asus as GPL code and device samples (in the case of new devices) are necessary for each individual model.
Changelog:
Code:
3006.102.1 (xx-xxx-2024)
This is the initial release of Asuswrt-Merlin based on
the 3006 codebase. Only a few specific models are
currently available, more will be added over time as
Asus progressively migrates devices to the new codebase.
3006 introduces a number of major features, these will not
be listed - please review Asus' own documentation on the
new features added in 3006 (AKA Asuswrt 5.0). The two most
notable ones are VLAN and Guest Network Pro (also called
Self-Defined Networks, or SDN), both of which are supported
in Asuswrt-Merlin.
This initial 3006.102.xx release also includes a number of
potentially breaking changes over 3004. The most relevant
ones will be listed below.
Note that while Asus uses VPNFusion, Asuswrt-Merlin still
uses VPNDirector. The integration with Guest Network Pro
had to be re-implemented to work with Asuswrt-Merlin,
which required a few backend changes.
Due to the VPN backend differences, it's strongly recommended
to do a factory default reset after coming from the original
Asus firmware if you used any VPN-related functionality.
- NEW: Added support for GT-BE98_PRO.
- NEW: Added support for RT-BE96U.
- NOTE: Wifi 7 devices don't support NFS (issue with new
toolchain), QoS classification page (issue with
TrendMicro BWDPI) or Wifi Radar (not updated by
Broadcom).
- NEW: Added dnsmasq-INDEX.conf.add and stubby-INDEX.yml.add,
which are appended to SDN config files (INDEX = SDN
index number)
- NEW: Added dnsmasq-sdn.postconf and stubby-sdn.postconf.
They take two arguments:
- path to the config file for that SDN's instance
- the SDN index number (1 for the first SDN instance)
- NEW: Rewrote VPN killswitch implementation. The new method
uses an always present routing rule to prohibit access to
the main routing table, so it will be active even if the
user manually stops a client. Removing the prohibit rule
requires disabling the killswitch on the webui.
The rules are also created before WAN goes up, to reduce
the risks of leaks between WAN going up and VPN connecting.
- NEW: Added killswitch support for WireGuard clients.
- UPDATED: Merged with GPL 3.0.0.6.102_34369.
- UPDATED: Chart.js was upgraded from 2.x to 3.9, to share the
same version used by Asus. Any third party addon
that used it will need to upgrade their charts to
the new version.
- UPDATED: wget to 1.24.5.
- CHANGED: Switched to a different qrcode generation script, to
share the same script used by Asus.
- CHANGED: WireGuard and OpenVPN clients use different iproute2
table IDs, to be in line with Asus's own table IDs.
The names defined in rt_tables remain unchanged.
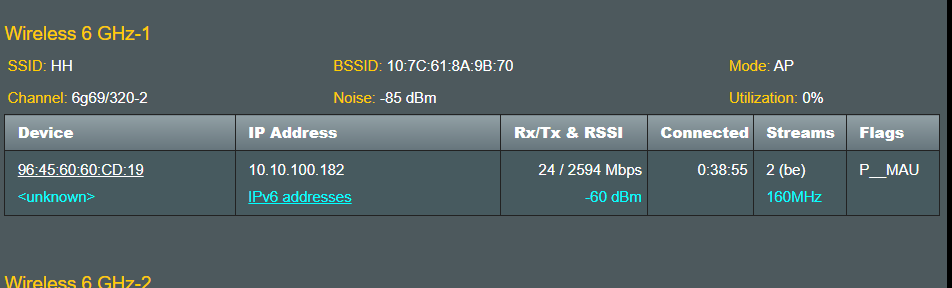
- CHANGED: Implemented support for Wifi 7 and SDN on the
Wireless Log page.
- CHANGED: Implemented DNSDirector webui for SDN.
- CHANGED: Removed stop/start and "Start with WAN" buttons from
OpenVPN clients. There is now just a single
"Enable" option, which will immediately start the
client when applying changes, and will also start it
automatically when WAN comes up. This is to reduce
confusion, better integrate into SDN, and match how
WireGuard clients already worked.
- CHANGED: ipset is now compiled into the kernel rather than as
modules (to match with Asus)
- CHANGED: Removed led_disable nvram, we now share the same AllLED
nvram as used by Asus for the LED button (and AiMesh sync)
- FIXED: JS error on Wifi 6e/7 models when toggling DDNS.
- REMOVED: Option dns_local_cache from Tools -> Tweak settings,
to avoid issues with SDN that run their own
dnsmasq instances.
- REMOVED: Wifi Radar was removed (unsupported by Wifi 7 devices,
and security issues cited by Asus in their own recent
releases).Things to test in particular:
- Guest Network Pro. Test with a VPN client, make sure traffic gets properly routed
- New killswitch implementation. Test various OpenVPN scenarios.
- Wireguard killswitch implementation. Test various scenarios.
- Test Wireless Log display with Guest Network Pro clients
- Test Wireless Log display with WIfi 7 clients (I only did limited testing by connecting another router as I don't have any Wifi 7 client)
- DNS Director tied to a Guest Network
For Addons developers:
- Chart.js was updated to 3.9. The 3004.388 branch will also be upgraded with 388.8, so get your addons updated if they use chart.js.
- The qrcode Javascript library was changed, as I switched to the same library Asus uses for Guet Network Pro. This change will only apply to 3006 firmwares.
- If your addon deals with VPN or routing, make sure they still work properly with the 3006 changes. iproute2 table IDs were changed for wgc and ovpn clients for instance (the ID changed, but the names remained the same)
- Each Guest Network can run its own dnsmasq instance. If your addon modified dnsmasq.conf, then you will need to adjust.
- Note that WIfi 7 routers are still based on kernel 4.19 (but a newer minor revision), the same Entware ARM 64-bit repo still works fine.
- ipset is now compiled built into the kernel rather than as a module, to match with Asus. If you use ipset, don't try to modprobe modules under 3006. I might apply that to 3004.388 as well, undecided yet.
- LED enable/disable was changed. Instead of our own led_disable nvram, we now reuse the AllLED nvram that Asus uses for the LED button. This will allow to sync it with AiMesh nodes. Anything that can manipulate LEDs will need to adjust. This will eventually be ported to 3004.388 as well.
There may be other changes that affect script authors, as I don't know what internal structures or variables they may be interfacing with.
Please keep discussions on testing of these two devices. Off-topic posts will be ignored, moved or deleted, based on my mood at the time.
Downloads are here.
Changelog is here.
Last edited: