You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Asuswrt-Merlin 378.53 is now available
- Thread starter RMerlin
- Start date
thegorilla
Occasional Visitor
I'd be looking around the first error, the missing ';' which is probably building a clientlist or something similar. Can you post the debugger output around that error?
Wow, you are GOOD! It appears to be an apostrophe in one of my DHCP manually assigned device names that is not currently connected.
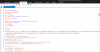
Is there a way to change this setting without using the GUI, so I can fix it?
Is there a way to prevent non-alphanumeric, dash, or underscore characters from being used in the manual assign DHCP client list?
Advanced_DHCP_Content.asp debugger, lines 46-86:
Code:
#ClientList_Block_PC a{
background-color:#EFEFEF;
color:#FFF;
font-size:12px;
font-family:Arial, Helvetica, sans-serif;
text-decoration:none;
}
#ClientList_Block_PC div:hover, #ClientList_Block a:hover{
background-color:#3366FF;
color:#FFFFFF;
cursor:default;
}
</style>
<script>
var dhcp_staticlist_array = '<D4:BE:D9:82:16:1D.168.99.100>A5271569ᝰ:25:AE:F7:BF:6F.168.99.169>ឈ:77:03:E2:41:0C.168.99.101>A5271569ᝰ:19:D1:29:B2:F0.168.99.23>STACKERᝰ:90:A9:B1:62:C4.168.99.110>MYBOOKLIVE3Tᝰ:1A:4D:5B:BB:BF.168.99.25>AMD47ɘC:89:10:AF:4F:2E.168.99.75>Samsung TV 1əC:99:4C:38:24:32.168.99.151>Orn's Note3 ';
if(pptpd_support){
var pptpd_clients = '192.168.99.190-199';
var pptpd_clients_subnet = pptpd_clients.split(".")[0]+"."
+pptpd_clients.split(".")[1]+"."
+pptpd_clients.split(".")[2]+".";
var pptpd_clients_start_ip = parseInt(pptpd_clients.split(".")[3].split("-")[0]);
var pptpd_clients_end_ip = parseInt(pptpd_clients.split("-")[1]);
}
var dhcp_enable = '1';
var pool_start = '192.168.99.200';
var pool_end = '192.168.99.254';
var pool_subnet = pool_start.split(".")[0]+"."+pool_start.split(".")[1]+"."+pool_start.split(".")[2]+".";
var pool_start_end = parseInt(pool_start.split(".")[3]);
var pool_end_end = parseInt(pool_end.split(".")[3]);
var static_enable = '1';
var dhcp_staticlists = '<D4:BE:D9:82:16:1D.168.99.100>A5271569ᝰ:25:AE:F7:BF:6F.168.99.169>ឈ:77:03:E2:41:0C.168.99.101>A5271569ᝰ:19:D1:29:B2:F0.168.99.23>STACKERᝰ:90:A9:B1:62:C4.168.99.110>MYBOOKLIVE3Tᝰ:1A:4D:5B:BB:BF.168.99.25>AMD47ɘC:89:10:AF:4F:2E.168.99.75>Samsung TV 1əC:99:4C:38:24:32.168.99.151>Orn's Note3 ';
var staticclist_row = dhcp_staticlists.split('<');
var lan_domain_curr = '';
var dhcp_gateway_curr = '192.168.99.1';
var dhcp_dns1_curr = '';
var dhcp_dns2_curr = '';
var dhcp_wins_curr = '';
if(yadns_support){
var yadns_enable = '0';
var yadns_mode = '1';
}john9527
Part of the Furniture
If you log in to the router via telnet/ssh, the nvram variable to edit is 'dhcp_staticlist'Is there a way to change this setting without using the GUI, so I can fix it?
do
nvram show | grep dhcp_staticlist
highlight the result with the mouse and then right click to copy it to the command line....insert 'nvram set' (without the quotes) at the beginning of the line and then move the cursor to delete the offending '
EDIT: You'll also need to enclose the data in double quotes (after the equal sign and at the end of the line)
Last edited:
I just tested it with the same setup as you mention and it's working fine for me.
Keep in mind that DNS lookups get cached both by the OS and by the web browser. You have to either try a different browser, or make sure you do shut down your browser and restart it before testing with a different DNS setup.
I did try these and other things without success.
Then I gave up and did a factory reset, set up everything again and voilà! It's all good now.
Thanks for the help anyway!
thegorilla
Occasional Visitor
If you log in to the router via telnet/ssh, the nvram variable to edit is 'dhcp_staticlist'
do
nvram show | grep dhcp_staticlist
highlight the result with the mouse and then right click to copy it to the command line....insert 'nvram set' (without the quotes) at the beginning of the line and then move the cursor to delete the offending '
EDIT: If you have any spaces in your names you'll also need to enclose the data in double quotes (after the equal sign and at the end of the line)
Thank you!!!!! This worked perfectly!! It fixed all 3 screens, which now load with no errors.
I had to encapsulate the value in double quotes, even though there were no spaces because I got an error "-sh: syntax error: unexpected redirection" if I did not.
I tested spaces, dashes and underscores, all did not break the page. It appears that the unescaped single quote is what kills it. I know not to use it myself , but it might be a candidate for 'protecting the user from themselves'.
Thank you all for your fast response and excellent troubleshooting!
It's a router, not a computer. You will need to stop running whatever you are running on it that requires so much memory.
Turns out the real issue is default setting for
Code:
/proc/sys/vm/overcommit_memory
Code:
echo 1 > /proc/sys/vm/overcommit_memoryAnd overcommit ratio is set to very low at 50%, better
Code:
echo 400 > /proc/sys/vm/overcommit_ratioOf interest is that large values for /proc/sys/vm/dirty_ratio (50) and /proc/sys/vm/dirty_background_ratio (20) actually caused a system reset more than once...but these are not that much higher compared to linux defaults. Anyone who wants to experiment, read this first: https://www.kernel.org/doc/Documentation/sysctl/vm.txt
Hoping Asus would realize their routers have too little ram to even run downloadmaster properly (seeding eats up ram, more than 256MB is quickly needed), not to talk about all the other stuff they keep on adding...and ram is cheap. Just put an empty sodimm socket in there, many people have leftover 1-4GB modules from upgrading laptops etc.
Last edited:
john9527
Part of the Furniture
Yes...sorry about that....I forgot about the use of < and > as field separators. Glad you tried the double quotes. Good to hear that it got things running!I had to encapsulate the value in double quotes, even though there were no spaces because I got an error "-sh: syntax error: unexpected redirection" if I did not.
pietjepuk100
Regular Contributor
VPN => openVPN clients => Redirect Internet traffic => Rules for routing client traffic through the tunnel
Thanks, that worked for me!
thegorilla
Occasional Visitor
No worries, the fix was straightforward and intuitive once you explained the commands.Yes...sorry about that....I forgot about the use of < and > as field separators. Glad you tried the double quotes. Good to hear that it got things running!
joegreat
Very Senior Member
Hi,Turns out the real issue is default setting for= 2, meaning never overcommit memory. Changing this to 1 byCode:/proc/sys/vm/overcommit_memorylets swap work. 1GB is not too much, since even mkfs.ext3 for a large filesystem (tb's) will need at least 400MB memory.Code:echo 1 > /proc/sys/vm/overcommit_memory
Thank you for this research and hints for the better memory management.
This add-on to my seetings here helps to reduce the pressure on memory usage and to avoid the "race condition" I was facing in the original posting.
With kind regards
Joe
Last edited:
Korumera
Occasional Visitor
Got an issue with the vlan's id's. When I try to set the ID to 6 at LAN > IPTV (manual) it won't change it at all. When I apply the change and go to Tools and scroll down it stays on VLAN ID 2 and when I check it with robocfg show it says VLAN 2 also.
I've tried to change it with robocfg, but that change won't stick and don't have a clue how to do that anyone else that as a problem with this (i'm using the software on a AC87u.
anyone else that as a problem with this (i'm using the software on a AC87u.
Thanks in advanced.
I've tried to change it with robocfg, but that change won't stick and don't have a clue how to do that
Thanks in advanced.
RussellInCincinnati
Senior Member
You appear to have some specialized knowledge that the writers of the Asus router code do not? That the Asus setting for overcommit_memory is a mistake?Turns out the real issue is default setting for= 2, meaning never overcommit memory. Changing this to 1 byCode:/proc/sys/vm/overcommit_memorylets swap work...Code:echo 1 > /proc/sys/vm/overcommit_memory
Hoping Asus would realize their routers have too little ram to even run downloadmaster properly...and ram is cheap...
Also interested in why anyone would want to run "downloadmaster" on a WiFi router that only has 256 megabytes of memory. Isn't downloadmaster something that you could run on a $75 dollar used NAS box for example?
@RMerlin I am an Android Kernel developer over at XDA for the Nexus 4 & 5, and I was wondering if you could implement Kernel Same Page Merging as well as zram that will further optimize memory consumption on these routers. Also I wonder how fiops io scheduler would perform on these routers. Let me know what you think, I think we can further optimize the performance on the ARM based routers, and its possible some Android kernel patches may be compatible.
You appear to have some specialized knowledge that the writers of the Asus router code do not? That the Asus setting for overcommit_memory is a mistake?
Asuswrt does not support a swap file by default, so there would be no real reason for them to have a different value on than the value of 2 it currently uses. "2" means "never overcommit more than you have available", which would be the logical configuration to use.
In fact, it should still allow the use of swap memory, so I'm not sure why the poster needed to set it to 1 for his swap to work. Personally, I would rather look at what swapiness value he has set for his router. Setting over_commit to "1" is a bad idea - it tells the kernel to NEVER refuse any malloc() call, even if there's no longer enough memory available. This can lead to router instability and crashes once you exhaust the available swap.
In short: it's not a solution, it's a workaround, and not a very good one. Asus's choice of "2" is the correct one.
Recommend reading: http://www.win.tue.nl/~aeb/linux/lk/lk-9.html
@RMerlin I am an Android Kernel developer over at XDA for the Nexus 4 & 5, and I was wondering if you could implement Kernel Same Page Merging as well as zram that will further optimize memory consumption on these routers. Also I wonder how fiops io scheduler would perform on these routers. Let me know what you think, I think we can further optimize the performance on the ARM based routers, and its possible some Android kernel patches may be compatible.
My hands are tied with the kernel, because any changes will potentially cause the kernel symbol versions to change, which will in turn prevent the router from loading the closed source modules, such as the wireless driver, the NTFS filesystem driver, or the Trend Micro DPI engine.
For instance, Asus/Broadcom kept a debug setting enabled in relation to the slab allocator. I can't even disable that, because the kernel symbol changes prevented the Tuxera FS driver from loading.
Also keep in mind that Broadcom uses a quite old kernel (2.6.36.4). A lot of features are not available yet in this version.
I have policy routing set up where only one client IP goes through the VPN tunnel. It works well. The problem I am having is with DNS. When I set the DNS to "exclusive" it works just as advertised and I have no DNS leak for the client, *but* at this point all my clients start using the DNS of the VPN service (which is not what I want). Note the non-VPN clients do not use the VPN tunnel, they just start using the VPN DNS service. Is this intentional? I would like to have the normal non-vpn clients use the DNS I specify in the WAN settings and have the policy based VPN client use the DNS of the VPN service.
Still, a great release. Love it and good job.
Still, a great release. Love it and good job.
I have policy routing set up where only one client IP goes through the VPN tunnel. It works well. The problem I am having is with DNS. When I set the DNS to "exclusive" it works just as advertised and I have no DNS leak for the client, *but* at this point all my clients start using the DNS of the VPN service (which is not what I want). Note the non-VPN clients do not use the VPN tunnel, they just start using the VPN DNS service. Is this intentional? I would like to have the normal non-vpn clients use the DNS I specify in the WAN settings and have the policy based VPN client use the DNS of the VPN service.
Still, a great release. Love it and good job.
Not much I can do about this. The router uses the same DNS for all queries, regardless on how they are being routed afterward. dnsmasq has no way of knowing if a specific query is from a VPN client or a regular client.
I have policy routing set up where only one client IP goes through the VPN tunnel. It works well. The problem I am having is with DNS. When I set the DNS to "exclusive" it works just as advertised and I have no DNS leak for the client, *but* at this point all my clients start using the DNS of the VPN service (which is not what I want). Note the non-VPN clients do not use the VPN tunnel, they just start using the VPN DNS service. Is this intentional? I would like to have the normal non-vpn clients use the DNS I specify in the WAN settings and have the policy based VPN client use the DNS of the VPN service.
Still, a great release. Love it and good job.
One thing you could try if really you are worried about your ISP logging your DNS queries (considering the sheer volume of queries an ISP must see I personally doubt they'd do that, for performance reason to be honest) is to leave the VPN client to "relaxed", but configure a DNSFilter rule to force your routed clients to a specific DNS.
xundas
New Around Here
I finally managed to track it down. It's not a bug in the firmware, it's the ovpn config you are importing that's telling the router NOT to run the proper cleanup script at exit time.
Remove the following line from your custom config field:
Code:explicit-exit-notify 1
Should be fine after that.
I tried but it seems that there was no difference. Please note that for every test that I am doing, I am applying the changes (obviously) and rebooting the router, and while it reboots I disable the wlan0 interface in my linux notebook, so (hopefully) cleaning up some cache that may interfere.
I was reading about this explicit-exit-notify and it seems(if I understood correctly!) that this has to do with a forced signal to the server indicating that I am disconnecting (They limit the amount of simultaneous connections that a given username can do, therefore a "hanging" connection would be bad..)
I really don't know much about troubleshooting DNS connections, I try using dig for somethings but I would really like to be able to identify which DNS server I am using...
Thanks again for your help!!
Similar threads
- Replies
- 194
- Views
- 41K
- Replies
- 101
- Views
- 19K
- Replies
- 113
- Views
- 17K
- Locked
- Replies
- 70
- Views
- 13K
- Locked
- Replies
- 53
- Views
- 7K
Similar threads
Similar threads
-
Asuswrt-Merlin Change Operation Mode Fails via NVRAM Variables
- Started by garycnew
- Replies: 15
-
robocfg Not Available on Asus GT-AXE11000 (Asuswrt-Merlin 388.8_4)?
- Started by garycnew
- Replies: 9
-
-
-
Can i install flask on asuswrt-merlin on usb with pip?
- Started by Sandman1
- Replies: 0
-
[ANNOUNCEMENT] Asuswrt-Merlin 386_x devices are no longer supported
- Started by RMerlin
- Replies: 76
-
Release Asuswrt-Merlin 3006.102.3 is now available for WIfi 7 devices
- Started by RMerlin
- Replies: 113
-
Solved NextDNS stock asuswrt vs Merlin, caching difference?
- Started by Zuikkis2
- Replies: 1
-
-
Beta Asuswrt-Merlin 3006.102.3 beta is now available for Wifi 7 devices
- Started by RMerlin
- Replies: 53
Latest threads
-
-
-
Asus XT8 WAN port speed stuck at 100Mbps
- Started by Silolis
- Replies: 3
-
3006.102.3 RT-BE88U as WireGuard client. No Internet connection after reboot.
- Started by biker3
- Replies: 0
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!

